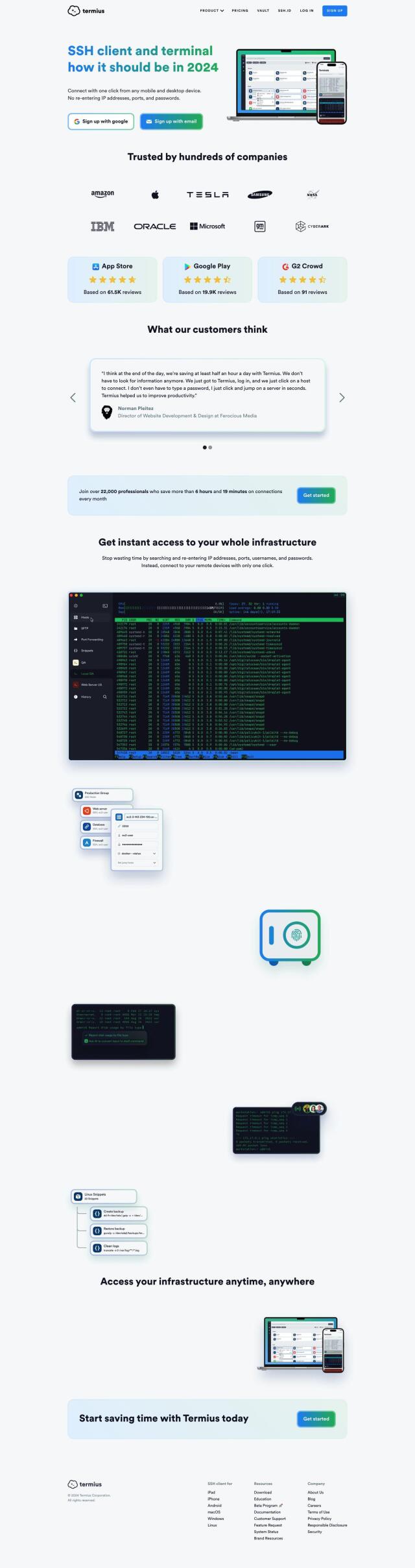
Question: Can you recommend a secure tunneling solution that allows me to access local servers from anywhere in the world?
Lokal
If you need a secure tunneling service to connect to local servers from anywhere, Lokal is another good choice. It uses Cloudflare's 310+ global edge locations to connect to local servers securely. Lokal supports TCP/UDP and has a GUI for sharing, debugging and development projects. It also has AI-powered help for tunnel traffic, code generation and question answering, so it's good for a variety of use cases.