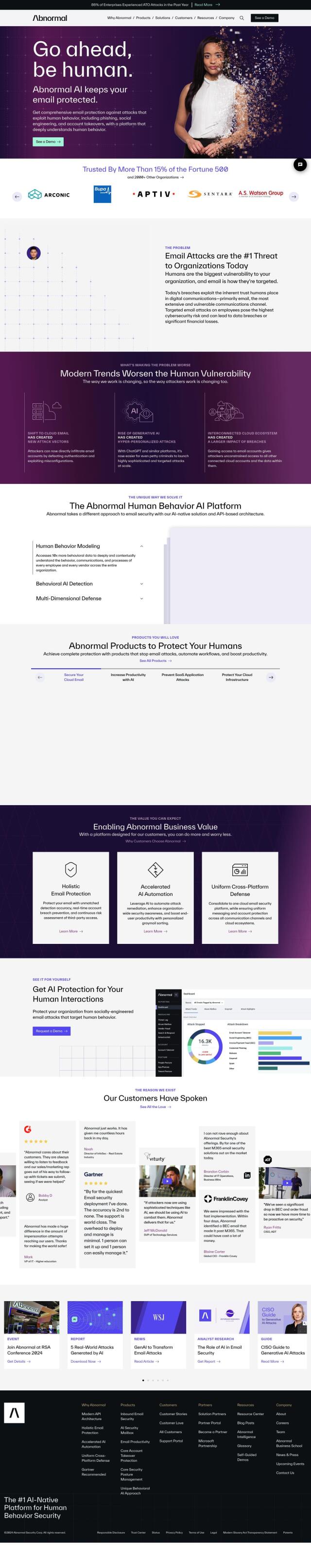
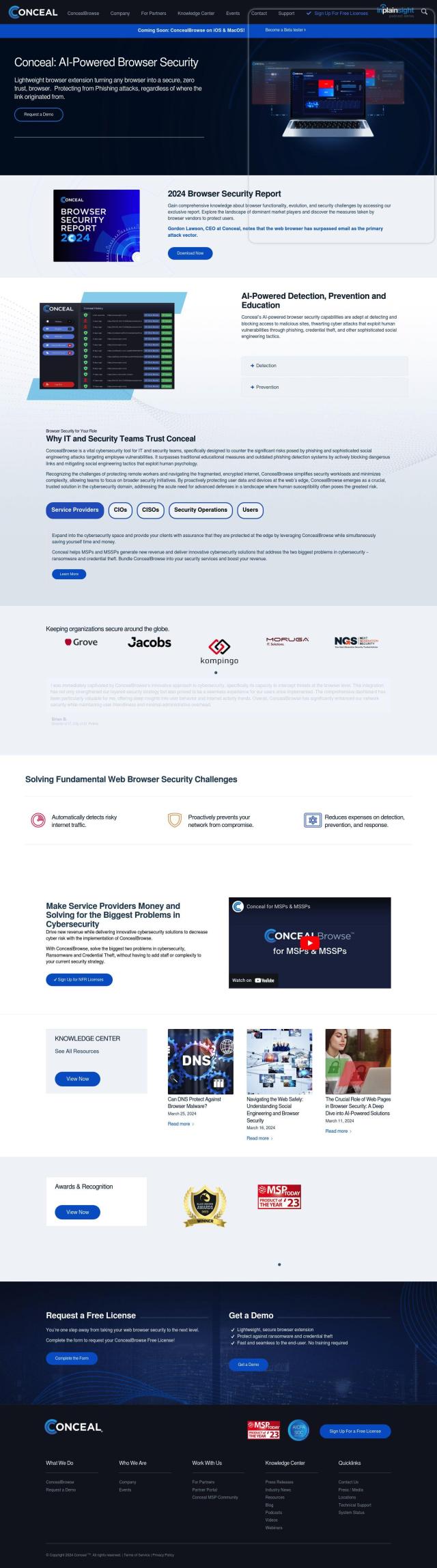
Question: How can I protect my customers from malware and phishing attacks while ensuring a seamless user experience?


