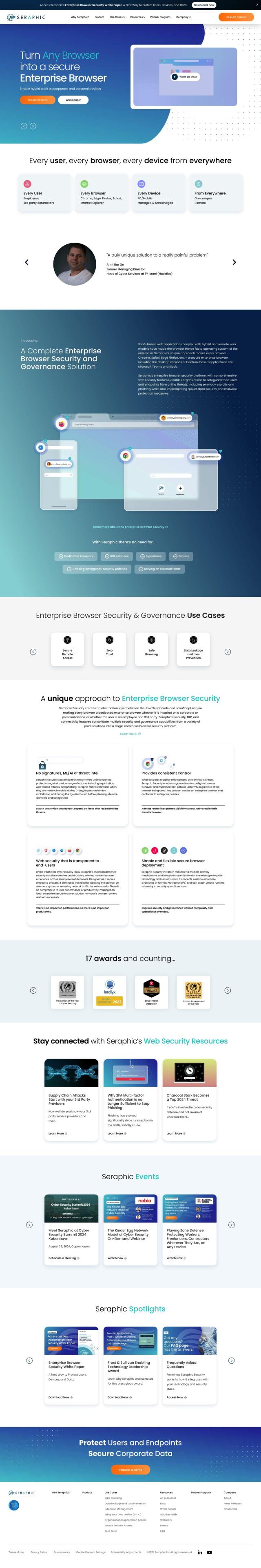
Question: I'm looking for a solution that provides Zero Trust security controls and remote browser isolation to protect against modern threats.
Ericom
If you need a more complete solution that includes Zero Trust security controls and remote browser isolation to thwart today's threats, check out the Ericom Cloud Security Platform. It combines Zero Trust with Remote Browser Isolation technology to protect devices, applications, networks and data. It also includes generative AI data loss prevention, zero-day cyberattack protection, secure web and email access, and virtual meeting security, so it's a good option for companies of all sizes.


Menlo Security
Another good option is Menlo Security, which offers a cloud-based Enterprise Browser product that protects against phishing and malware attacks on any browser and any device. It also offers zero-hour phishing protection, evasive ransomware prevention, VDI replacement, zero-trust access and secure generative AI. Menlo Security's technology uses AI-powered threat prevention to remove the browser attack surface, protecting against modern zero-day web exploits and evasive attacks.
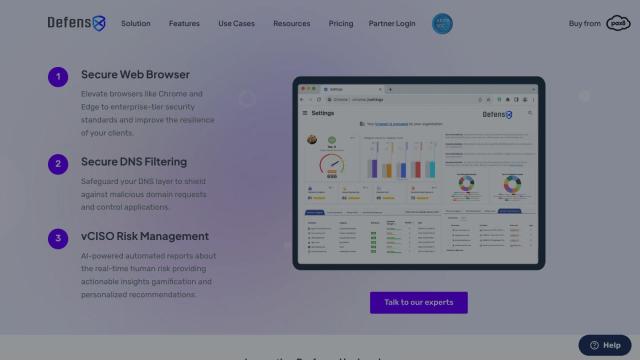
DefensX
If you want more advanced web browser security, DefensX offers a secure web browser that isolates threats from endpoint devices, locking down browsers like Chrome and Edge with enterprise-strength security. It includes features like DOM Security, Zero-Trust Web, Zero-Trust Passwords, Zero-Trust Files and Remote Browser Isolation, so it's a good option for Managed Service Providers (MSPs) who want to expand their cybersecurity services.
Palo Alto Networks
And Palo Alto Networks offers a cybersecurity platform that incorporates Zero Trust principles, protecting networks, cloud workloads and hybrid workforces with threat intelligence and security consulting services. It includes Precision AI for real-time threat detection, a unified Network Security Platform and full Cloud Security offerings, so it's a good option for a wide range of industries.