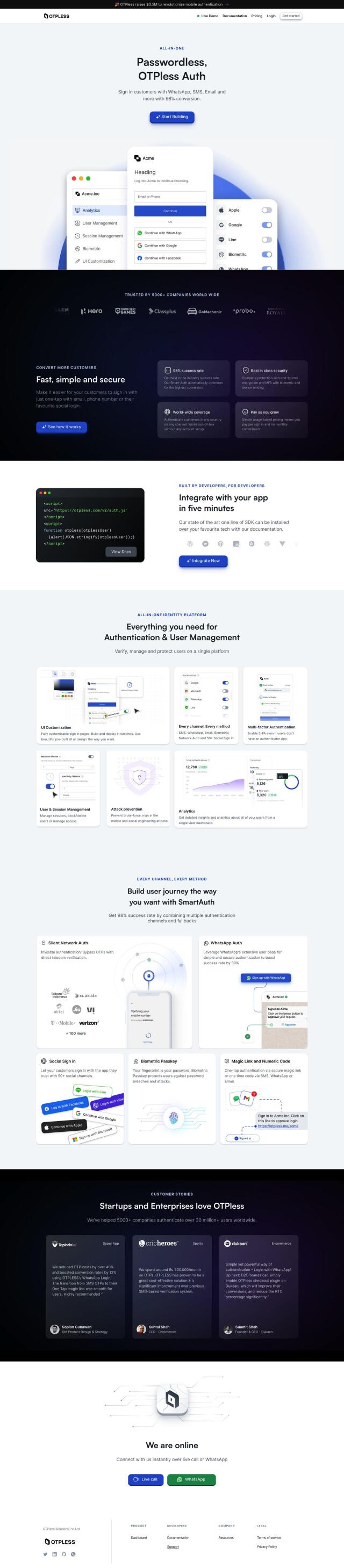
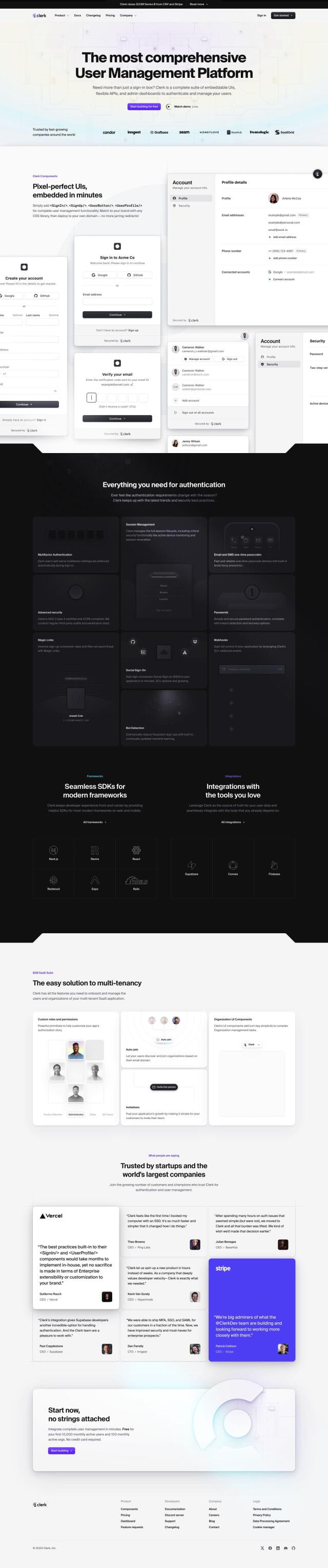
CyberArk
If you're looking for a SecureAuth alternative, CyberArk is an identity security and access management platform that offers secure access to any device, anywhere, with the power of artificial intelligence through its CyberArk CORA AI. The platform offers secure Single Sign-On (SSSO), Adaptive Multi-Factor Authentication (MFA), lifecycle management, directory services, and user behavior analytics. CyberArk also offers intelligent privilege controls and flexible identity automation, making it a great option for protecting identity security postures and embracing a Zero Trust strategy.