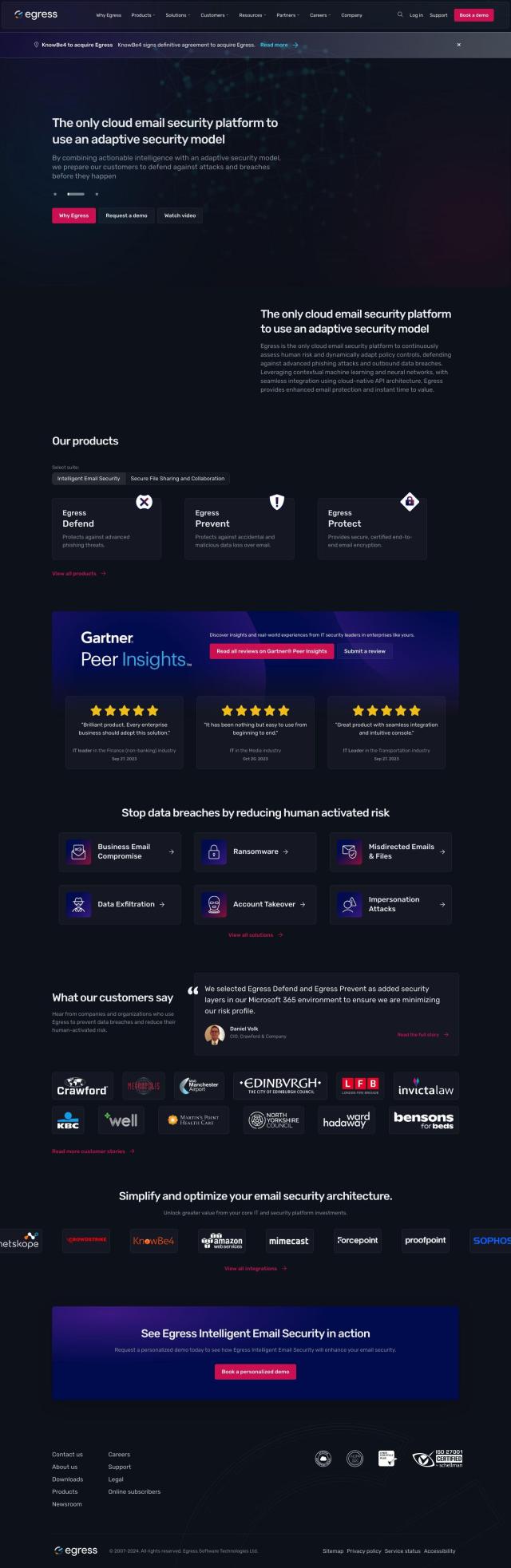
IBM Security Trusteer
IBM Security Trusteer is a cloud-based information security platform that uses AI and machine learning to authenticate customers, prevent fraud and protect against malicious users across all channels. It includes real-time fraud detection, identity risk assessment, mobile device risk assessment, compromised device detection, and malware and phishing protection. The platform provides continuous digital identity assurance and a scalable, agile cloud platform, making it a comprehensive solution for reducing risk and delivering a frictionless experience.


CrowdStrike
Another top choice is CrowdStrike, a full-spectrum, cloud-based cybersecurity platform that delivers advanced protection for endpoints, cloud workloads, identities and data. It offers agent and agentless protection, real-time identity protection and a next-gen SIEM for complete threat visibility. CrowdStrike's platform includes next-gen endpoint protection, USB device control and host firewall management, delivering a single cloud security solution that integrates seamlessly to stop sophisticated threats.


Darktrace
For a more AI-based approach, Darktrace uses Self-Learning AI to detect and respond to in-progress cyber attacks in real-time, including ransomware, email phishing and cloud and infrastructure attacks. It provides real-time threat detection, contextual understanding, threat correlation, automated response and native visibility across clouds, devices, communications, locations, applications and people. This makes it a flexible and scalable solution for businesses of all sizes to stay ahead of cyber threats.


SentinelOne
Finally, SentinelOne offers a single, unified solution for endpoint, cloud, identity and data protection with its AI-powered platform. It includes next-gen EPP, EDR and XDR tools for endpoint security, real-time cloud workload protection, identity threat detection and response, and data analytics for centralized and actionable insights. With 24/7 threat hunting and managed services, SentinelOne is a great fit for organizations that want to reduce risk and increase efficiency.