Question: I need a secure way to transfer sensitive data to clients, can you recommend a solution that verifies recipient identities and ensures no trace is left behind?
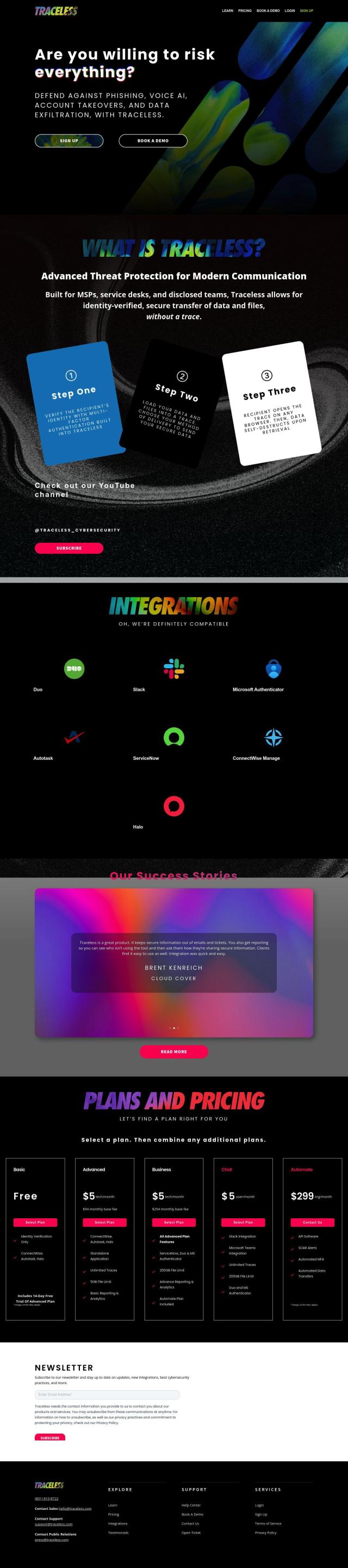
Traceless
If you need a way to send sensitive information to customers while ensuring recipients are who they say they are and that there's no record of the exchange, Traceless could be the ticket. It's good for managing service providers, service desks and disclosed teams. It verifies recipients with multi-factor authentication, transfers data that automatically deletes itself, and grants access through any browser. With integrations with ConnectWise, Autotask and ServiceNow, Traceless helps you keep communications and data transfers secure and free from cyberattacks and data breaches.
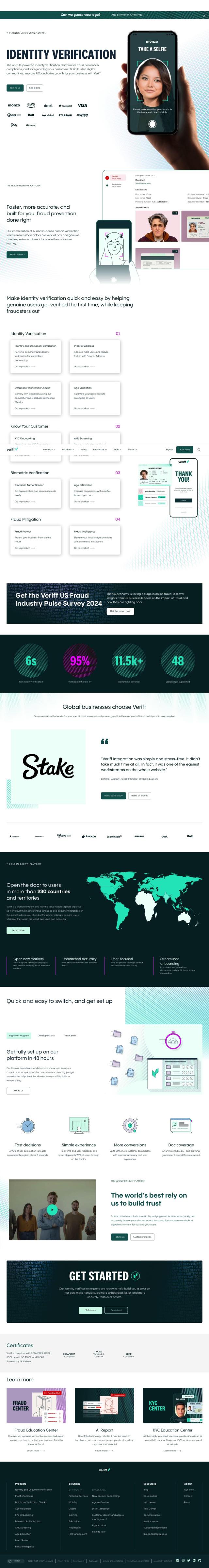
Veriff
Another contender is Veriff, an all-in-one identity verification system that can help you fight fraud and comply with regulations. Veriff uses a combination of AI and human verification teams to ensure a smooth customer experience for identity and document verification, KYC onboarding and AML screening. It supports more than 11,500 government-issued IDs from 230+ countries and territories, so it's a global solution for businesses. The system is heavily regulated, with compliance with CCPA/CPRA, GDPR and WCAG Accessibility Guidelines, so it's good for financial services, iGaming and other industries.
