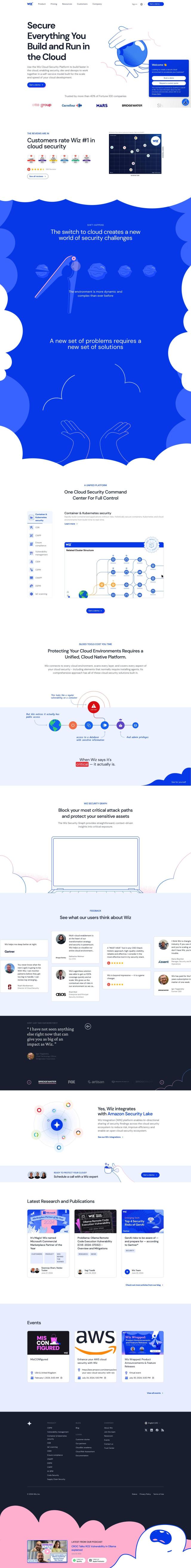
Auditive
If you're looking for a SafeBase alternative, Auditive is a good option. It's an AI-powered third-party risk marketplace that automates security assessments for vendors and buyers by continuously monitoring vendors against specific security requirements. With automated security assessments, accelerated sales and continuous risk monitoring, Auditive integrates with tools like Salesforce, Slack, Jira and Drata to keep your workflow running smoothly.


Tenable
Another option is Tenable, an all-in-one cybersecurity platform that handles vulnerability management, cloud security, operational technology security and identity exposure management. Tenable offers real-time vulnerability assessment and prioritization, attack path analysis and unified identity and entitlement risk management. It's compliant with regulations like FISMA, HIPAA and PCI, so it's good for a variety of industries and helps organizations understand and manage their cyber risk in real time.
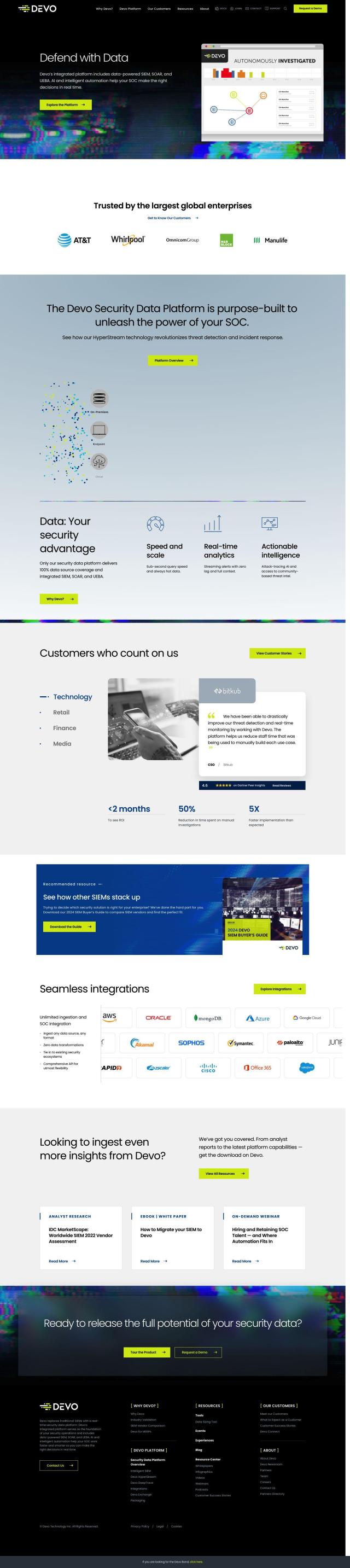
Devo
If you prefer a SIEM, SOAR and UEBA-based solution, Devo is another option. It combines these technologies to help Security Operations Centers (SOCs) better detect and respond to threats. With AI and automation tools, sub-second query performance and real-time analytics, Devo offers cloud-native, SaaS-based solutions that scale for a variety of industries. It gives you visibility into security data from an unlimited number of sources.


Whistic
Last, Whistic is a powerful third-party risk management software that automates vendor assessments and streamlines the process through its AI-powered platform. Features include a centralized Trust Center for security and compliance documentation, AI integration for task automation, and a network for efficient information sharing. Whistic is designed to reduce the potential for breaches and accelerate the sales process, making it a good alternative for companies looking to improve their third-party risk assessments.