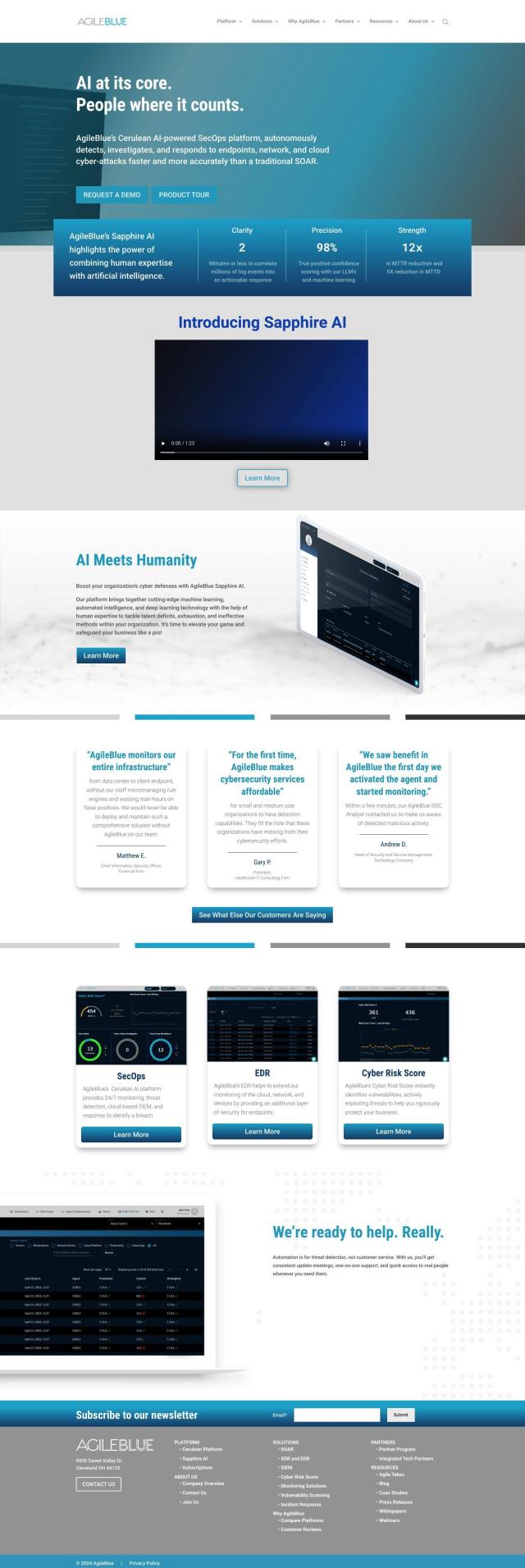
Flashpoint
If you're looking for a replacement for Microsoft Defender Threat Intelligence, Flashpoint is a full cyber threat intelligence platform that offers timely and accurate threat intelligence. It serves a range of teams, including CTI/SOC, Fraud Teams and Corporate Security, and combines human-sourced data collection with advanced analytics and dashboards. Flashpoint's staff augmentation and managed intelligence services make it a good option to boost your security posture.


Vectra AI
Another good option is Vectra AI, which uses AI-powered Attack Signal Intelligence to identify and respond to threats in real time. It offers continuous protection across hybrid cloud environments, including network detection and response, and managed extended detection and response services. Vectra AI's AI technology reduces alert noise by up to 90% and covers more than 90% of hybrid cloud MITRE ATT&CK techniques, so it's a good option for threat hunting and response.


Darktrace
Darktrace is also worth a look, using Self-Learning AI to detect and respond to in-progress cyber attacks. It offers real-time threat detection and automated response, and a single view of security threats across clouds, devices and applications. It's designed for companies of all sizes, with the goal of staying ahead of cyber attacks and achieving true cyber resilience.


SentinelOne
Last, SentinelOne offers a unified cybersecurity AI platform for endpoint, cloud, identity and data protection. With next-gen EPP, EDR and XDR tools, real-time cloud workload protection and 24/7 threat hunting, SentinelOne offers a complete cybersecurity solution. It's a well-regarded option, having been named a Leader in the 2023 Magic Quadrant for Endpoint Protection Platforms, so it's a good option to reduce risk and increase efficiency.