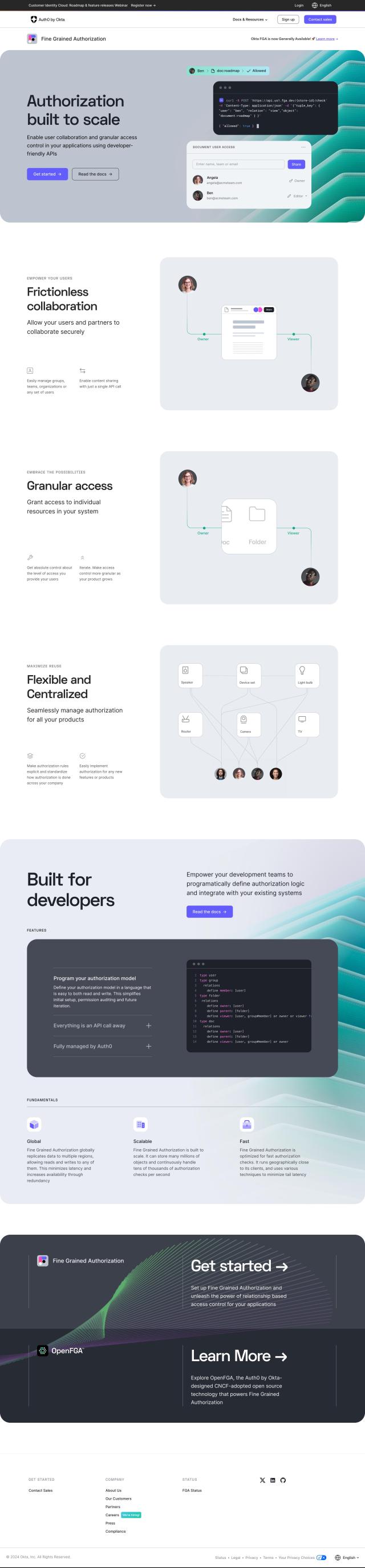
Auth0
Another top SecureAuth alternative is Auth0, an authentication and authorization platform that offers secure access to users while giving you control over access permissions. With features like Universal Login, Single Sign On, Multifactor Authentication, and customizable actions, Auth0 offers a flexible and scalable solution for managing customer identities across many industries. Its extensive developer tools make it a great option for small startups to large enterprises, with more than 30 SDKs and Quickstarts for easy integration with many languages and frameworks.
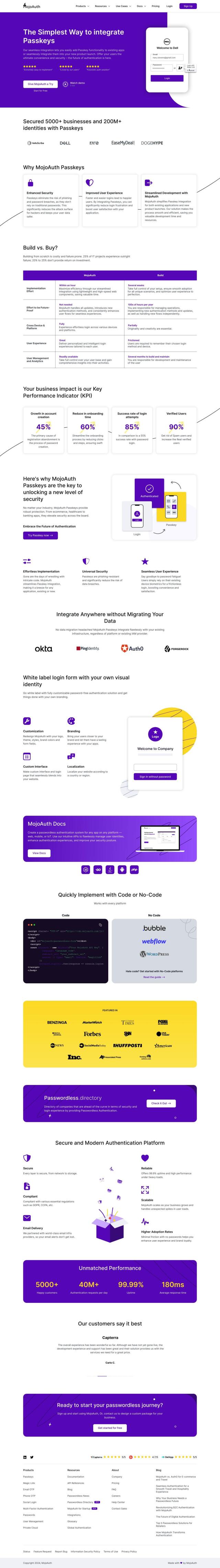
MojoAuth
If you're looking for a passwordless authentication option, MojoAuth offers a secure and seamless login experience for web and mobile applications. The platform eliminates the vulnerabilities of passwords, reducing the attack surface for hackers and protecting user data better. MojoAuth offers features like enhanced security, improved user experience, streamlined development, and universal compatibility, making it a great option for industries such as ecommerce, healthcare, and banking.