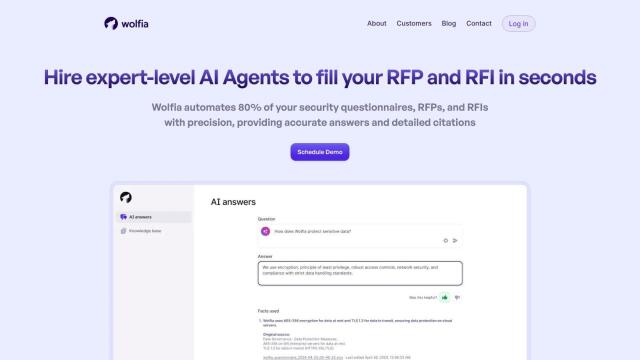
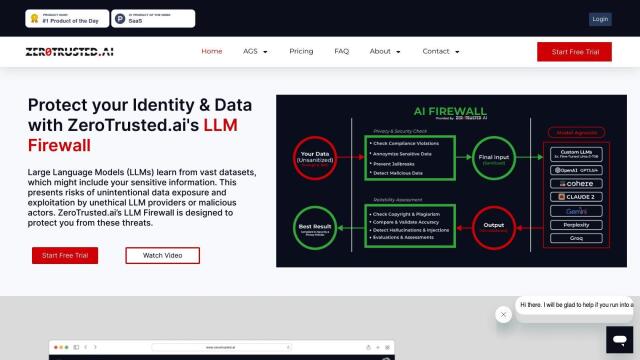
Question: Is there a solution that lets me create a security profile and share it with customers with full control over access?


Auditive
Auditive is an AI-powered third-party risk marketplace that streamlines security assessments for vendors and buyers. It lets you share your security posture with customers with a single click and monitor many vendors through a unified interface. With automated security assessments and continuous risk monitoring, Auditive can help you get your security in order and pass even the most demanding standards like SOC2.


Whistic
Another powerful option is Whistic, which automates vendor assessments and offers a unified Trust Center for security and compliance information. Its Frictionless Security Exchange feature lets you easily share your security posture, and it offers access to more than 40 questionnaires and frameworks. Whistic seeks to lower the risk of breaches and speed up sales, so it's a good option for third-party risk management.


Panorays
If you want more detailed, up-to-the-minute risk assessments, Panorays offers a full third-party cyber risk management platform. It assigns a real-time Risk DNA rating to each third-party connection and offers actionable threat alerts and continuous monitoring. The platform includes customizable templates for compliance and AI-powered risk assessments, so it's a good option for companies that want a more in-depth third-party risk management approach.