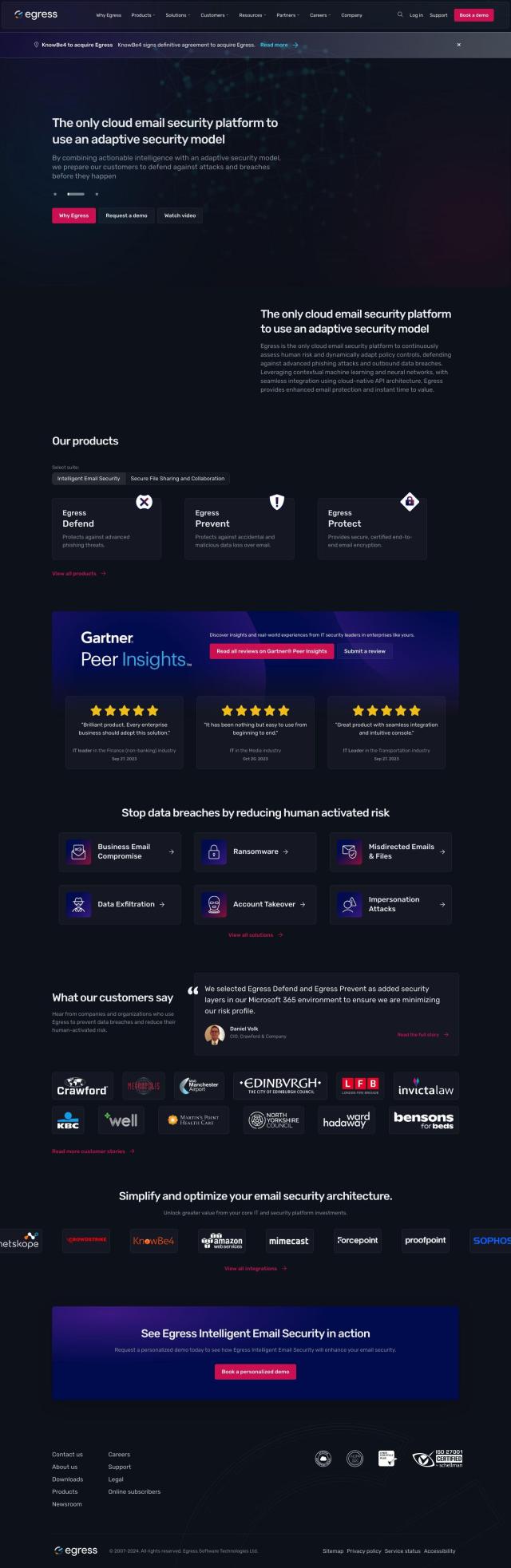
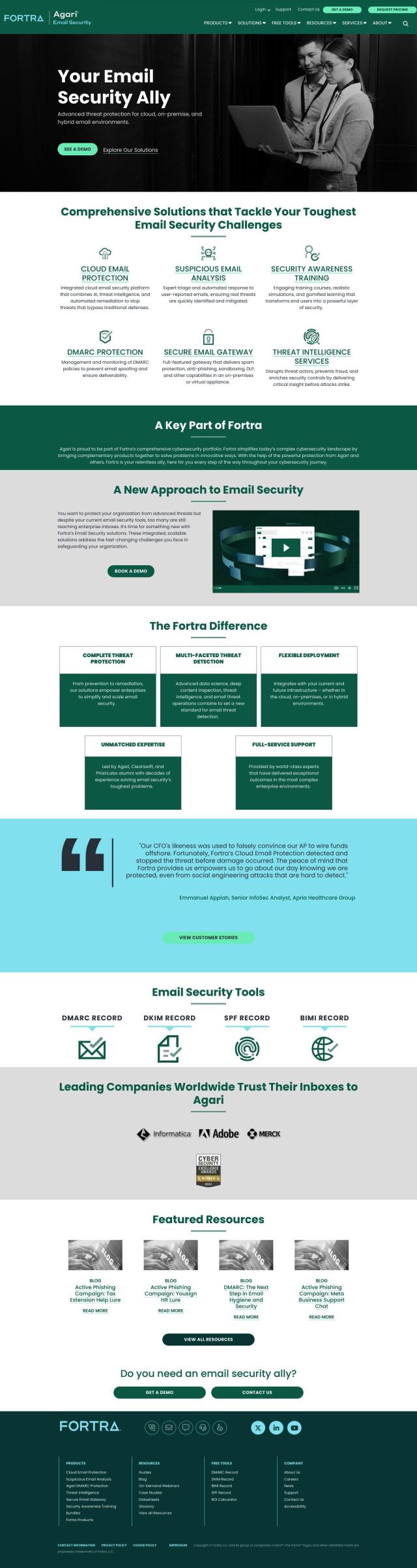
Tessian uses AI to stop phishing attacks, email data theft and misdirected emails. It cuts risk and saves time by spotting and blocking sophisticated email attacks that evade traditional security systems.
Tessian is designed to address a top concern for security executives, since email-based attacks are the top concern. The company says it's stopped more than 250,000 BEC (Business Email Compromise) attacks reported to the FBI since 2013, with an average cost of $4.5 million per attack.
Tessian's AI uses behavioral, content and threat network analysis to spot and block email-based attacks like BEC, account takeovers and impersonation attacks. That means it can stop sensitive data from being sent to the wrong people or from being stolen through email. It also offers contextual warnings that help people learn how to evaluate risks and spot potential problems.
Among its features are:
- Defend: AI-based email threat defense against sophisticated attacks like BEC and domain spoofing.
- Protect: Blocking data loss through email with behavioral analysis to stop employees from making mistakes.
- Respond: Quick search and remediation for email incidents, including automated removal of end-user reported threats.
- Coach: Helping people make better security decisions with contextual warnings.
Tessian works with Microsoft and Google email services and can be deployed in minutes through native API integration. The service is intended to improve the security of cloud email services, offering a more complete response to email security challenges.
Prospective customers can schedule a personalized demo to learn how Tessian can help protect against advanced phishing attacks and protect sensitive data on email. Tessian is one of several tools businesses can use to try to improve their email security without disrupting operations.
Published on July 6, 2024
Related Questions
Tool Suggestions
Analyzing Tessian...