Question: Can you recommend a platform that automates device management and compliance for employee devices?
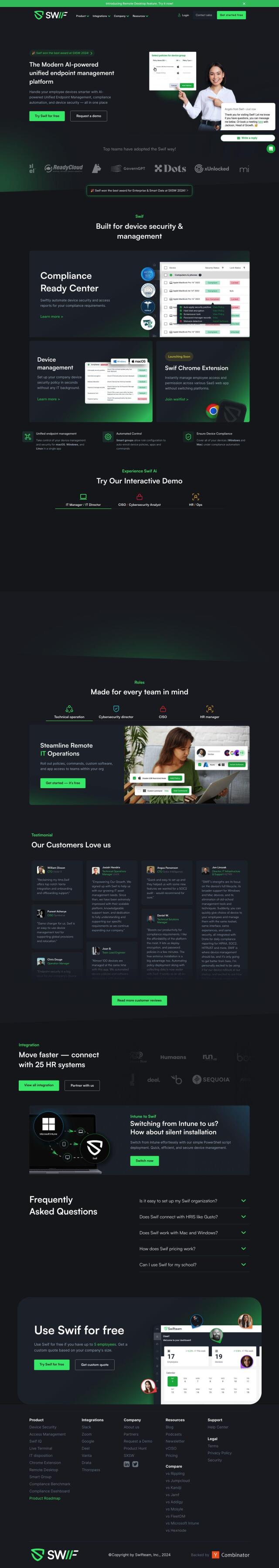
Swif
If you're in the market for a platform to automate device management and compliance for employee devices, Swif is worth a look. It's a GenAI-powered unified device management and compliance automation platform that automates employee device management while keeping them secure and compliant. Swif includes tools like a Compliance Ready Center for automating security and access reports, unified endpoint management for macOS, Windows and Linux devices, and a Chrome extension for employee access and permissions management across SaaS web apps. It also integrates with popular tools like Slack, Zoom, Google and Vanta, and offers an interactive demo and a free trial for up to 5 employees.


Forescout
Another option is Forescout, a broad cybersecurity platform that discovers, protects and ensures compliance of all managed and unmanaged connected assets. It includes automated assessment, segmentation and enforcement of proactive and reactive controls for network security. Forescout serves multiple industries and offers features like threat detection and response, asset inventory, and real-time monitoring, making it a good fit for security professionals and IT teams looking to improve their cybersecurity posture across a range of asset types.
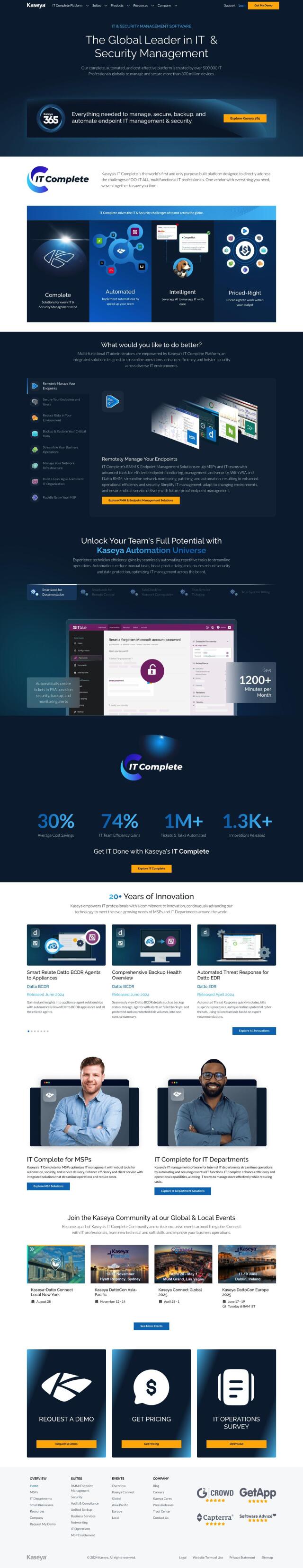
IT Complete
If you're looking for a more comprehensive solution, check out IT Complete from Kaseya. This platform is designed to manage and secure IT and security operations, and is used by more than 500,000 IT professionals to manage 300 million devices. IT Complete includes advanced RMM and endpoint management, comprehensive security, audit and compliance, and business operations automation. It's designed to improve security and data protection, and provide cost savings and productivity gains for IT professionals and MSPs.


BeyondTrust
Last, BeyondTrust offers a powerful platform for intelligent identity and access security. It provides a 360-degree view of all identities, privileges and access to help prevent threats. With features like secure remote access, dynamic access management, and threat detection, BeyondTrust helps organizations adopt a zero-trust approach and meet compliance requirements. Its advanced features and capabilities have been recognized in leading industry reports.