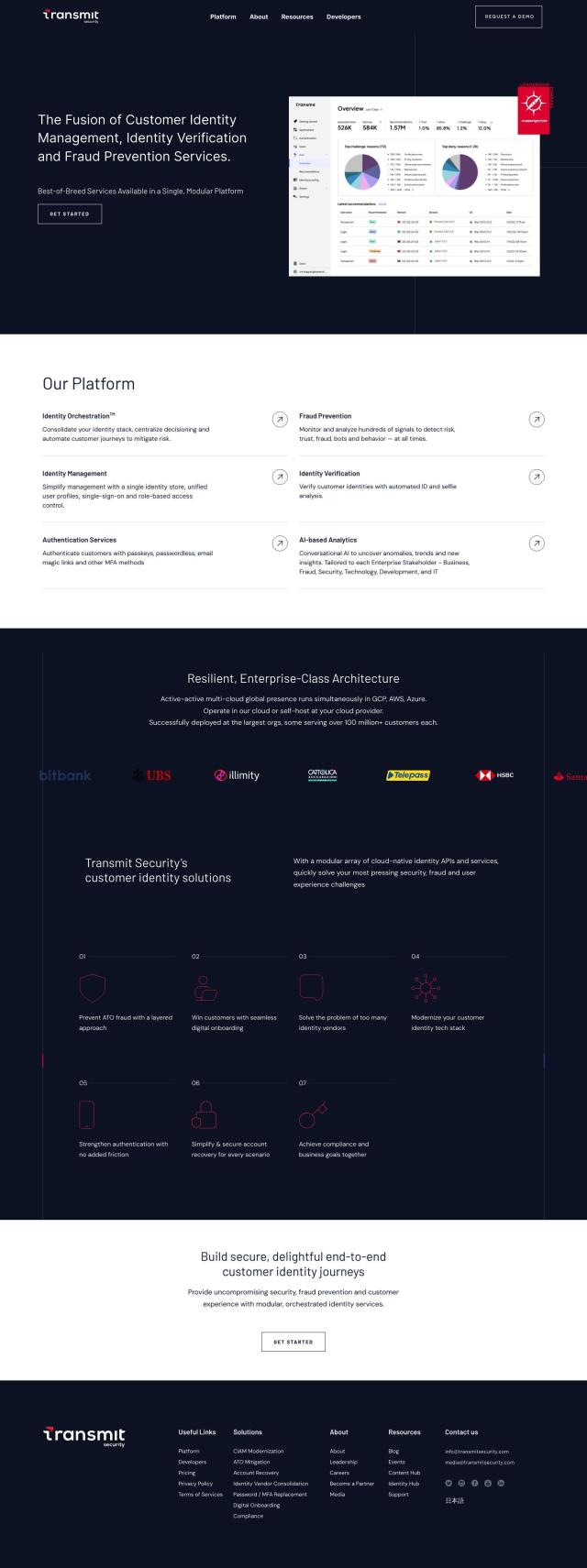
Question: I'm looking for a platform that can help prevent outages and misuses of machine identities in cloud-native applications.
Venafi
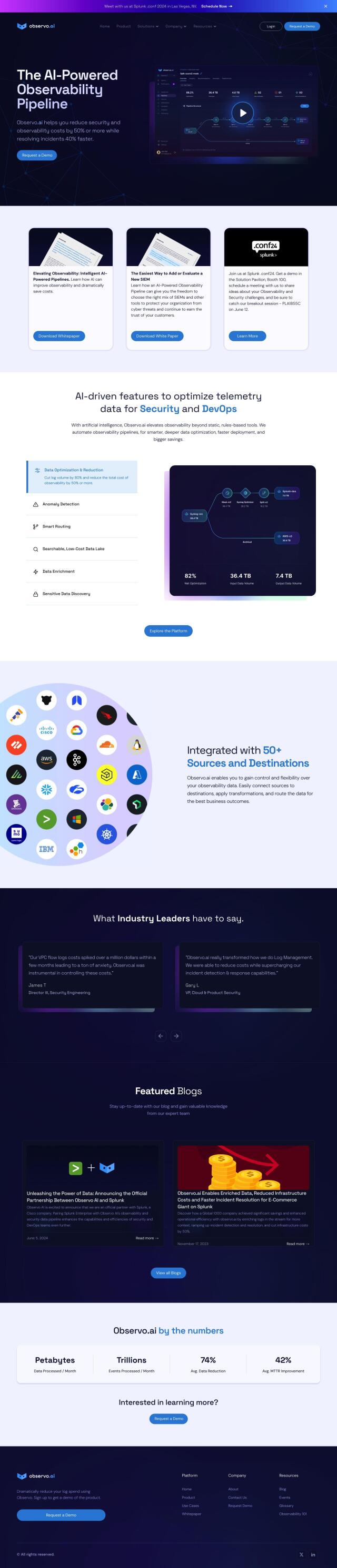
If you're looking for a platform to help prevent outages and misuses of machine identities in cloud-native applications, Venafi is a top choice. Venafi offers a comprehensive machine identity management platform designed to simplify complexity and eliminate outages across multiple platforms. The platform includes features like TLS Protect, SSH Protect, CodeSign Protect, and more, which can automate certificate provisioning, prevent misuses, and ensure total observability and security for machine identities. It's used by leading organizations and is available for a free trial, making it a scalable and robust solution.


Aqua
Another notable option is Aqua, a full cloud-native security platform that integrates with container platforms such as Kubernetes and Docker. Aqua protects cloud native applications from attacks throughout the software development lifecycle, with features like event-based scanning, genAI security, and automated devsecops. It supports environments on AWS, Google Cloud, OpenShift, and more, making it a versatile choice for comprehensive cloud security.


CyberArk
For a more targeted approach to identity security, consider CyberArk. CyberArk provides secure access to any device with AI-driven identity security and access management. The platform includes secure Single Sign-On, Adaptive Multi-Factor Authentication, lifecycle management, and more. It supports a wide range of industries and offers flexible pricing, making it a strong option for organizations adopting a Zero Trust approach.


Akeyless
Lastly, Akeyless offers secure secrets management using Distributed Fragments Cryptography (DFC). It provides features such as automated credential rotation, just-in-time credentials, and secure Kubernetes secrets management, which ensure zero-knowledge encryption and eliminate single points of breach. Akeyless integrates with many tools and platforms, making it easy to deploy and scale securely.