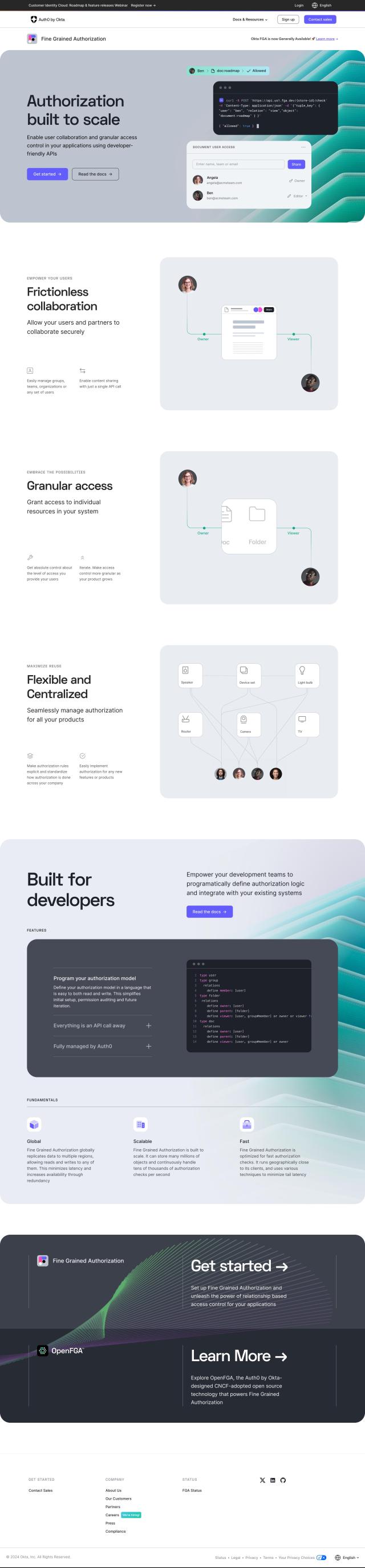
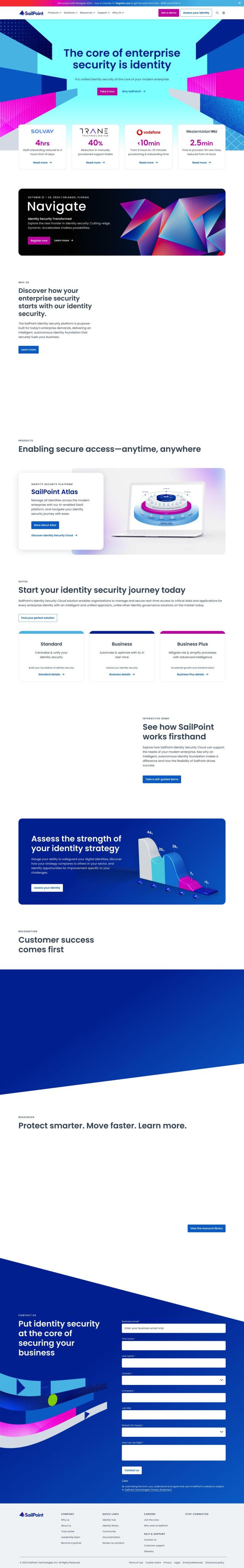
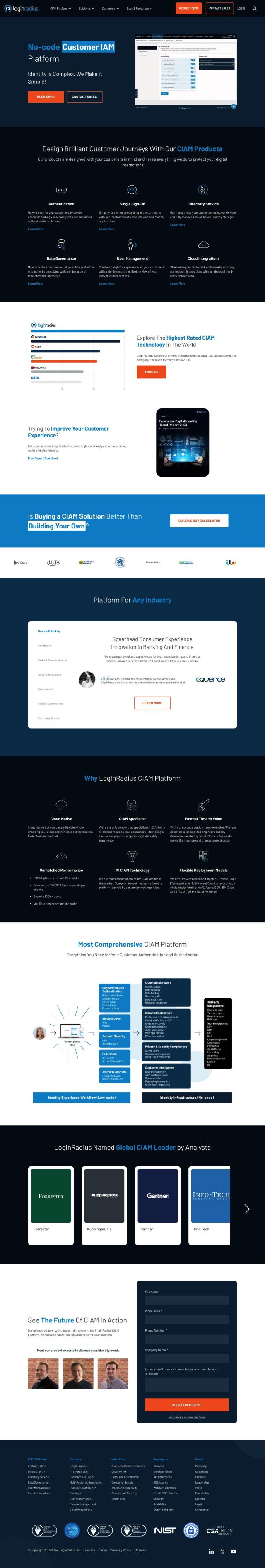
Question: I'm looking for a solution that provides secure, one-click access to all applications across devices and locations.


CyberArk
If you're looking for a comprehensive solution for secure, one-click access to all applications across devices and locations, CyberArk is a robust option. It offers a comprehensive identity security and access management solution with features like secure Single Sign-On (SSSO), Adaptive Multi-Factor Authentication, and lifecycle management. CyberArk also boasts intelligent privilege controls and extensive integration capabilities, making it suitable for a wide range of industries.
QuickLaunch
Another excellent choice is QuickLaunch, an AI-driven identity and integration platform. QuickLaunch provides centralized, one-click secure access to all applications with features such as single sign-on, adaptive authentication with MFA, and passwordless authentication. It also offers identity lifecycle management and customizable solutions for various industries like education and healthcare, improving user experience and security.


BeyondTrust
For a more advanced approach, consider BeyondTrust. This intelligent identity and access security platform provides a 360-degree view of all identities and privileges, offering secure remote access, identity threat detection, and dynamic access control. Its zero-trust approach and extensive integrations make it suitable for various use cases, including cloud security and endpoint protection.