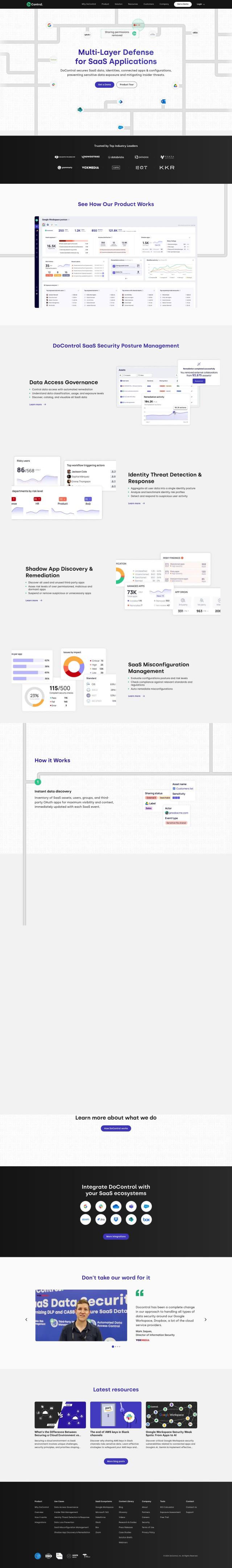
Question: I'm looking for a tool that helps enforce least privilege principles and identifies permission risks in our organization.
Oleria
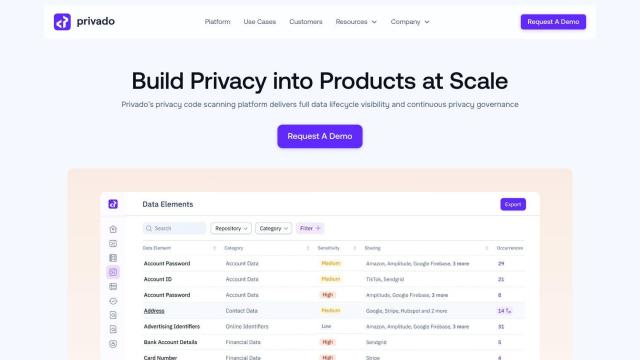
For enforcing least privilege principles and identifying permission risks, Oleria is a comprehensive security solution that offers end-to-end identity security by connecting identity silos across enterprise IAM and decentralized SaaS platforms. It provides real-time access usage visualization, fine-grained access visibility, access graph, activity analysis, account usage, access inventory, and risk monitoring. These insights help you enforce least privilege principles, detect and remediate permission risks, and respond to incidents faster.


BeyondTrust
Another excellent choice is BeyondTrust, which provides a 360-degree view of all identities, privileges, and access to protect identities, stop threats, and deliver dynamic access. It features full privilege transparency, secure remote access, detection and response to identity threats, and protection of privileges at scale. With its advanced features and capabilities, BeyondTrust supports a wide range of use cases, making it an effective tool for enforcing least privilege and managing permission risks.


Varonis
Varonis offers an all-in-one SaaS platform for automated data security, providing comprehensive solutions for data discovery, classification, threat detection, and policy automation across multiple cloud and on-premises environments. Its features include DSPM, AI security, cloud DLP, UEBA, and compliance management, all designed to deliver automated outcomes, real-time visibility, and proactive threat detection. This platform is ideal for organizations seeking deep data visibility and automated remediation to enforce least privilege.


Delinea
For centralized authorization and identity security, Delinea is worth considering. It offers real-time, centralized authorization to protect privileged access across an organization. It includes features like Enterprise Vault for managing privileged access, DevOps Vault for securing secrets, Service Account Lifecycle for governing service accounts, and Detect & Remediate Threats for proactively identifying and mitigating identity-based threats. This platform is designed to streamline deployment and management, ensuring reliable security with a 99.99% uptime guarantee.