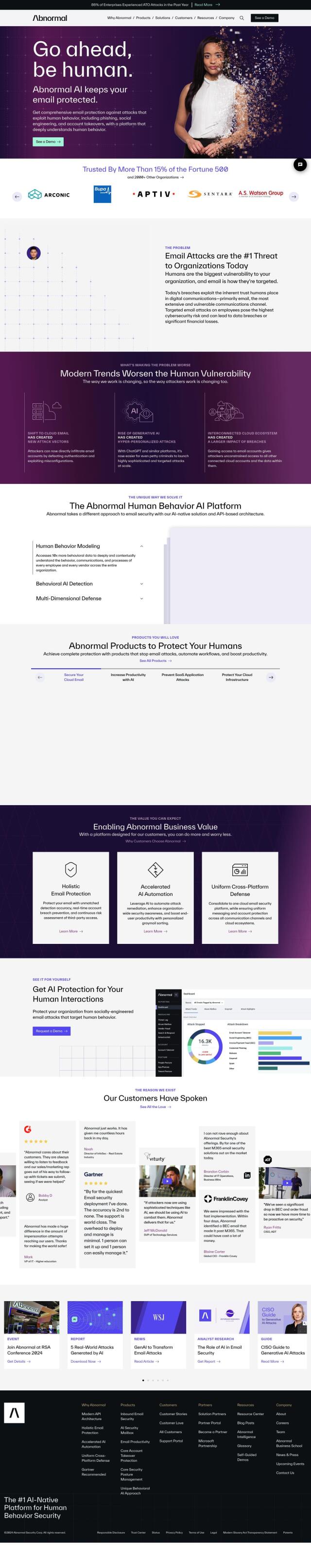
Seraphic
If you're looking for a Menlo Security alternative, Seraphic is worth a serious look. It turns any browser into an enterprise browser with a layer of abstraction between the JavaScript code and the JavaScript engine. The platform supports multiple browsers, including Chrome, Safari, Edge, Firefox and Electron-based apps. Seraphic blocks zero-day exploits, phishing and web app attacks, and protects data and blocks malware in many different environments.
Conceal
Another good alternative is Conceal, a lightweight browser extension that uses AI technology to block web-based threats like phishing and malware. It offers real-time threat analysis and advanced phishing detection, making it a good option for IT staff and security professionals. Conceal also protects privacy since it doesn't upload sensitive data and has a relatively low subscription price, so it's a good option for small and medium-sized businesses.


SentinelOne
If you're looking for something more comprehensive, check out SentinelOne. It's an all-in-one endpoint, cloud, identity and data security platform with more advanced features like next-gen EPP, EDR and XDR tools. SentinelOne offers real-time cloud workload protection, identity threat detection and 24/7 threat hunting, so it's good for companies of all sizes. Its strong security features and industry accolades mean it's a good option for reducing risk and increasing efficiency.