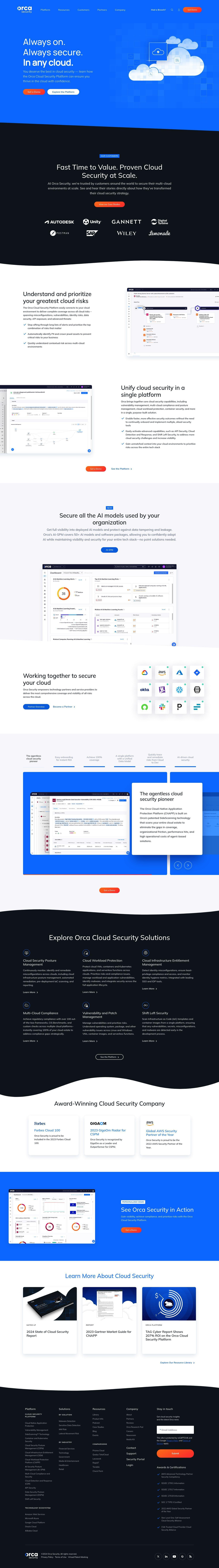
Orca Security is an agentless, cloud-native application protection platform that offers comprehensive cloud infrastructure security and compliance. It's a single platform for all cloud security needs, providing 100% coverage across cloud risks including misconfigurations, vulnerabilities, identity risks, data security, API exposure, and advanced threats.
Orca Security consolidates core cloud security functions like vulnerability management, multi-cloud compliance and posture management, cloud workload protection, container security, and more. It also offers advanced features like AI-driven risk prioritization, automated detection and remediation of misconfigurations, and multi-cloud compliance management. This means security teams can focus on higher-value work and reduce the daily grind and stress.
Orca's AI-driven cloud security capabilities provide a more comprehensive view of cloud security postures and contextual risk visibility across the entire tech stack. It also includes a patented SideScanning technology that can scan the entire cloud estate without agents, eliminating gaps in coverage, organizational friction, performance hits, and high operational costs.
Some of the key features of Orca Security include:
- Unified Platform: Consolidates CSPM, CWPP, CIEM, DSPM, Vulnerability Management, API Security, Compliance, and more into a single platform.
- Agentless Cloud Security: No agents are required to be deployed, reducing overhead and friction.
- Context-Aware Risk Prioritization: Identifies and prioritizes the top combination of risks that matter.
- Multi-Cloud Compliance: Supports over 100 out-of-the-box frameworks, CIS Benchmarks, and custom checks.
- AI-Driven Cloud Security: Improves security postures and reduces daily workloads and stress.
- Shift Left Security: Scans Infrastructure as Code (IaC) templates and container images for vulnerabilities and secrets.
- Attack Path Analysis: Shows teams which cloud security risks endanger critical business assets and provides remediation guidance.
Orca Security is well-suited for organizations with a multi-cloud environment that need complete visibility and centralized management of their entire cloud estate. It is also well-suited for those looking to consolidate cloud security capabilities, reduce alert fatigue, and effectively prioritize risks. With its AI-driven approach and comprehensive coverage, Orca Security empowers security teams to work smarter, not harder.
Published on July 21, 2024
Related Questions
Tool Suggestions
Analyzing Orca Security...