Question: How can I protect my mission-critical systems and data from cyber threats with a comprehensive digital security solution?


SentinelOne
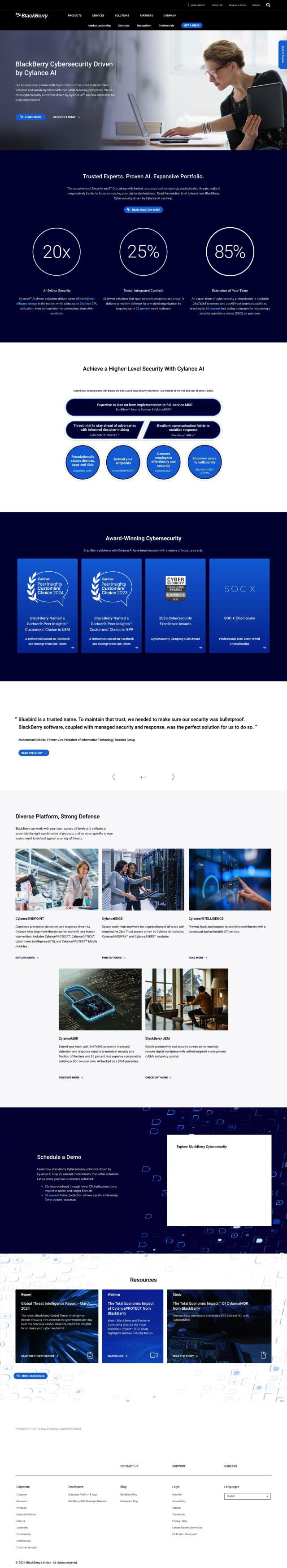
To protect your mission-critical systems and data from cyber threats, SentinelOne provides a comprehensive cybersecurity AI platform for endpoint, cloud, identity and data protection. Its capabilities include next-gen EPP, EDR and XDR, real-time cloud workload protection, identity threat detection and a Security Data Lake for real-time insights. It also offers 24/7 threat hunting and managed services, giving you a trusted partner for streamlined and powerful cybersecurity.


CrowdStrike
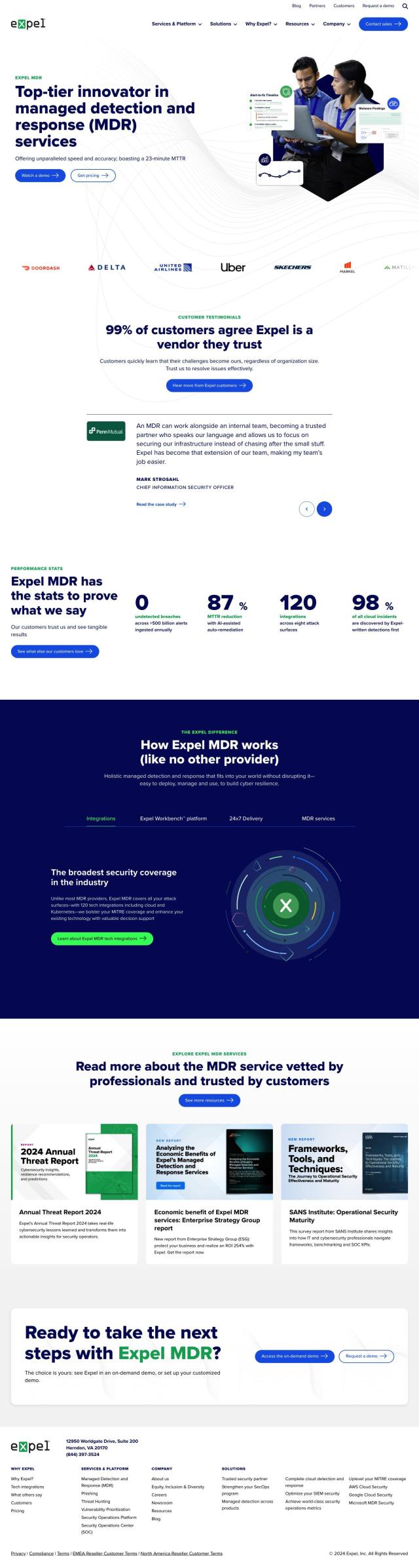
Another top contender is CrowdStrike, a cloud-native cybersecurity platform that protects endpoints, cloud workloads, identities and data. It includes real-time identity protection, a next-gen SIEM for threat visibility, and controls like antivirus, USB device control and host firewall management. CrowdStrike is a top performer in cybersecurity incident response and cloud workload security, and you can try it with a 15-day free trial to get started and test it out.


Cybereason
For a more AI-centric approach, Cybereason offers an AI-Driven XDR platform that combines NGAV, EDR and MDR to predictively prevent, detect and respond to advanced threats. It includes MalOp Detection, NGAV and Endpoint Controls, making it a good fit for enterprises that need to defend against today's sophisticated attacks. The platform is designed to scale to very large deployments, with a range of plans to accommodate different business needs.


Darktrace
Last, Darktrace uses Self-Learning AI to detect and respond to in-progress cyber attacks in real-time. It offers real-time threat detection, contextual understanding and automated response for cloud, email, endpoint and network security. This flexible and scalable solution is good for companies of any size, and can be used in conjunction with other tools to add an extra layer of protection.