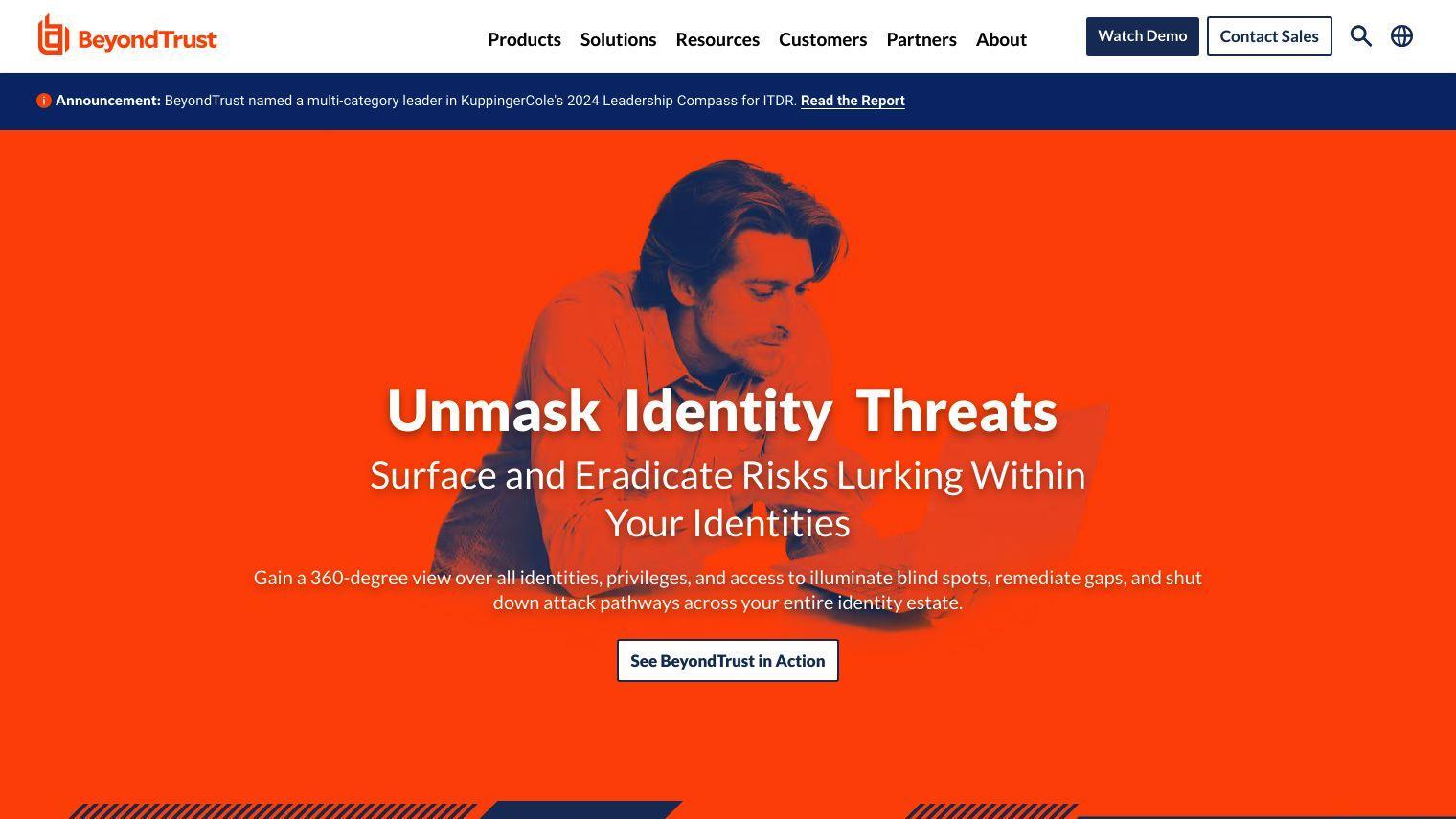
BeyondTrust is a comprehensive platform for intelligent identity and access security. It safeguards identities, prevents threats and offers dynamic access with a 360-degree view of all identities, privileges and access. This helps organizations uncover blind spots, fix gaps and eliminate attack vectors across their entire identity estate.
BeyondTrust provides several key capabilities to help protect identity:
- Full Privilege Transparency: Discover and protect users and machine identities, secrets, devices and access across all environments.
- Secure Remote Access: Provide VPN-free secure access to any infrastructure with just-in-time access controls.
- Detect and Respond to Identity Threats: Leverage advanced discovery, intelligence and analytics to identify and take down identity-based attacks.
- Protect Privileges at Scale: Manage and automate just-in-time access and modern identity governance across cloud estates.
The platform integrates with a wide range of tools and systems to support a zero-trust approach to least privilege and intelligent threat detection. This ensures unified control and visibility across the entire identity estate.
BeyondTrust is well-suited for a variety of use cases, including:
- Cloud Access: Identity-based, cloud-native access to infrastructure.
- Cloud Security: Protect business with proven PAM solutions for the cloud.
- Compliance: Meet audit and compliance requirements out-of-the-box.
- Cyber Insurance: Meet foundational security standards required by issuers.
- Digital Transformation: Build security into the foundation of digital transformation programs.
- Endpoint Security: Protect endpoints from known and unknown threats.
- Identity Threat Detection & Response: Prevent, detect and neutralize identity-based threats.
- Operational Technology: Enable secure remote access to critical operational technology systems.
- Ransomware: Make environments inhospitable to ransomware and other malware.
- Secure Remote Access Management: Secure remote access for vendors and employees.
- Service Desk Efficiency: Reduce tickets, improve incident resolution times and lower IT costs.
- Workforce Passwords: Secure and audit employee passwords at scale.
- Zero Trust: Implement zero trust security controls.
BeyondTrust has been named a Leader in the Gartner Magic Quadrant for Privileged Access Management five times, and a Leader in the Forrester Wave for Privileged Identity Management and KuppingerCole Identity Threat Detection & Response Leadership Compass.
To learn more about BeyondTrust, interested parties can schedule a demo to receive detailed product, pricing and technical information directly from the experts.
Published on June 23, 2024
Related Questions
Tool Suggestions
Analyzing BeyondTrust...