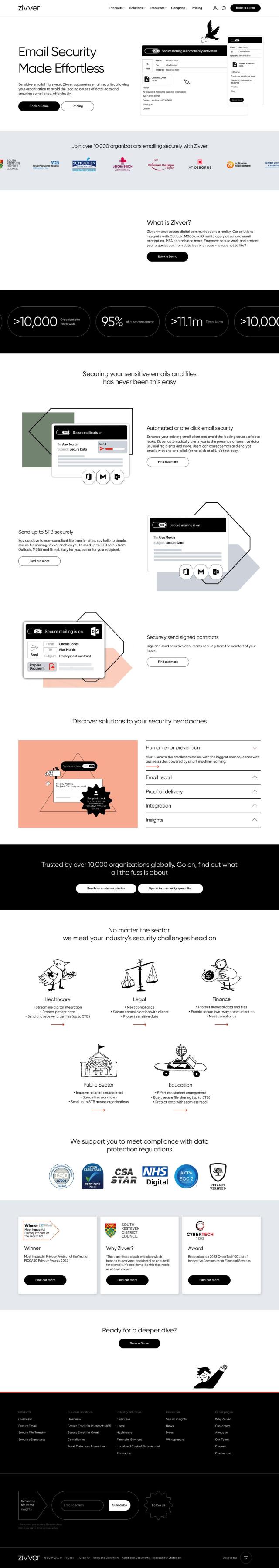
Zivver
If you need a secure email service, Zivver offers strong email encryption and multi-factor authentication controls that work with Outlook and Gmail. It also offers features like automated or one-click email security, secure file transfer, proof of delivery and exportable insights into company-wide usage and blocked breaches. Zivver is designed to comply with regulations like GDPR, HIPAA, DORA and NIS2, so it's good for healthcare, financial services and education.
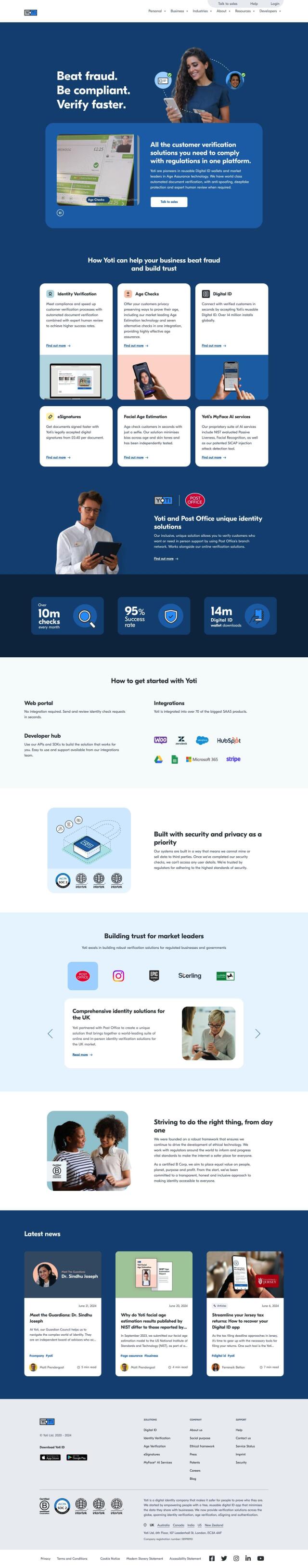
Yoti
If you need a digital identity service that can do a lot of things, check out Yoti. It offers identity verification, age checks, digital IDs, eSignatures and facial age estimation. The service uses automated document verification, human review and AI-based services to deliver high success rates and minimize bias. Yoti's systems are designed with security and privacy in mind, encrypting customer data and offering integration with more than 70 popular SAAS products through APIs and SDKs. That makes it a good option for businesses that want to verify customers securely and quickly.