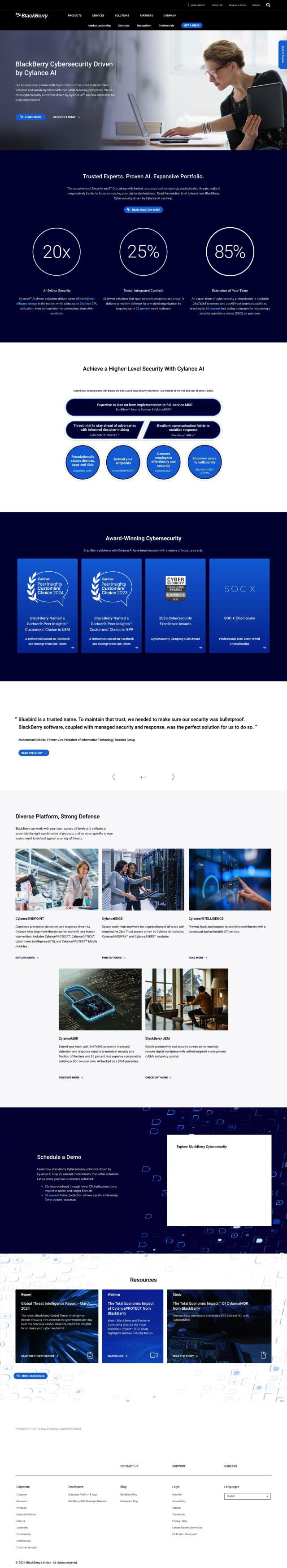
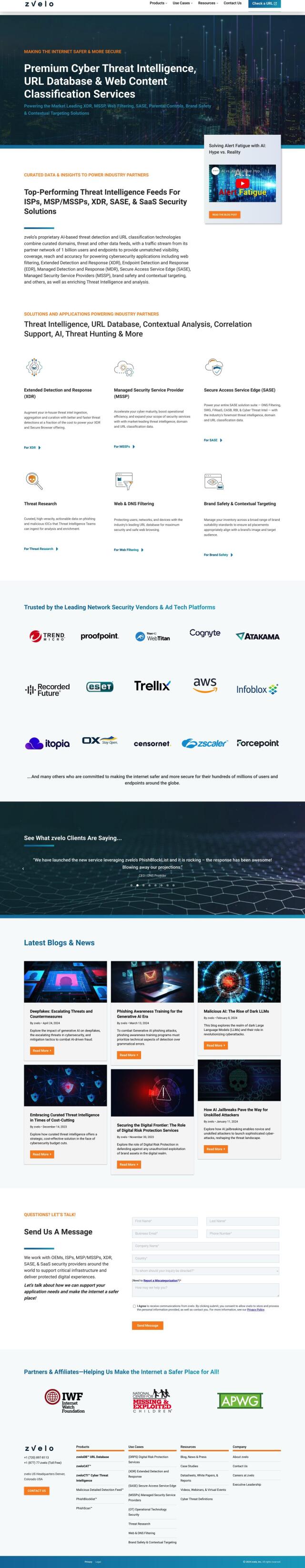
Darktrace
If you're looking for another alternative to Expel, Darktrace is a good option. It uses Self-Learning AI to detect and respond to in-progress cyber attacks in real-time, including ransomware and email phishing. The platform offers real-time threat detection, automated response, and native visibility across clouds, devices, and applications. This means it's flexible and can be scaled to meet the needs of any business.


Vectra AI
Another good option is Vectra AI, which offers AI-powered Attack Signal Intelligence to detect and respond to threats in real-time. It offers continuous protection across hybrid cloud environments, including public cloud services, SaaS applications, and endpoint security. With features like threat correlation and managed extended detection and response services, Vectra AI is designed to help improve SOC efficiency and lower cyber risk.


CrowdStrike
If you're looking for a more comprehensive cybersecurity solution, you should also check out CrowdStrike. This cloud-native platform offers advanced protection for endpoints, cloud workloads, identities, and data. It includes real-time identity protection, a next-gen SIEM, and a generative AI security analyst. CrowdStrike's solutions are highly rated by top industry analysts and you can try it for free for 15 days, so it's a good alternative to Expel.


Cybereason
Last, Cybereason offers an AI-Driven XDR platform that combines NGAV, EDR, and MDR to provide predictive prevention, detection, and response to modern attacks. It offers a single view of malicious activity and automates attack prediction and response, making it suitable for large-scale deployments. Cybereason's feature-rich product and multiple plans help to meet the needs of any business, so it's another good option to consider.