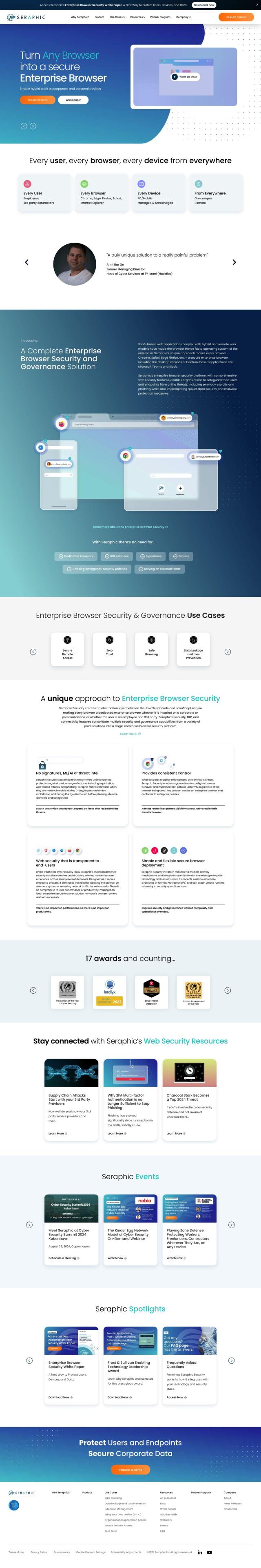
Question: Is there a way to replace VDI with a more secure and efficient solution for remote access to applications?


Menlo Security
If you're looking for a more secure and efficient way to reach apps beyond VDI, Menlo Security is another good option. Its Enterprise Browser is a cloud-based service that blocks phishing and malware attacks by transforming any browser into an enterprise browser. It's got features like zero-hour phishing protection, evasive ransomware prevention and generative AI that's protected from abuse, so it's a good way to protect against today's web-based zero-day exploits and evasive attacks.


BeyondTrust
Another good option is BeyondTrust, an intelligent identity and access security platform. It offers a 360-degree view of all identities and privileges, protecting against identity-based attacks and delivering dynamic access. The platform also offers secure remote access management and integrates with other tools to help you adopt a zero-trust approach, so it's a good way to lock down remote access.


CyberArk
If you're looking for an identity security system that covers all your bases, CyberArk is worth a look. It offers secure access to any device, anywhere, with artificial intelligence-powered security features like Secure Single Sign-On and Adaptive Multi-Factor Authentication. CyberArk also offers advanced identity management and orchestration, so you can move to a Zero Trust system without as much hassle.


Zero Networks
Last, Zero Networks offers an automated microsegmentation and remote access service. It marries the speed of VPNs with the security of Zero Trust Network Access, offering automated network segmentation and multi-factor authentication. It's good for limiting network access to sensitive assets, stopping lateral movement and ransomware attacks.