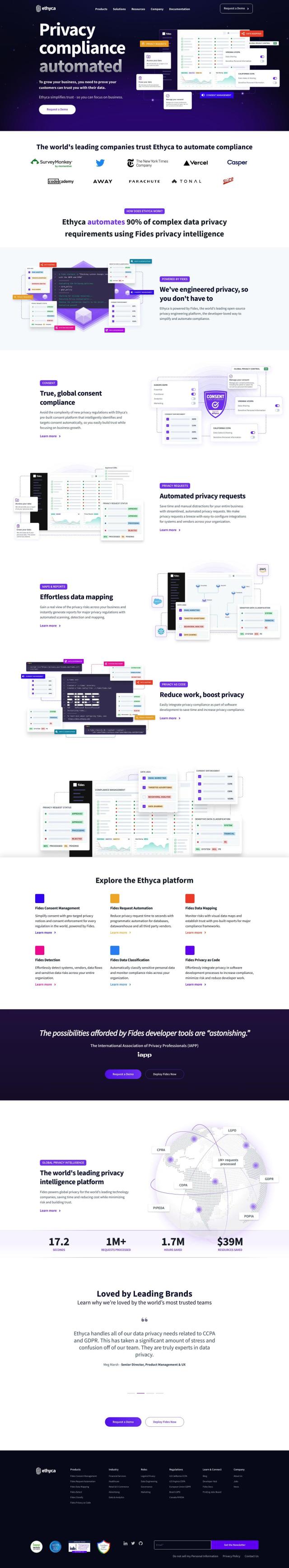
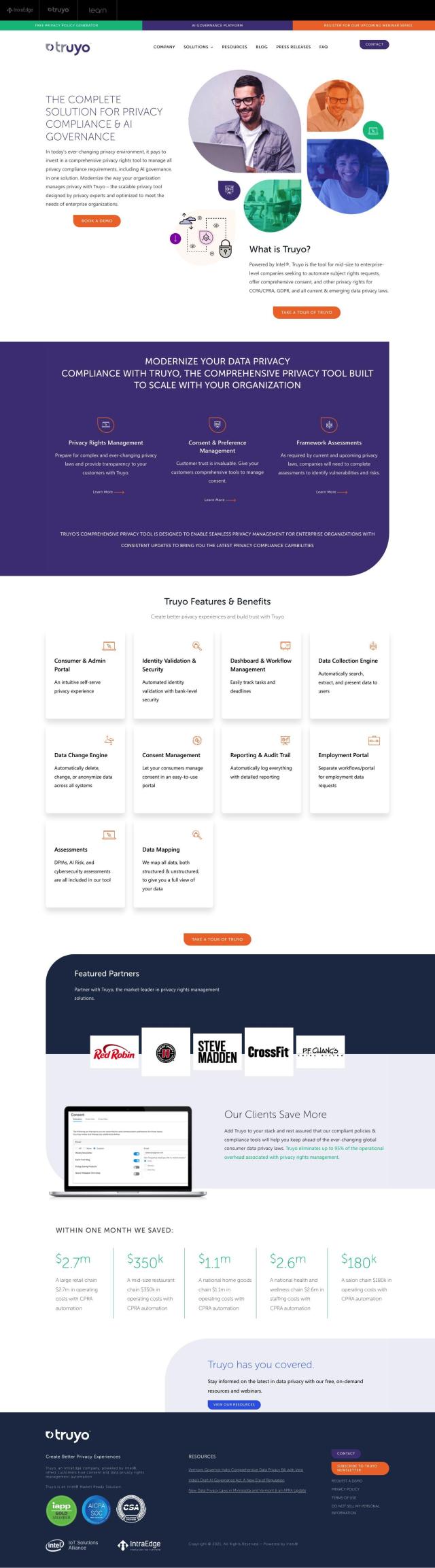
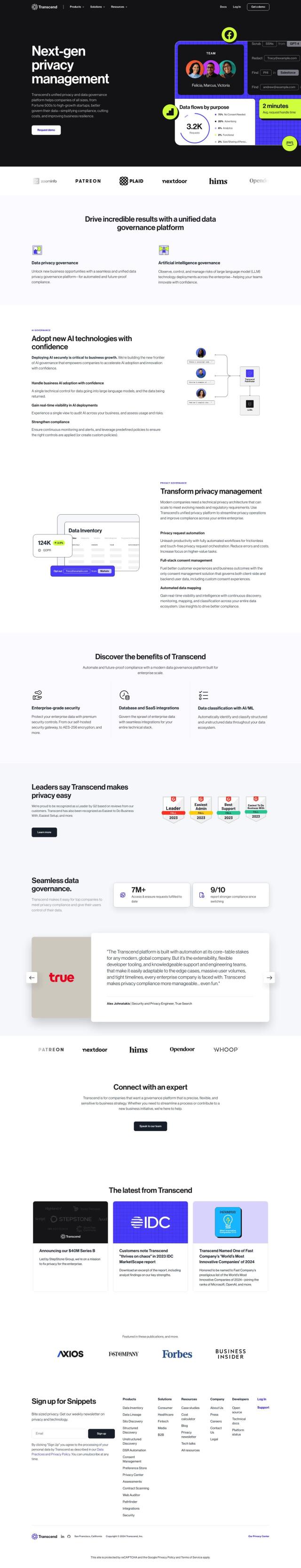
Question: Looking for a certification and monitoring platform that helps businesses establish trust and comply with regulations on the internet.
LegitScript
If you're looking for a certification and monitoring platform to help businesses establish trust and comply with regulations online, LegitScript is a good option. It's got a broad range of features, including merchant monitoring, marketplace monitoring and compliance services for different industries, like e-commerce marketplaces, search engines and social networks. LegitScript uses AI technology and machine learning to help businesses reduce risk and establish trust, and it can help them expand into new markets.


OneTrust
Another good option is OneTrust, a trust intelligence platform for managing privacy, data governance, security and ethics across an organization. It offers end-to-end data management with features like data discovery, enriched data context, risk assessment and compliance automation. OneTrust has a wide range of integration options so data management can be built into existing processes, and it can help organizations move beyond compliance and build trust with stakeholders.
TrustArc
TrustArc also offers a mature option for privacy and data governance. It offers automated tools for managing consent and consumer preferences, centralizes privacy work, and offers certifications to show a company's commitment to privacy. TrustArc helps companies comply with regulations like GDPR, CCPA and ISO/IEC 27001, and it can help companies maintain continuous compliance and build trust with customers.
Ketch
For privacy management spanning many systems and applications, Ketch is a good option. It automates data permissioning, consent management and data mapping, and it can help with regulations like GDPR and CCPA. Ketch's interface is designed to be easy to use, and pre-built templates for adaptive compliance mean non-technical people can use it. That means big productivity gains and fast onboarding.