Question: How can I simplify identity security and make it easier to deploy and manage across my enterprise?


CyberArk
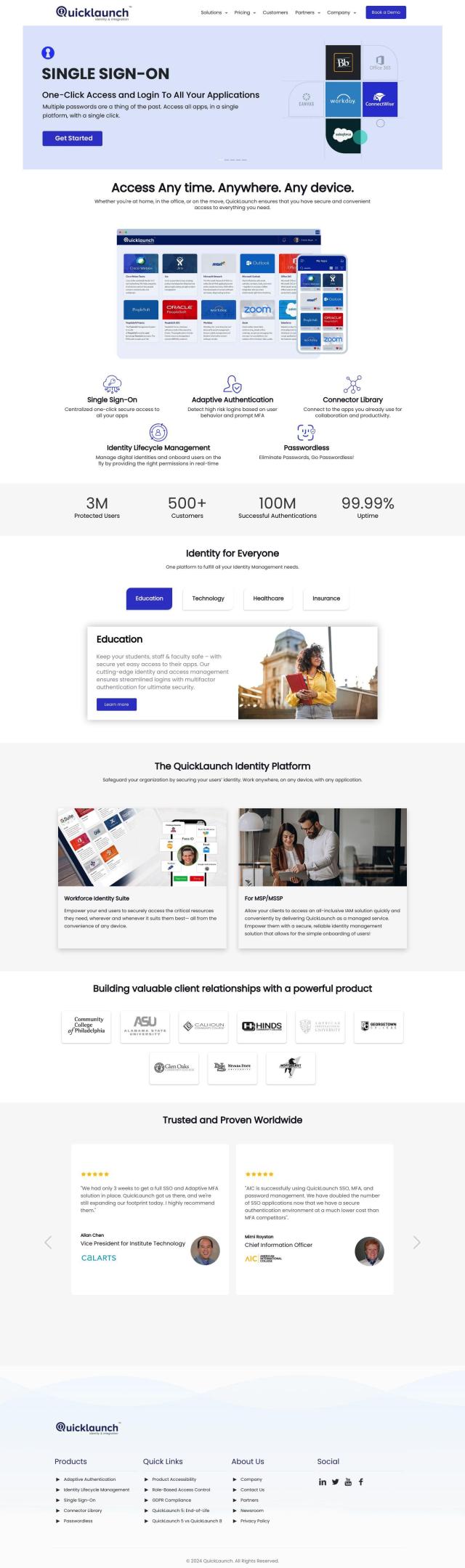
If you want to streamline identity security and span your enterprise, CyberArk is a good all-in-one option. It can grant access to any device, anywhere, with Single Sign-On, Adaptive Multi-Factor Authentication and lifecycle management. CyberArk serves many industries and has more than 200 alliance partners with 300 integrations, so it's a good choice for identity security that's not too complicated.


BeyondTrust
Another good option is BeyondTrust, which offers a 360-degree view of all identities and privileges. It's got secure remote access, identity threat detection and response, and a zero-trust approach to least privilege, and it integrates with many other tools to ensure centralized control and visibility. BeyondTrust has been named a leader in several industry reports, and it's got more advanced features for deeper identity security.
SailPoint
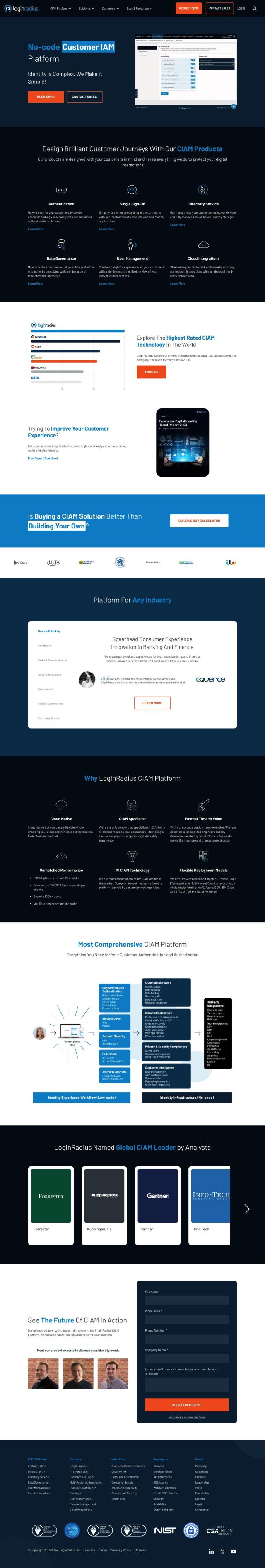
SailPoint also has a unified identity security platform that ties into many different ecosystems. It offers real-time visibility, automated identity processes and centralized access control across all data and applications. With machine learning and AI technology, SailPoint can ensure the right people have access to sensitive resources while keeping things secure. It offers three suites to accommodate different organizational needs.


Delinea
For smart authorization and identity security, Delinea is another good option. It offers real-time, centralized authorization to protect privileged access and includes tools like Enterprise Vault for managing audit credentials and DevOps Vault for protecting secrets. Delinea promises 99.99% uptime for reliable security, and it's relatively easy to deploy and manage identity security.