Menlo Security
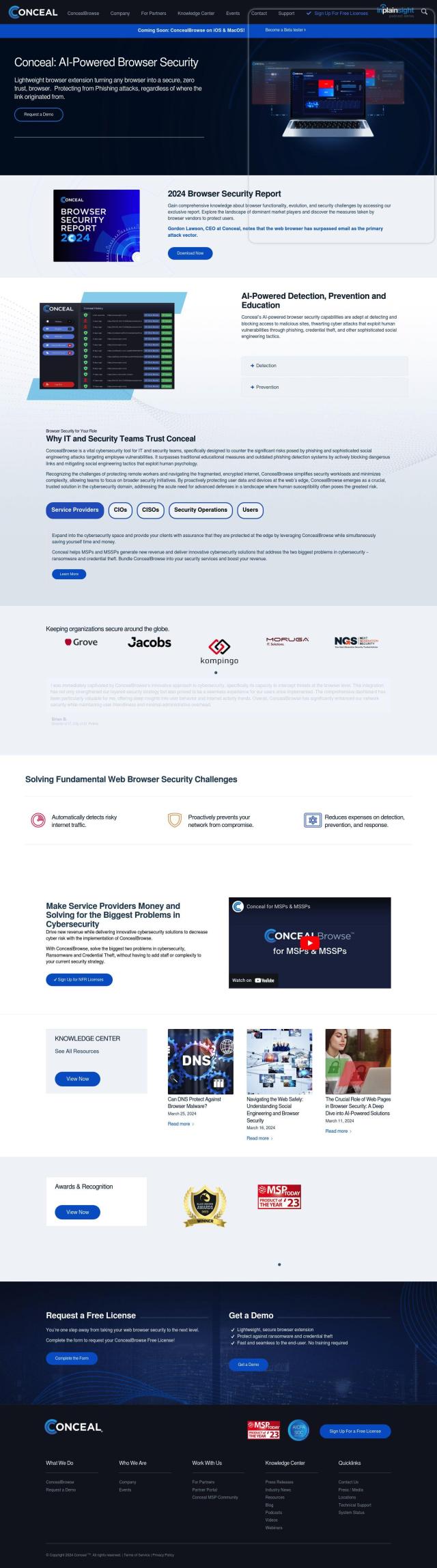
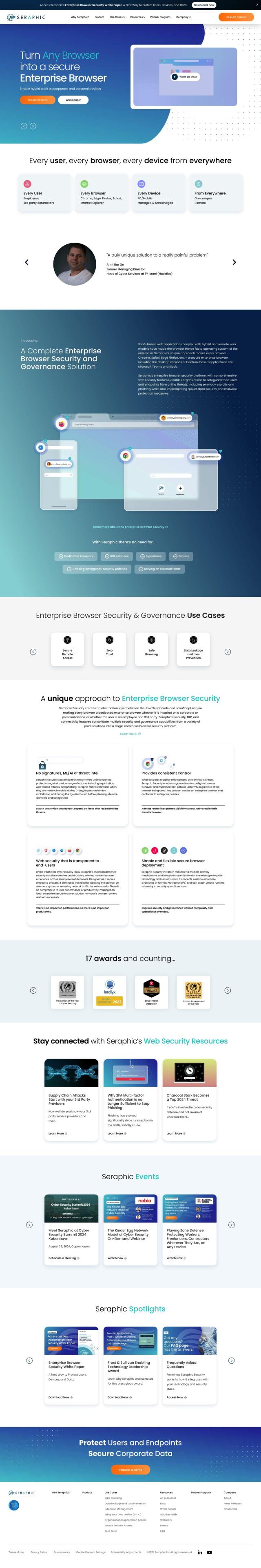
If you're looking for a Conceal alternative, Menlo Security has a powerful cloud-based security foundation that blocks phishing and malware attacks. Its HEAT Shield and Browser Posture Manager offer zero-hour phishing protection and evasive ransomware prevention, too, so it's a good option for protecting your digital assets.


Darktrace
Another good option is Darktrace, which uses Self-Learning AI to detect and respond to in-progress cyber attacks, including ransomware and phishing. The platform learns from an organization's operations and offers real-time threat detection and automated response, so it's adaptable and good at keeping up with evolving cyber threats.


Lookout
If you're focused on mobile security, Lookout has a cybersecurity platform with features like real-time breach detection, cloud data loss prevention and a secure web gateway. Its defense-in-depth approach and AI-powered data set means strong mobile and cloud security, too, so it's a good alternative if you need to protect data in many apps.


Forcepoint
Last, Forcepoint has a broad security platform with several products, including Cloud DLP, Data Security Posture Management and a Secure Web Gateway. Its cloud-native platform, Forcepoint ONE, offers data-first SASE, and its global coverage with 99.99% uptime means your apps, devices and locations are always protected.