Question: Can you recommend a tool that helps me identify and map sensitive data flows across my systems?
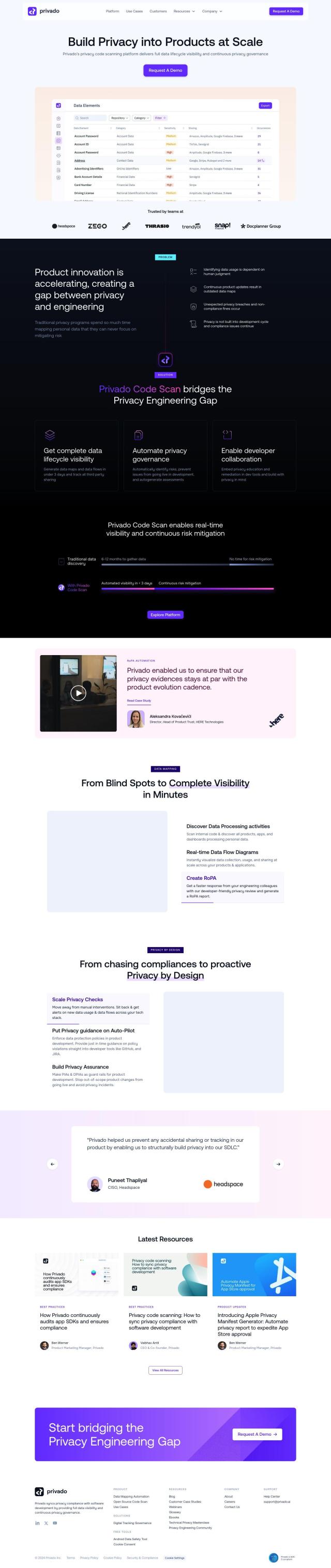
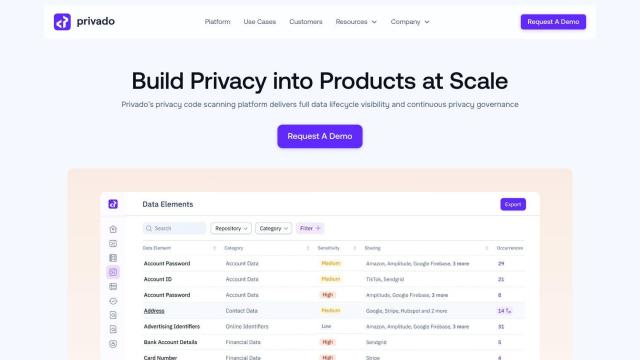
Privado
If you need a tool to find and map sensitive data flows across your environment, Privado is a great option. It provides end-to-end data lifecycle visibility and continuity privacy governance. Its features include data flow discovery, dynamic data mapping, automated risk discovery and real-time data flow diagrams. It can be integrated with existing source code management and CI/CD pipelines, and it's designed to ensure GDPR compliance and automate privacy governance.


Securiti
Another powerful option is Securiti, which offers a single pane of glass for data intelligence and control across hybrid multicloud environments. It includes data discovery, governance, data flow management, breach analysis and compliance checks with AI capabilities. This makes it a good option for complex data environments and for ensuring compliance with global regulatory requirements.


Nightfall
If you prefer an AI-native approach, Nightfall is designed to find, classify and protect sensitive data in SaaS and cloud applications. Its machine learning algorithms are designed to provide high accuracy and low false positives, reducing the risk of data breaches. Nightfall supports major compliance standards and can be deployed in minutes, making it a good option for real-time data security monitoring.


Varonis
Last, Varonis offers an all-in-one platform for automated data security, with data discovery, classification and threat detection across multiple environments. Its features include cloud DLP, UEBA and compliance management, making it a good option for organizations that need deep data visibility and automated remediation. Varonis supports multiple cloud platforms, so you can scale and save money for better data protection.