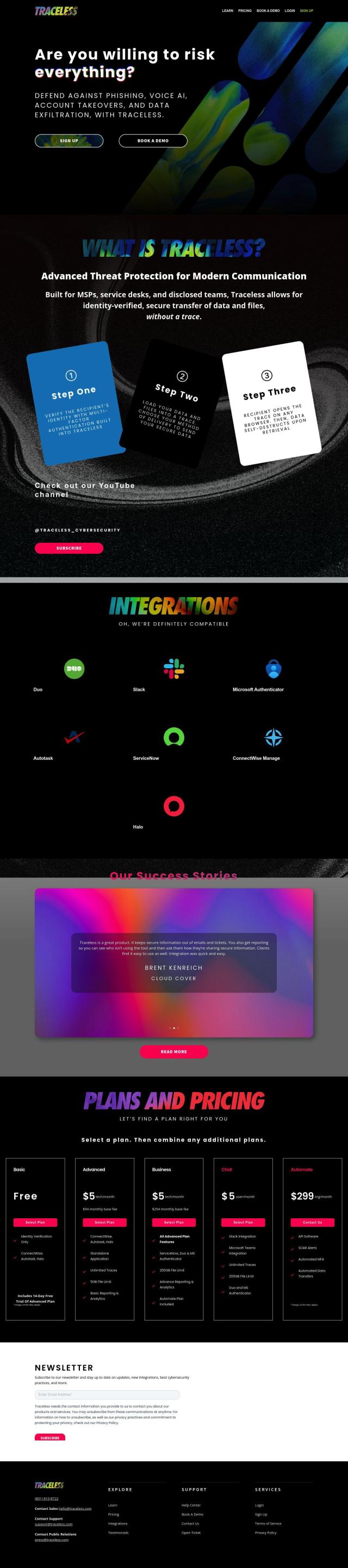
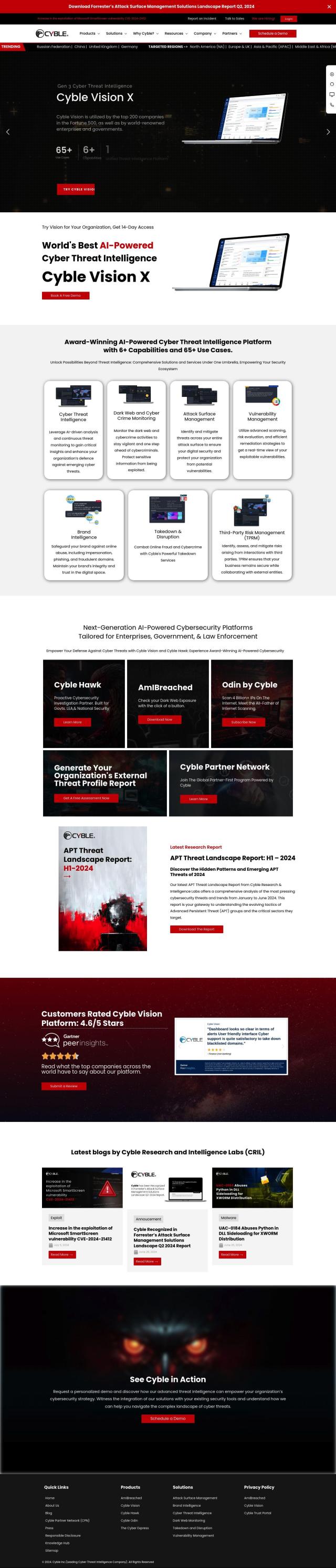
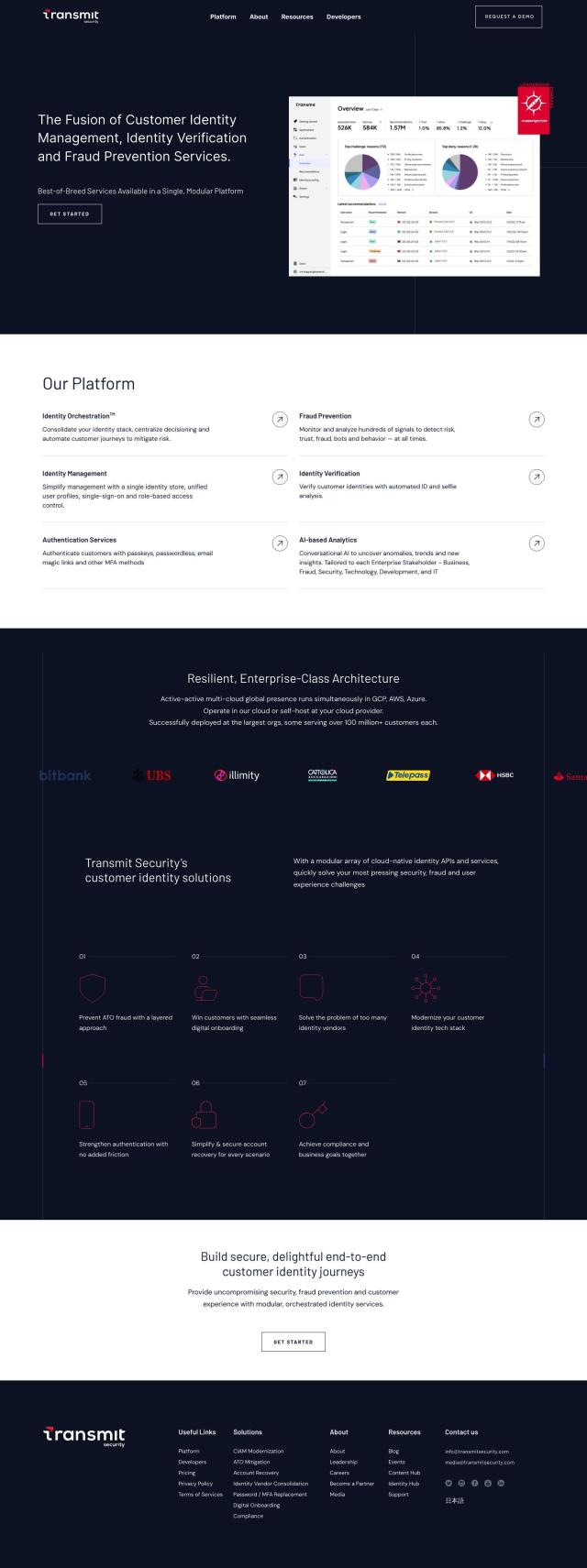
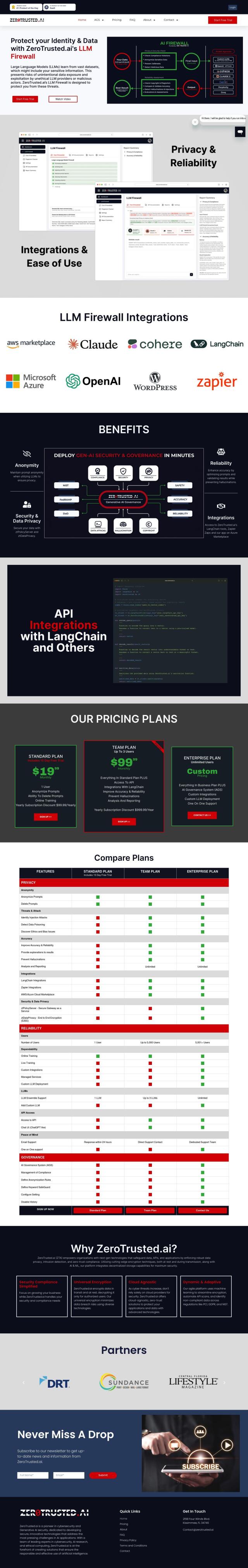
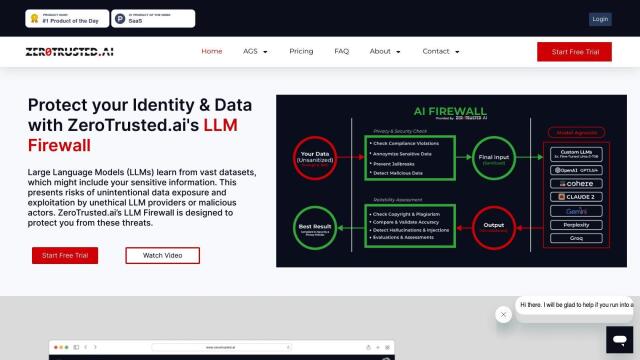
Varonis
If you're looking for something to replace Traceless, Varonis has a more complete automated data security offering. It includes data discovery and classification, threat detection and policy automation across many cloud and on-premises systems. It spans many applications and cloud services like Microsoft 365 and Google Workspace, and offers automated results, real-time visibility and proactive threat detection.
WatchGuard
Another option is WatchGuard, which offers a unified cybersecurity platform with network, endpoint and identity security products. Its centralized security management and threat detection abilities, along with products like AI-powered NDR security and managed detection and response, make it a good option for companies of all sizes.
Tessian
If you're more interested in email security, Tessian could be a good option. It uses AI-powered behavioral, content and threat network analysis to spot and block sophisticated email attacks like phishing and email data theft. Its integration with Microsoft and Google email systems through native API integrations offers a complete solution to email security problems without disrupting operations.


BeyondTrust
Last, BeyondTrust is an intelligent identity and access security platform that offers a 360-degree view of all identities, privileges and access. It offers features like privilege transparency, secure remote access and a zero-trust approach to identity security, and integrates with many other tools to offer centralized control and visibility across your entire identity estate.