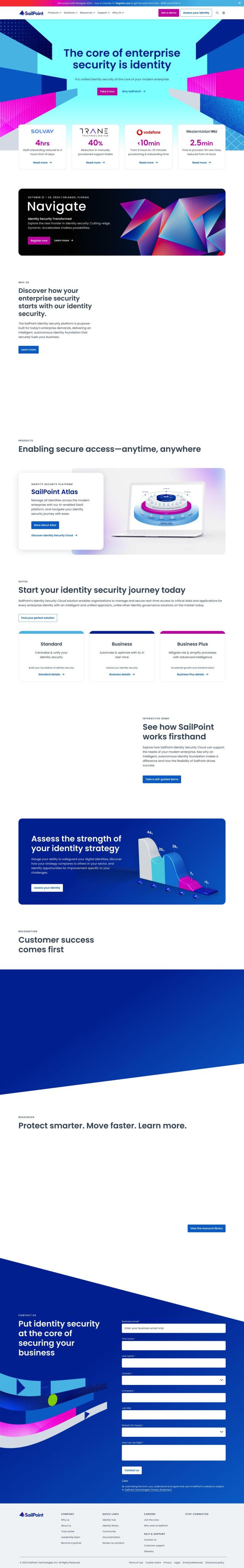
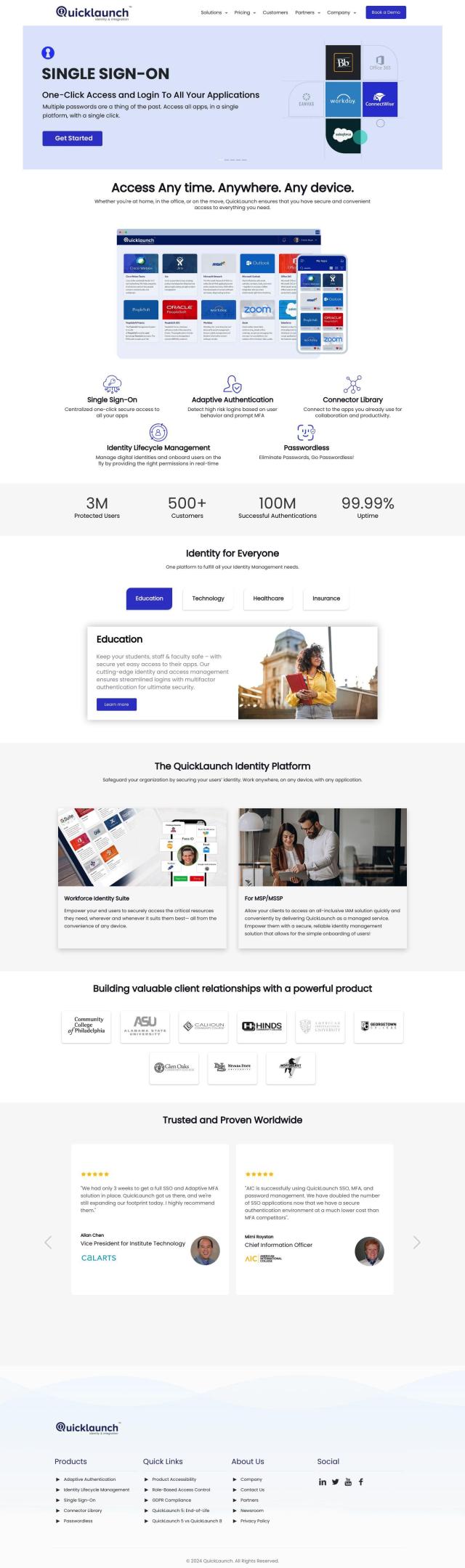
CyberArk
If you're looking for a SailPoint alternative, CyberArk is another option worth considering. CyberArk provides an identity security and access management platform with AI capabilities through CyberArk CORA AI. The platform offers secure Single Sign-On, Adaptive Multi-Factor Authentication and lifecycle management, and is designed to protect both human and machine identities.


BeyondTrust
Another option is BeyondTrust, an intelligent identity and access security platform that offers a 360-degree view of identities, privileges and access. With features like secure remote access, threat detection and response, and a zero-trust approach, BeyondTrust is a good fit for a variety of use cases, including cloud security and compliance.


RSA
If you're looking for a security-focused identity solution, RSA offers a unified identity platform with automated identity intelligence and advanced risk assessment. The platform supports multiple authentication methods and has governance and lifecycle management, so it's a good option for industries with high security requirements like government and financial services.


Delinea
Last, Delinea is focused on real-time, centralized authorization to protect privileged access across an organization. Features like Enterprise Vault for privileged access management and Detect & Remediate Threats for proactive threat response make Delinea a good option for those who want to simplify their identity security deployment and maintain high security.