Question: Can you recommend a cloud-based solution for protecting digital content from piracy and unauthorized use?
PallyCon
For a cloud-based solution to protect digital content from piracy and unauthorized use, consider PallyCon. PallyCon is a comprehensive digital rights management (DRM) and forensic watermarking service that prevents leakage and unauthorized content use. It supports various DRM standards like PlayReady, Widevine, and FairPlay, and integrates with AWS for a high-performance, multi-region architecture. PallyCon offers features such as global monitoring, takedown notices, and a flexible pricing model, making it suitable for VOD and live streaming applications.


Axur
Another strong option is Axur, which leverages artificial intelligence to monitor and remove digital threats across the Deep and Dark Web. Axur excels in fast threat detection and mitigation, offering tools for brand protection, AI-powered takedown, and data leakage prevention. Its robust cybersecurity platform ensures quick and accurate identification and removal of digital threats, making it a reliable choice for content protection.
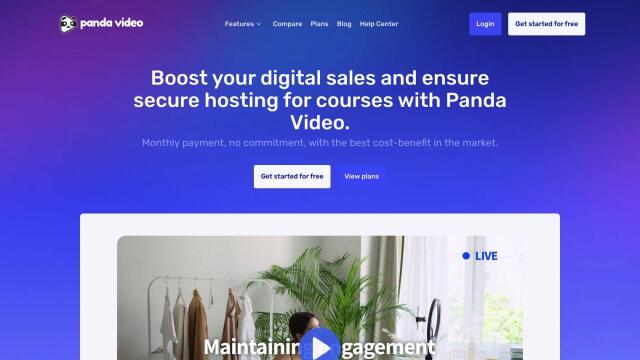
Panda Video
For those specifically focused on video content, Panda Video offers a secure video hosting platform designed for digital sales and course creators. Panda Video includes features like AI-optimized video processing, DRM watermarking, and customizable CTA buttons to boost engagement and conversion. With different pricing tiers, Panda Video aims to improve user engagement and thwart piracy, making it an excellent choice for secure video sharing.
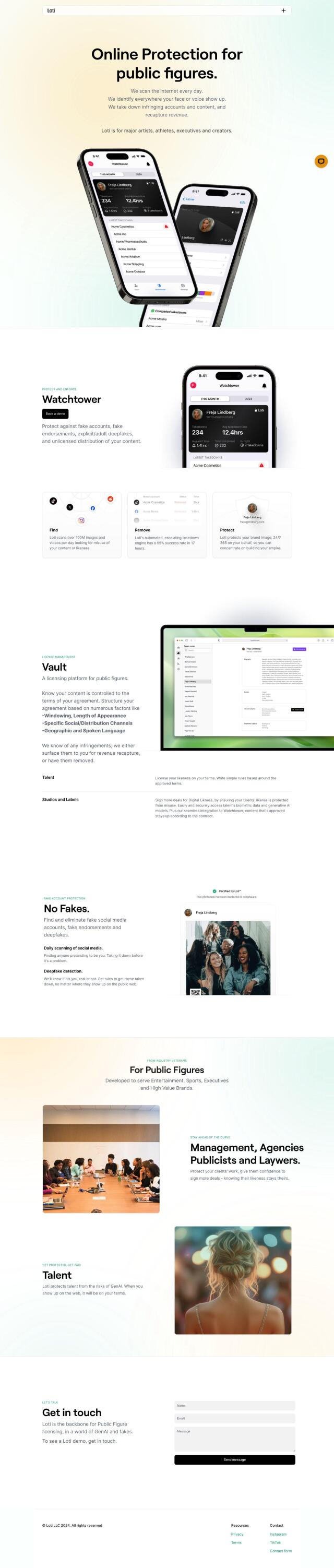
Loti
Lastly, Loti provides a specialized service for public figures and creators to detect and remove infringing content. Its platform includes Watchtower for daily image and video monitoring, Vault for content licensing, and No Fakes for eliminating fake social media accounts and deepfakes. Loti also offers an automated takedown engine with a high success rate, providing an extra layer of protection for valuable digital assets.