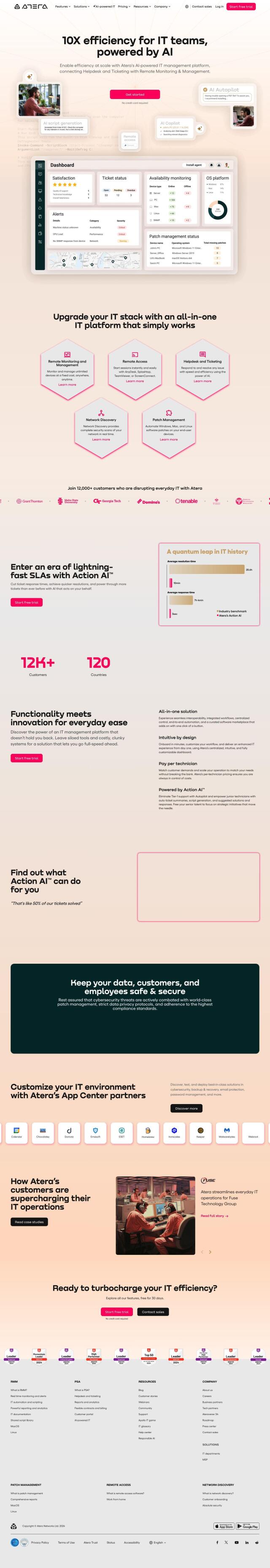
Question: Is there a unified endpoint management tool that can help me streamline remote IT operations and prevent data breaches?


SentinelOne
If you're looking for a unified endpoint management tool to simplify remote IT work and reduce the risk of data breaches, SentinelOne also offers a full cybersecurity platform. The AI-based system covers endpoint, cloud, identity and data protection with next-gen EPP, EDR and XDR tools, as well as 24/7 threat hunting and managed services. It's a good option for companies that need to keep up with sophisticated threats.


CrowdStrike
Another strong contender is CrowdStrike, a cloud-based cybersecurity platform that protects endpoints, cloud-based computing workloads, identities and data. It uses agent and agentless protection, real-time identity protection and a next-gen SIEM for full visibility into threats and real-time insights. CrowdStrike has won industry accolades and has good integration, so it's a good option for companies dealing with more sophisticated attacks.
IT Complete
IT Complete from Kaseya is another all-in-one tool for managing and securing IT operations. It offers remote endpoint management, security, risk assessment, data backup and restore. With features like advanced RMM, unified backup and networking management, IT Complete is geared for IT staff and MSPs who want to automate as much as possible and improve security.
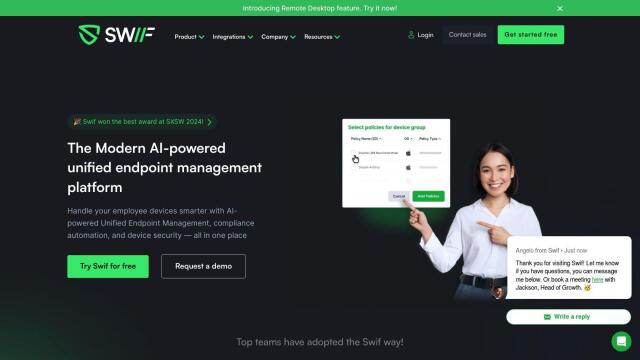
Swif
For those who need to automate compliance and device security, Swif offers a GenAI-powered unified device management platform. It includes tools for automating security and access reports, setting up company security policies and enforcing device compliance on macOS, Windows and Linux. Swif's automated control and data breach prevention abilities make it a good option for IT managers and cybersecurity analysts.