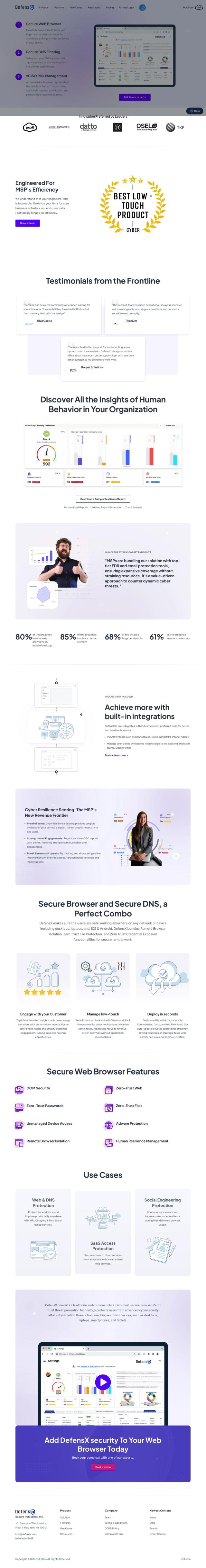
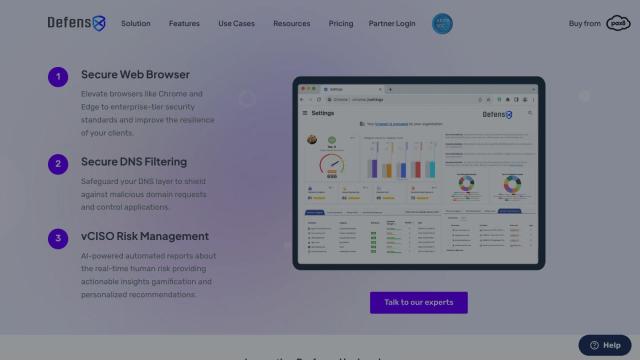
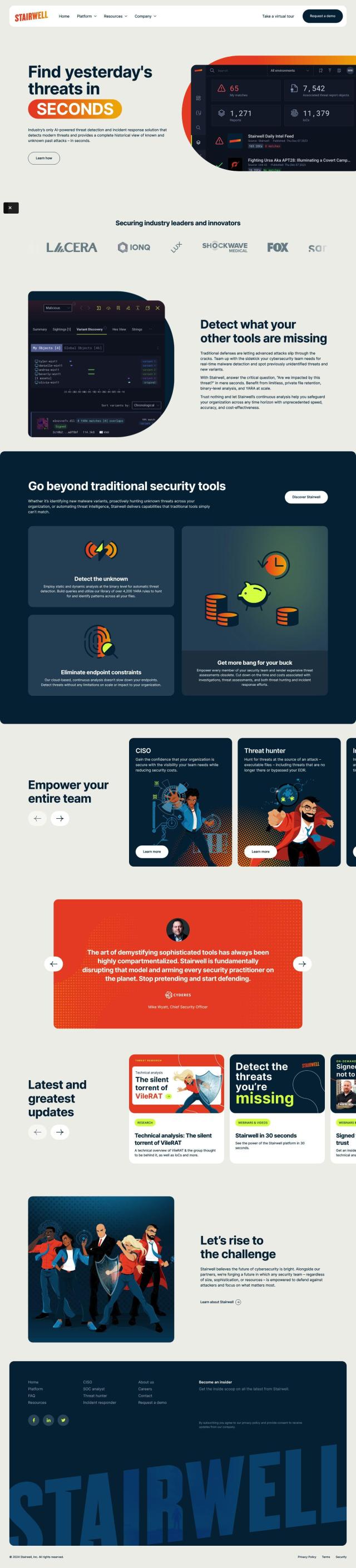
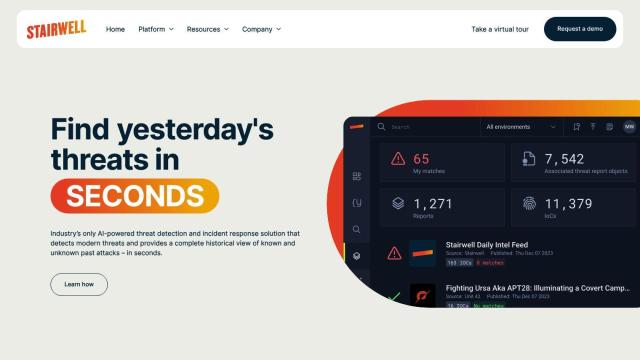
Question: How can I reduce the risk of malware infections on my organization's endpoints without impacting user experience?

Deep Instinct
To protect your organization's endpoints from malware infections without disrupting users, you could also look at Deep Instinct. The company's platform is designed to take a prevention-first approach using deep learning to identify and stop unknown ransomware and malware attacks. With a 96% user recommendation rate and very low false positive rates, it's designed to offer strong protection across a range of operating systems, including Windows, macOS, Android and Linux.
ReasonLabs
Another option is ReasonLabs, which offers a full endpoint protection and response solution. With multilayered machine learning technology, it thwarts advanced malware attacks with features like behavioral analysis, endpoint detection and response, and real-time malware protection. The suite is designed to be easy to use and accessible, making it a good option for home users and businesses.


Menlo Security
If you prefer a cloud-based option, Menlo Security offers an Enterprise Browser solution that protects against phishing and malware attacks on any browser and device. With features like zero-hour phishing protection, evasive ransomware prevention and secure generative AI, it offers secure browsing without performance impact. The platform is well suited for hybrid enterprises that need to protect user access and data across multiple environments.


Cybereason
Last, Cybereason offers an AI-Driven XDR platform that combines NGAV, EDR and MDR to provide predictive prevention, detection and response to modern ransomware and sophisticated attacks. With features like MalOp Detection, NGAV and Endpoint Controls, it automates attack prediction and response, providing a comprehensive defense solution for enterprises of all sizes.