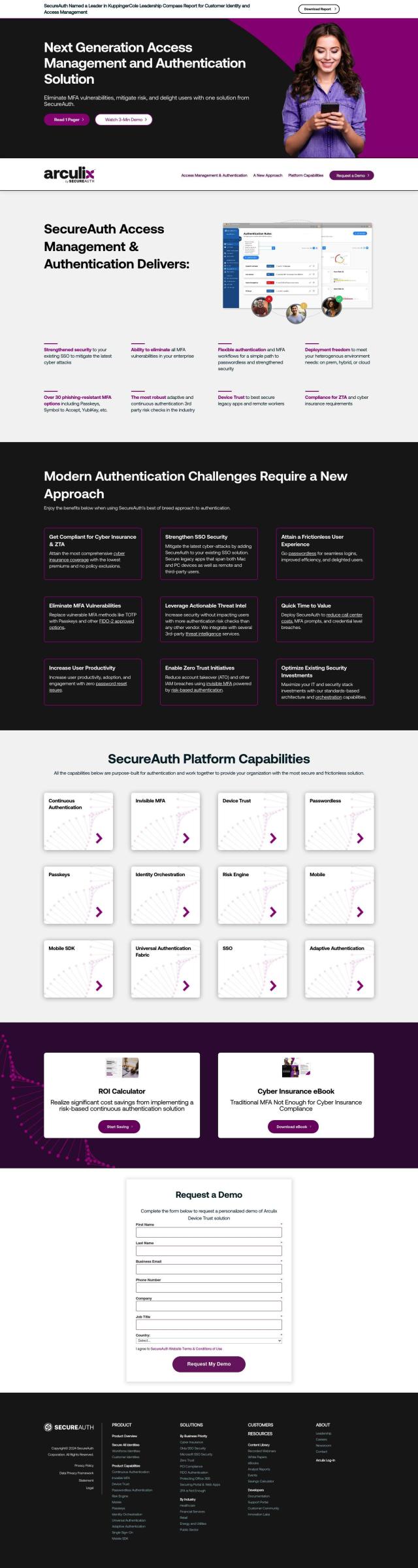
Question: I'm looking for a platform that enforces zero trust device posture and verifies user identity from login to logout.
Infinipoint
If you're looking for a platform that enforces zero trust device posture and verifies user identity from login to logout, Infinipoint could be a great option. It provides secure access through continuous authentication of user identity and device posture, offers phishing-resistant passwordless and multi-factor authentication, and comes with a remediation toolbox for real-time remediation use cases. This platform verifies zero trust device posture for every login attempt, thereby thwarting account takeovers and weak device posture attacks.


BeyondTrust
Another top option is BeyondTrust, an intelligent identity and access security platform. It offers a 360-degree view of all identities, privileges, and access, protects identities, prevents threats, and offers dynamic access. With features like secure remote access, identity threat detection, and privilege transparency, BeyondTrust spans a broad range of use cases, including cloud access, endpoint security, and secure remote access management, so it's a good option for zero-trust efforts.
nudata Security
If you're looking for something a bit different, check out nudata Security. It fuses behavioral biometrics, device behavior, and a proprietary trust network to continuously assess and differentiate legitimate users from threats in real-time. This platform offers a frictionless user experience without compromising security, which is why it's well-suited for financial services, fintech, and eCommerce companies.


CyberArk
Last but not least, CyberArk offers an identity security and access management solution that includes features like secure Single Sign-On, Adaptive Multi-Factor Authentication, and lifecycle management. With intelligent privilege controls and flexible identity automation, CyberArk helps organizations maintain a strong identity security posture and move to a more mature Zero Trust strategy.