Question: How can I simplify device security and access reporting for compliance requirements?
Swif
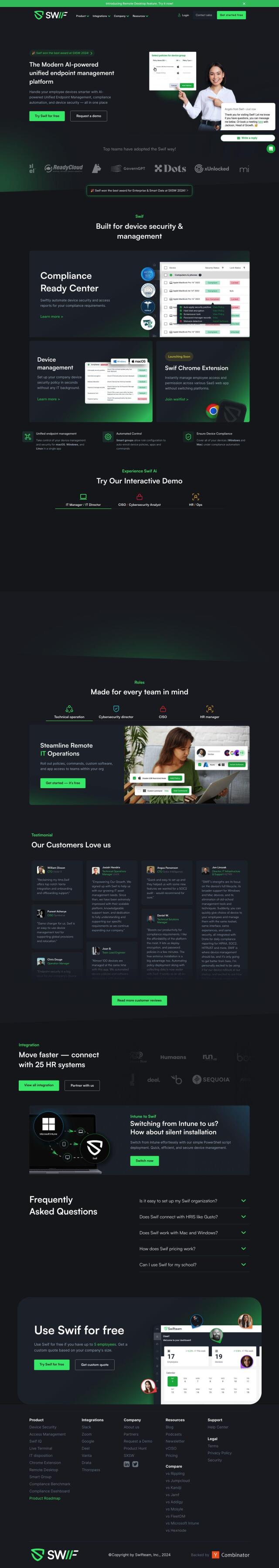
To make device security and access reporting easier for compliance, Swif also offers a GenAI-powered unified device management and compliance automation platform. That includes features like a Compliance Ready Center for generating security and access reports, device management for enforcing company security policies, and a Chrome extension for managing employee access and permissions to SaaS web apps. Swif also offers unified endpoint management for macOS, Windows and Linux computers and integrates with popular tools like Slack, Zoom, Google and Vanta, so it's a good option for IT managers and cybersecurity analysts.


CyberArk
Another good option is CyberArk, which offers a mature identity security and access management system. With features like secure Single Sign-On (SSSO), Adaptive Multi-Factor Authentication (MFA) and AI-powered privilege controls, CyberArk controls access to any device, anywhere. The platform spans a broad range of industries and offers flexible pricing, so it can be a good option for companies that want to improve their identity security posture and adopt a Zero Trust model.


BeyondTrust
If you want a more intelligence-infused approach, BeyondTrust offers a 360-degree view of all identities, privileges and access. Its platform offers secure remote access, identity threat detection and response and privilege protection at scale. It integrates with other tools, and BeyondTrust can help companies adopt a zero-trust model and comply with a range of security standards.

AccessOwl
If your focus is on access governance and SaaS management, AccessOwl is worth a look. It automates user account provisioning, access requests and reviews, and Shadow IT detection. AccessOwl centralizes employee access to multiple SaaS applications and ensures compliance with security standards like SOC 2 and ISO 27001. It's particularly good for fast-growing companies with complex SaaS app environments.