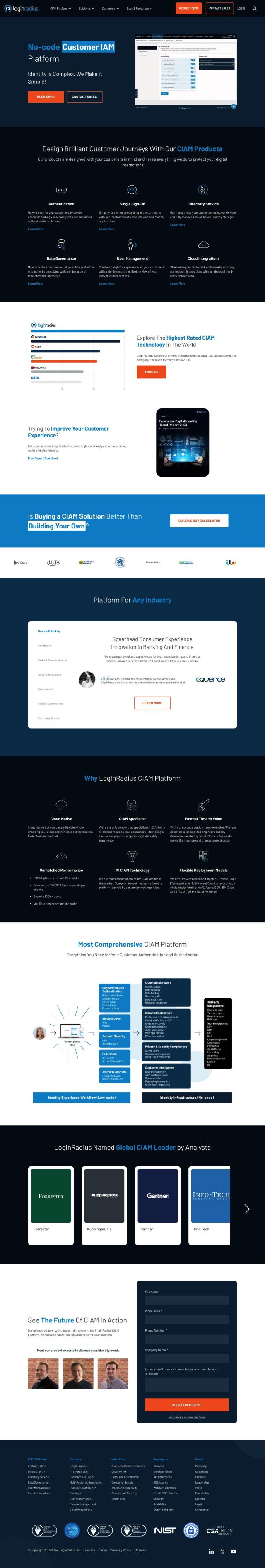
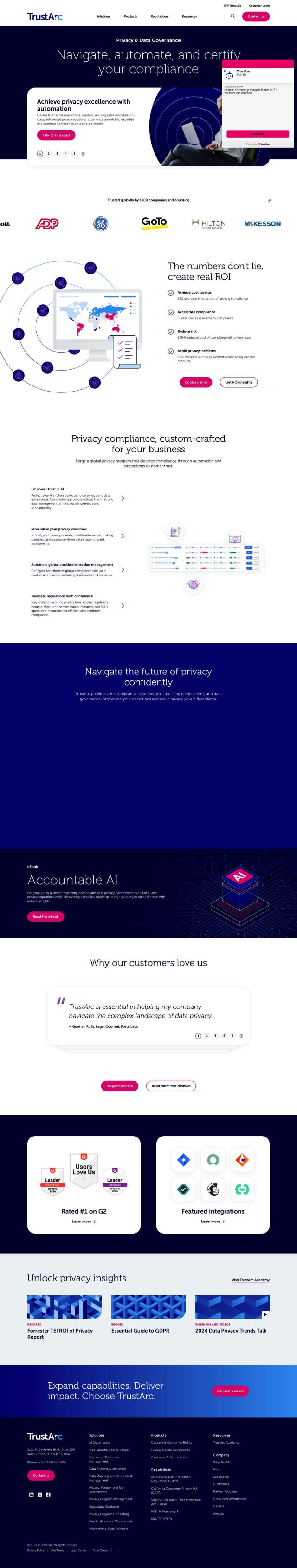
BeyondTrust
For those looking for a Delinea alternative, BeyondTrust offers a broad intelligent identity and access security platform. It offers a unified view of all identities, privileges and access rights to help prevent attacks and deliver dynamic access. With features like secure remote access, identity threat detection and a zero-trust foundation, BeyondTrust is good for a variety of use cases, including cloud access, endpoint security and identity threat detection.


CyberArk
Another major contender is CyberArk, a mature identity security and access management product. It uses AI-infused CORA to grant access to any device while protecting human and machine identities. CyberArk offers SSO, adaptive MFA, lifecycle management and intelligent privilege controls, making it a good fit for organizations trying to move to a Zero Trust model.


RSA
Finally, RSA offers a broad security-first identity product with automated identity intelligence, authentication, access and governance abilities. The RSA Unified Identity Platform supports multiple secure authentication methods and has strong governance and lifecycle management, making it a good fit for high-security organizations like government and financial services.