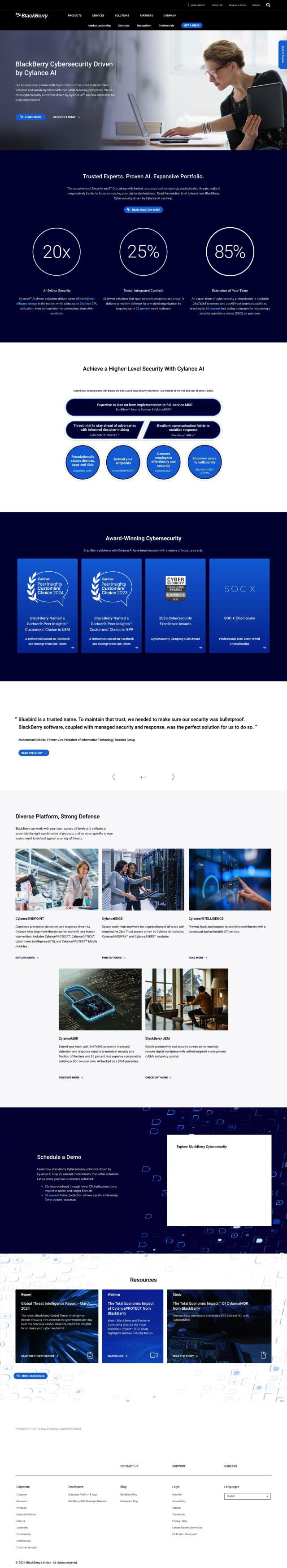
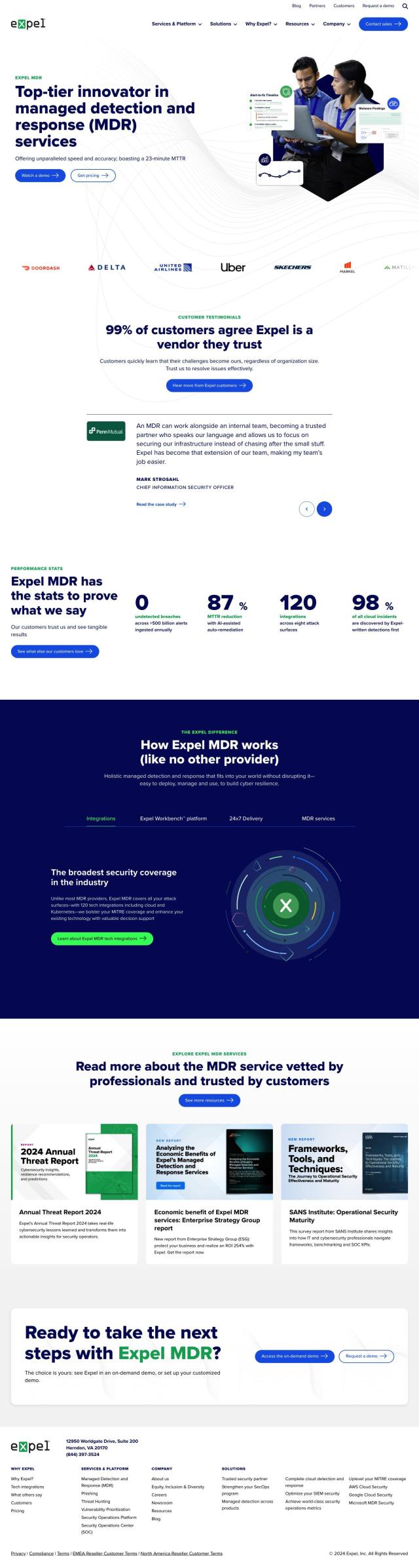
Question: Is there a platform that uses AI to automate threat removal and has a high success rate?


Axur
If you're looking for a platform that uses AI to automate threat removal with a high success rate, Axur is a great option. Axur provides a comprehensive cybersecurity solution using artificial intelligence to monitor and remove threats across the Deep and Dark Web. It has a 98.9% success rate in AI-powered takedown, making it a powerful tool for rapid threat identification and removal.


CrowdStrike
Another top contender is CrowdStrike, a cloud-native cybersecurity platform that provides rapid threat detection and response through AI-native technology. With a generative AI security analyst and next-gen SIEM, it offers comprehensive protection across endpoints, cloud workloads, identities, and data. CrowdStrike's platform has received top ratings in cybersecurity incident response and endpoint protection, ensuring a comprehensive and efficient response to threats.


Darktrace
Darktrace is also a top option for end-to-end cybersecurity solutions that use Self-Learning AI to identify and respond to in-progress attacks in real-time. Its capabilities include real-time threat detection, automated response, and native visibility across multiple domains, allowing for flexibility and scalability across businesses of all sizes.


SentinelOne
Finally, SentinelOne provides a single cybersecurity platform with AI-powered endpoint, cloud, identity, and data protection. It includes next-gen EPP, EDR, and XDR tools, along with real-time cloud workload protection and 24/7 threat hunting services. The platform is designed to stay ahead of threats and effectively manage vulnerabilities, making it a great option for comprehensive cybersecurity needs.