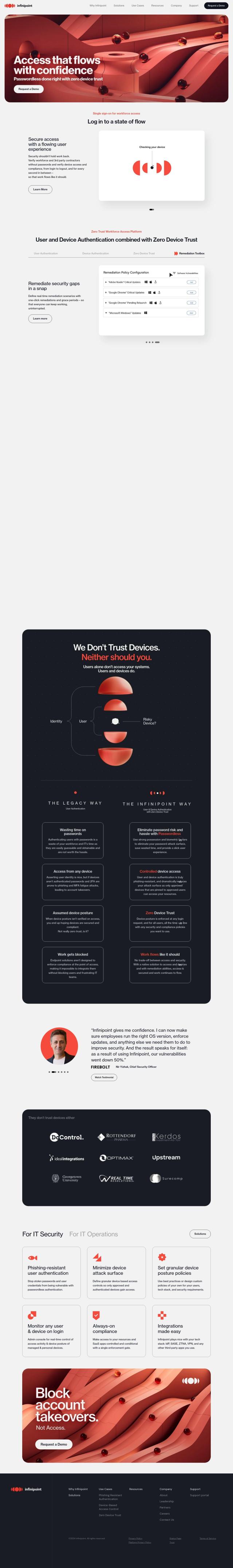
CyberArk
If you're looking for a Keeper alternative, CyberArk is another good option. It's a broad identity security and access management system with SSO, adaptive MFA, lifecycle management and directory services. CyberArk also offers more sophisticated identity automation and orchestration, and a large library of integrations with more than 300 out-of-the-box solutions, making it a good foundation for a Zero Trust strategy.


BeyondTrust
Another good option is BeyondTrust, an intelligent identity and access security platform. It offers a 360-degree view into all identities and privileges, along with secure remote access and identity threat detection. BeyondTrust integrates with a wide range of tools and systems to support a zero-trust approach, and it's a good option for endpoint security and compliance.
Arculix
Arculix is another option worth considering, with continuous authentication and a frictionless user experience. Its features include invisible MFA, passwordless authentication and a risk engine that can help reduce credential-level breaches and support zero-trust efforts. It can be deployed in on-premises, hybrid or cloud environments, and offers strong adaptive authentication and risk checks.


Akeyless
If you're focused on secrets management, Akeyless is a cloud-native SaaS platform that uses Distributed Fragments Cryptography (DFC) for secure secrets management. It includes features like automated credential rotation, just-in-time credentials and secure Kubernetes secrets management, so it's a good option for organizations that want to improve their security.