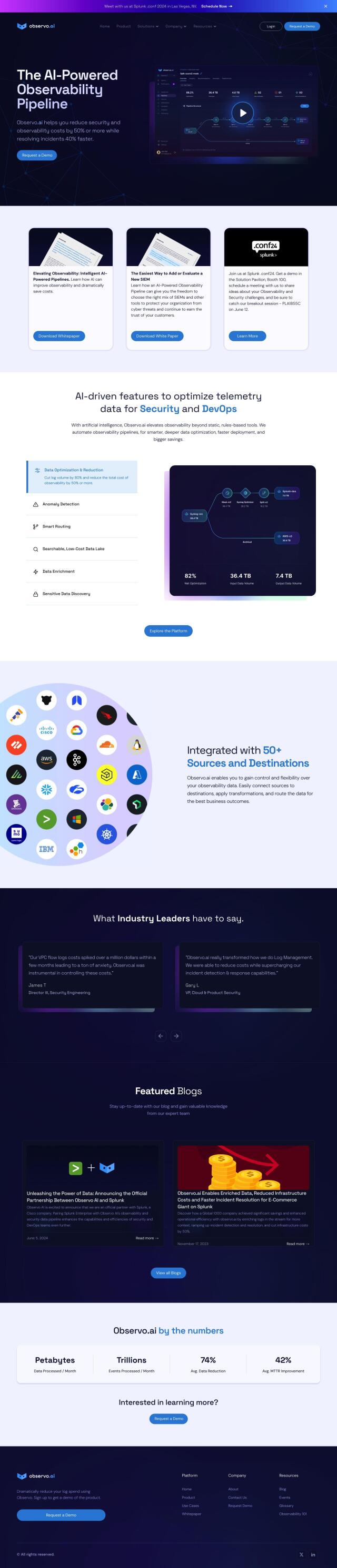
Question: Do you know of a tool that can provide total observability and security for machine identities and automate certificate provisioning?
Venafi
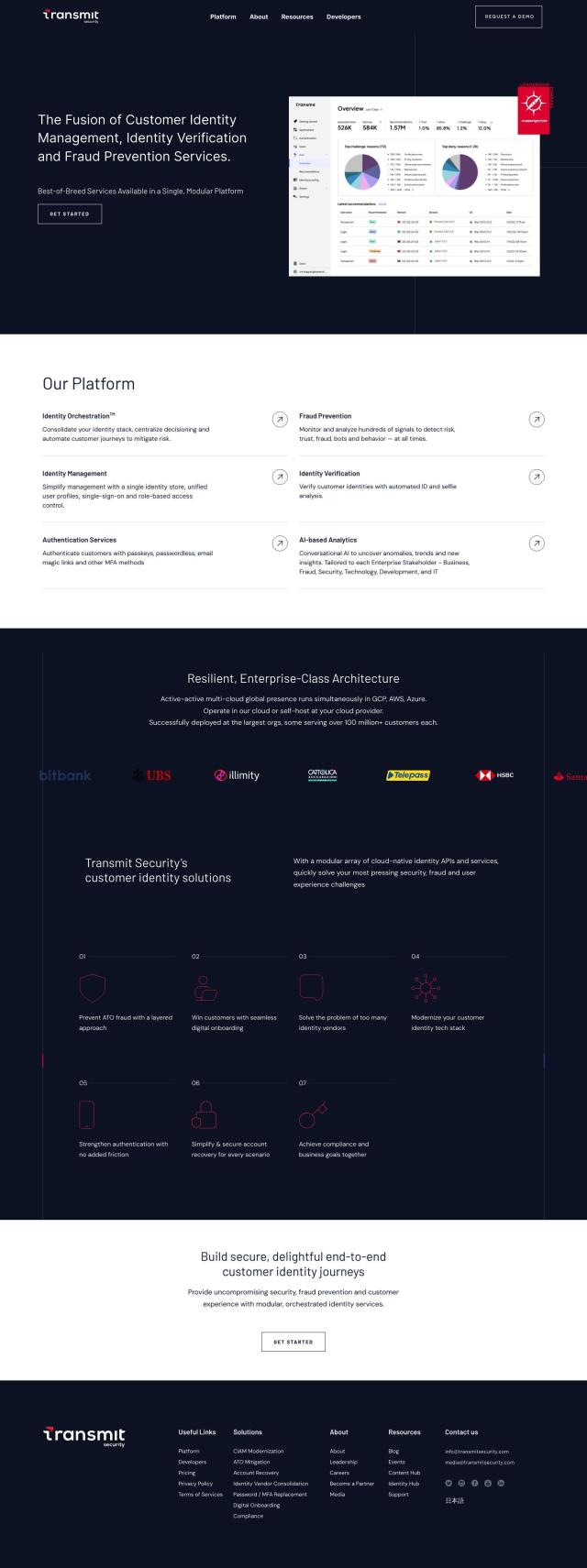
If you're looking for a tool that offers full observability and security for machine identities and automates certificate provisioning, Venafi is a great option. Its machine identity management platform offers a unified platform for managing machine identities across multiple platforms, reducing complexity, eliminating outages and automating certificate provisioning. With TLS Protect, SSH Protect and CodeSign Protect, Venafi offers zero outages and can provision certificates up to 98% faster, resulting in a significant reduction in time and costs. It's used by many of the world's largest organizations and offers a free trial.


CyberArk
Another option is CyberArk, which offers end-to-end identity security and access management. With features like secure Single Sign-On, Adaptive Multi-Factor Authentication and lifecycle management, CyberArk protects both human and machine identities. It includes intelligent privilege controls, flexible identity automation and broad integrations, making it adaptable to a wide range of industries and compliance needs. CyberArk also supports a Zero Trust approach, which can help improve your security posture.


Akeyless
If you need a cloud-native option, Akeyless offers a secure secrets management platform. It uses Distributed Fragments Cryptography (DFC) to generate encryption keys, which means zero-knowledge encryption and no single points of breach. Akeyless includes features like automated credential rotation, just-in-time credentials and secure Kubernetes secrets management, making it highly scalable and cost-effective. It also integrates with many tools and platforms, making deployment easy.


BeyondTrust
Also worth considering is BeyondTrust, which offers a 360-degree view of all identities, privileges and access. It includes full privilege transparency, secure remote access and intelligent threat detection. BeyondTrust integrates with many systems to support a zero-trust approach and offers unified control and visibility across the entire identity estate. It supports a wide range of use cases, including cloud security, compliance and identity threat detection and response.