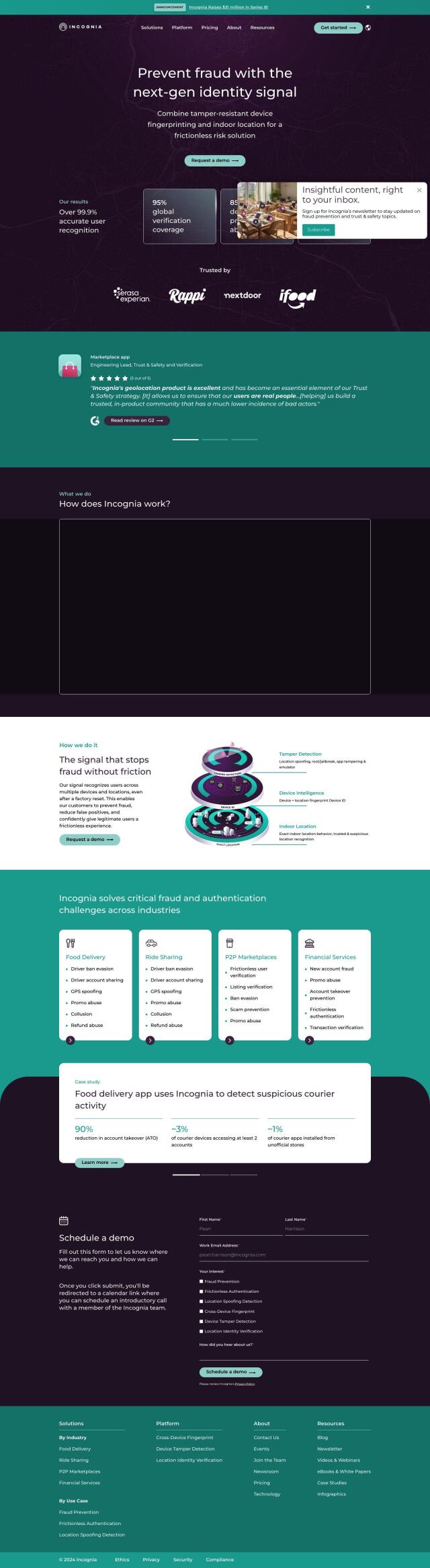
Question: Show me a comprehensive identity security solution that can help reduce account-takeover fraud and protect our organization's identity lifecycle.
HYPR
For a broad identity security solution to help cut account-takeover fraud and protect your organization's identity life cycle, HYPR is a strong contender. HYPR helps you identify, prevent and remove identity-related risk for workforce and customer identities, with continuous risk and policy orchestration, strong passwordless authentication and automated identity verification. HYPR has cut account-takeover fraud by 98.4% and has more than 25 million users deployed, is certified at high assurance levels and has been adopted by major companies.
Transmit Security
Another strong contender is Transmit Security, which offers a cloud-native suite of services for security, fraud prevention and customer experience management. It includes identity orchestration, fraud prevention with hundreds of signals, and AI-based analytics for anomaly detection. It's highly scalable and runs in multiple cloud environments, making it a good choice for companies that want to modernize their customer identity tech stack and cut account takeover fraud.


CyberArk
For a broader identity security and access management system, you might want to look at CyberArk. CyberArk protects all identities, human and machine, with secure Single Sign-On (SSO), Adaptive Multi-Factor Authentication (MFA) and life cycle management. The system includes intelligent privilege controls, flexible identity automation and strong endpoint and cloud security, and can help companies move to a Zero Trust identity security posture.


RSA
Last, RSA offers a broad security-first identity system with automated identity intelligence, authentication, access, governance and life cycle capabilities. RSA offers multiple secure authentication options, including anomaly detection and machine learning-based risk assessment, and offers single sign-on and self-service options. The system is good for high-security organizations in many industries, and RSA offers customized products and professional services to meet specific security requirements.