Question: Is there a search engine that can help me monitor network exposure and identify potential security risks?
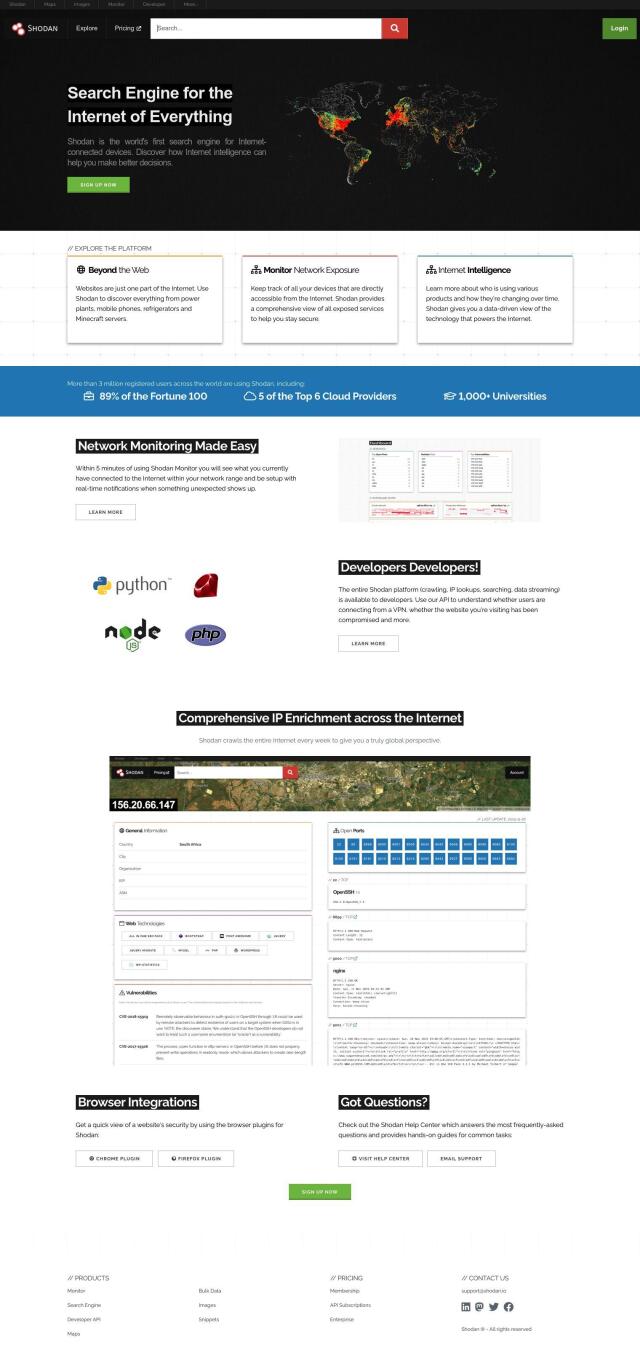
Shodan
If you want a search engine to keep an eye on network exposure and warn you of potential security problems, Shodan is a good choice. It can monitor networks in real time and issue alerts, enrich IP addresses with other information, and offer a developer programming interface for more detailed information about exposed services. Shodan also has a graphical interface for exploring devices and seeing geo-location information and historical activity.


Tenable
Another broad platform is Tenable, which offers a range of products for vulnerability management, cloud security and operational technology (OT) security. Tenable offers real-time vulnerability assessments, exposure metrics and attack path analysis to help you prioritize and remediate cyber risks across your full attack surface.


UpGuard
For continuous monitoring and real-time scanning, UpGuard is useful. It offers automated scanning, evidence analysis and real-time alerts through integration with tools like Jira and Slack. UpGuard also offers data leak detection and industry-leading security ratings to help you make informed security decisions.


Recorded Future
And Recorded Future offers a threat intelligence platform to help you find and respond to risks in many different areas. It offers real-time intelligence from the dark web and open web, along with automated security workflows and exposure management features to help you improve your overall security posture.