Question: Is there a platform that can automate credential rotation and minimize standing privileges for compliance and security?


Akeyless
Akeyless is a cloud-native SaaS platform for secure secrets management without vault management. It includes automated credential rotation, just-in-time credentials and a range of secure access management tools like PKI as a service and secure remote access. Akeyless integrates with tools like Ansible, AWS, Azure, GitHub and Kubernetes, so it's a good option for companies that want to improve their security without disrupting their existing operations.
CloudTruth
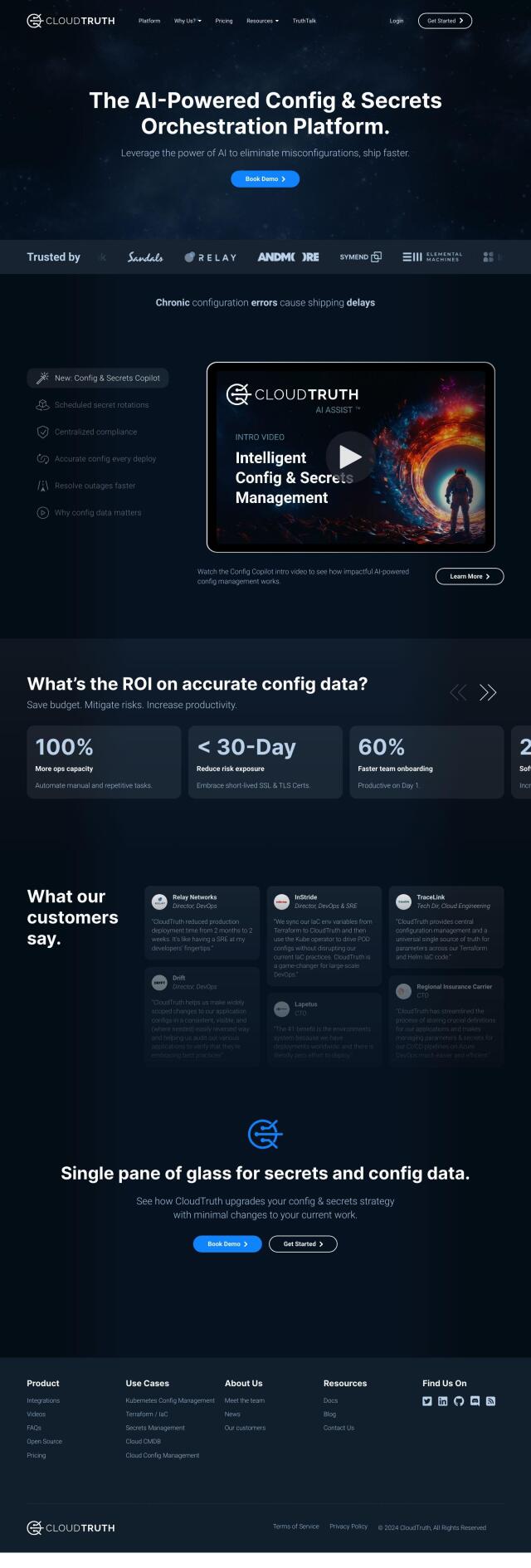
CloudTruth is another option worth considering. It uses AI to automate and orchestrate config management, ensuring secrets and config data is up to date and accurate. Scheduled secret rotations and centralized compliance are also features that can help reduce errors and security risks. It's a single source of truth for config and secrets management, and it integrates with CI/CD and IaC tools like Terraform, Kubernetes and GitHub, so it's a good choice for complex infrastructure and application environments.


CyberArk
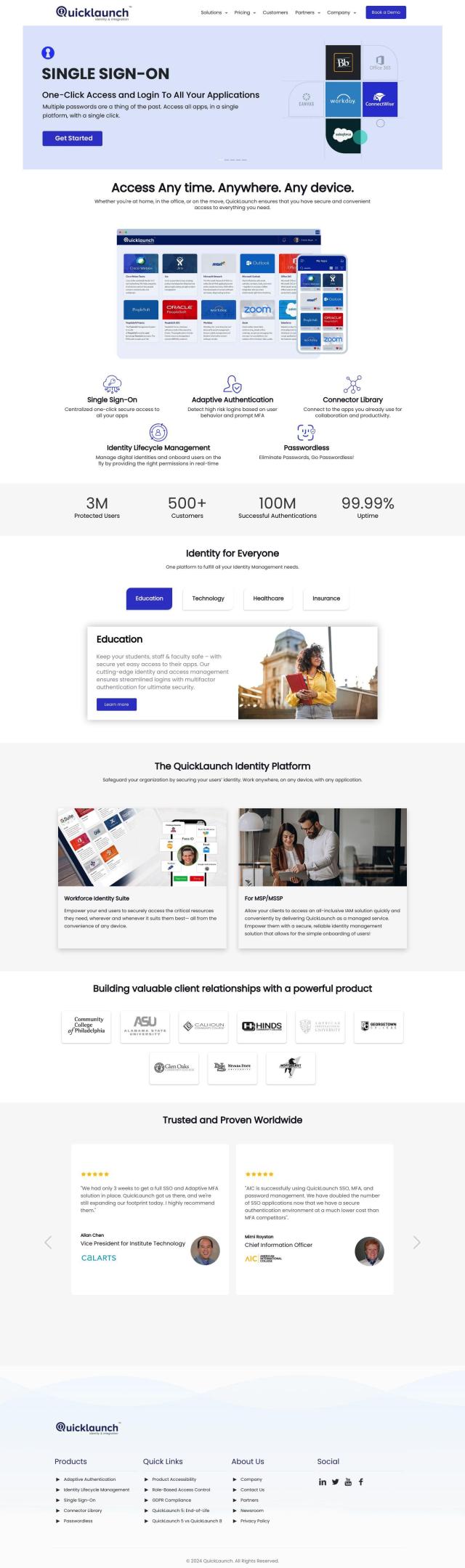
If you want a broader identity security foundation, check out CyberArk. CyberArk provides secure access to any device, anywhere, at any time, with features like SSO, Adaptive MFA and lifecycle management. It's used in a variety of industries, and the company offers flexible pricing, so it's a good option for companies that want to move to a more serious Zero Trust approach.