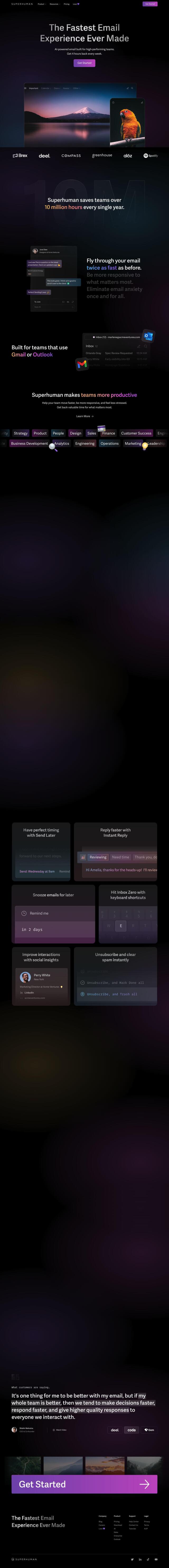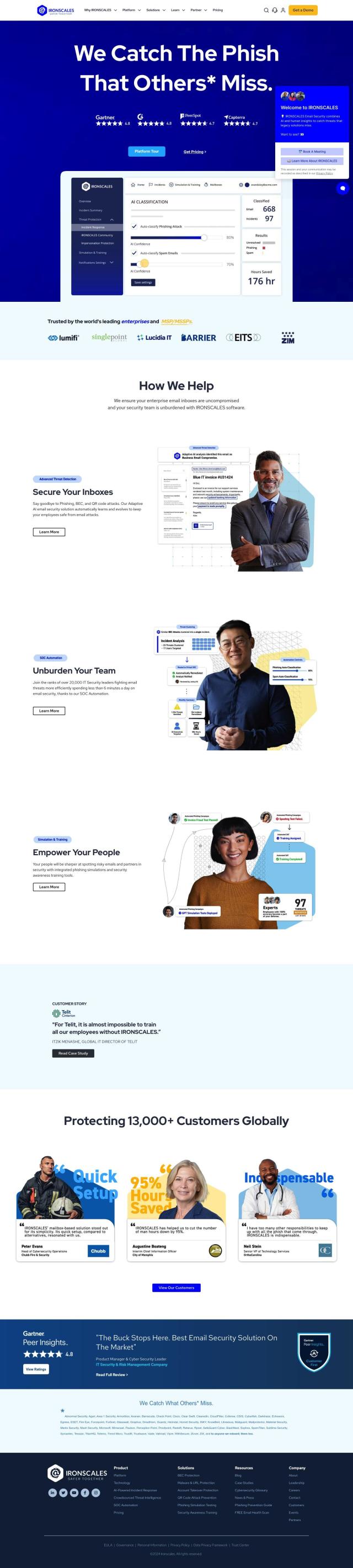
IRONSCALES
If you're looking for another Abnormal alternative, IRONSCALES is a powerful email security solution that uses adaptive AI to combat BEC, ATO and social engineering attacks. It offers a range of features, including inbound email protection, account takeover protection and SOC automation. IRONScales integrates with Microsoft 365 and Google Workspace, making it a good choice for enterprises.
Mimecast
Another option is Mimecast, which uses AI and machine learning to protect against email-based attacks, phishing and ransomware. It offers a range of deployment options and integrates with more than 250 partner technologies, so Mimecast can be a good choice for those who want a flexible, growing security foundation. It also offers security awareness training, DMARC analyzer and collaboration security for Microsoft Teams and SharePoint.


Proofpoint
Proofpoint is another option, with a multi-layered threat detection approach and adaptive email data loss prevention. It combines behavioral AI and human-centric security to thwart impersonation, supplier risk and identity takeover. Proofpoint is used by 87 of the Fortune 100, so it's a good choice for those who want a broad security foundation for many types of businesses.
Vade
If you need something that's very scalable and easy to use, Vade could be a good option. It protects more than 1.4 billion mailboxes around the world with its AI-powered engine that evaluates text, context and visual data to block threats. Vade integrates with Microsoft 365 and is designed for MSPs, SMBs and ISPs, so it's a good option for those who want a security and compliance foundation.