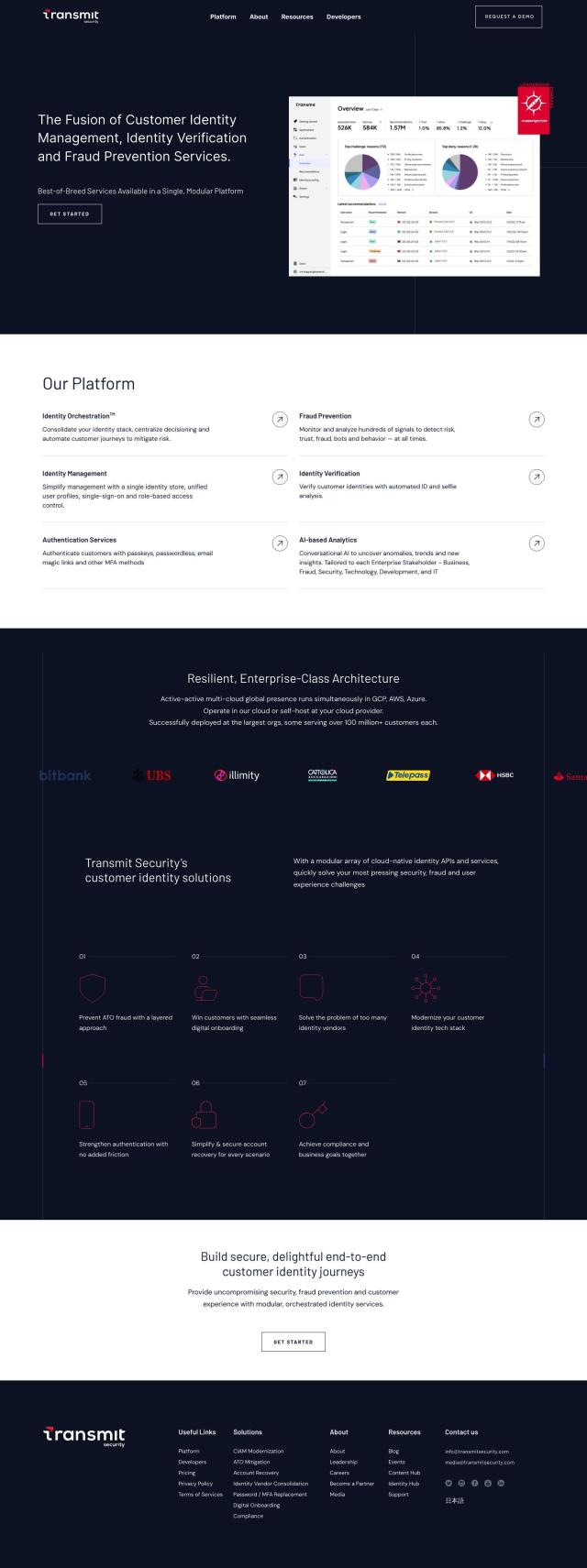
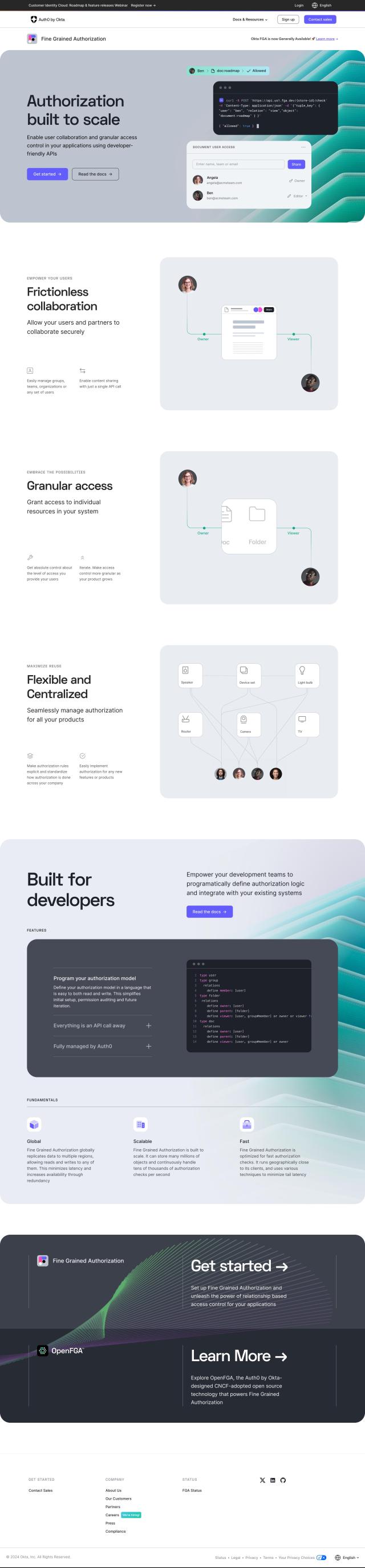
Question: How can I get a unified view of identity and access across my enterprise IAM and decentralized SaaS platforms?
Oleria
Oleria offers an end-to-end identity security solution by integrating identity silos across your enterprise IAM and SaaS platforms. It offers features such as real-time access usage visualization, fine-grained access visibility, and activity analysis. This information enables you to enforce least privilege principles, identify permission risks, and respond to incidents more quickly, all while maintaining centralized and adaptive access management.


BeyondTrust
BeyondTrust is another all-encompassing platform that offers a 360-degree view of all identities and privileges. It enables a zero-trust approach with complete privilege transparency, secure remote access, and intelligent threat detection and response. Its features and capabilities have been recognized in several industry reports, making it a powerful option for unified identity management and security.
SailPoint
SailPoint offers a unified identity security platform that integrates with multiple ecosystems to provide centralized access control and identity processes. With machine learning and AI, SailPoint offers real-time visibility into identities and access, streamlined identity processes, and pre-built integrations with many applications. This platform is designed to help you strengthen your identity security posture and maintain a secure environment.