Question: I need a way to provide secure and simplified access to company resources and information for all employees, regardless of location or device.


CyberArk
If you need a broad identity security and access management system, CyberArk is a good choice. It offers access to any device anywhere with AI-based features like Single Sign-On, Adaptive Multi-Factor Authentication, and intelligent privilege controls. The system spans many industries, and the company offers flexible pricing, so it's a good pick for organizations that want to lock down their identity security posture with a Zero Trust approach.


BeyondTrust
Another good option is BeyondTrust, which offers a 360-degree view of all identities and privileges. Its features include secure remote access, threat detection and response, full privilege transparency and a zero-trust approach. It's good for organizations that want to integrate with a variety of tools and systems for unified control and visibility across the full identity estate.
SailPoint
SailPoint offers a unified identity security platform that uses machine learning and AI to provide real-time insights and automated decision-making. It offers centralized access control and real-time visibility into identities, streamlining identity processes and ensuring the right people have access to critical resources while keeping the environment secure.
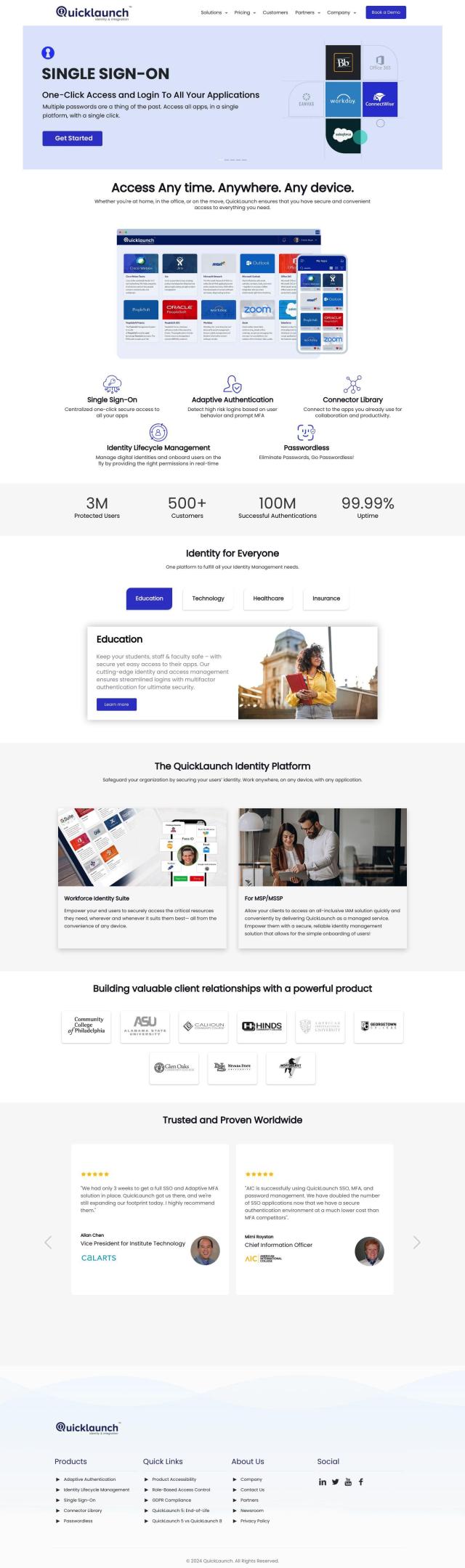
QuickLaunch
If you want an AI-based option, QuickLaunch offers centralized, one-click secure access to all applications across devices and locations. It includes single sign-on, adaptive authentication and passwordless authentication, making it a secure and easy-to-use option for industries like education and health care.