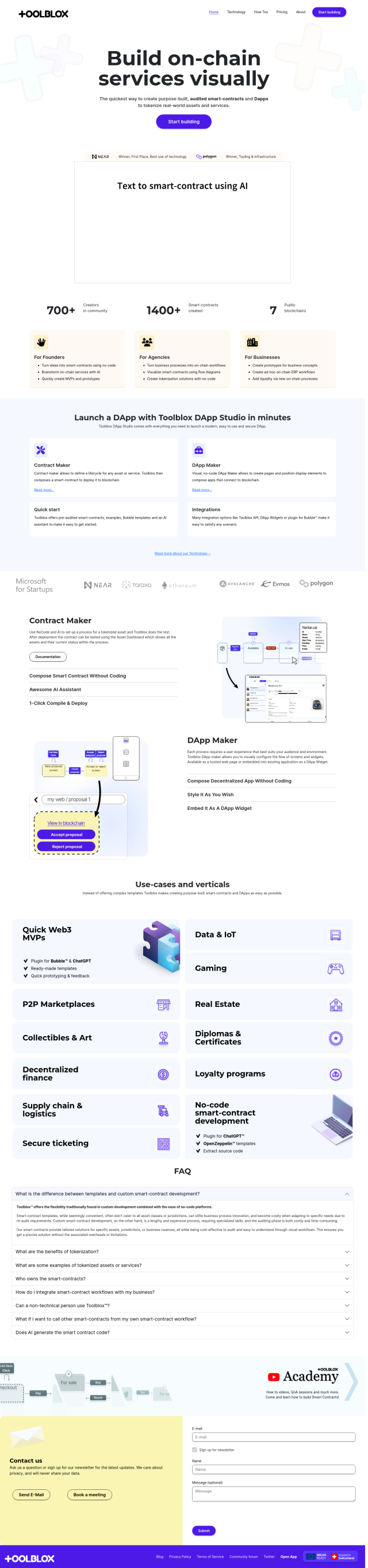
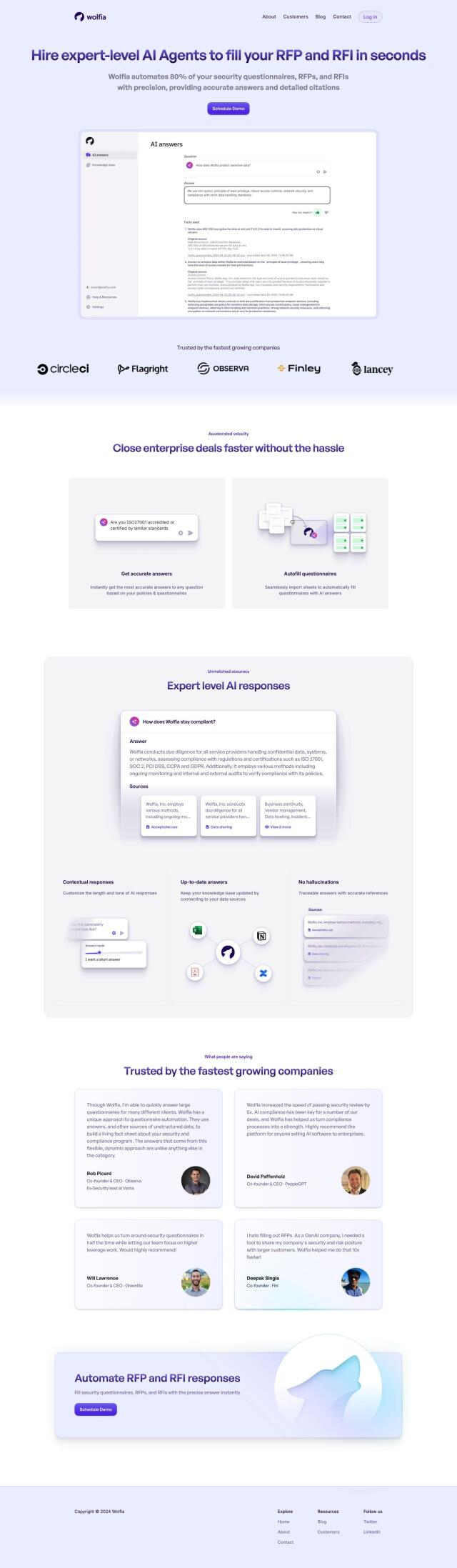
Question: Is there a utility that can help me identify recent transactions to centralized exchanges in case of a wallet hack?
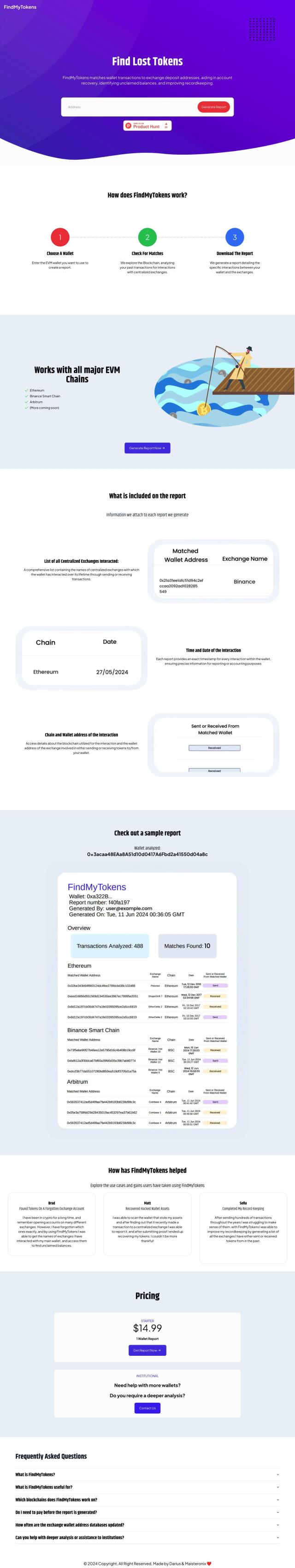
FindMyTokens
If you're worried about tracing recent transactions to centralized exchanges in case your wallet is hacked, FindMyTokens could be a useful utility. The system, designed to help you recover lost tokens by matching wallet transactions to exchange deposit addresses, produces a detailed report of interactions with centralized exchanges, including timestamps and blockchain and wallet addresses. FindMyTokens supports EVM Chains like Ethereum and Binance Smart Chain and offers two pricing tiers for individual and institutional customers.
Web3 Antivirus
Another tool worth evaluating is Web3 Antivirus. This free, open-source browser extension offers a range of security features, including transaction simulation and proactive phishing protection. It blocks users from signing malicious transactions and interacting with potentially malicious assets and phishing websites. It only supports Ethereum transactions for now, but plans to expand to other chains, and offers more protection with a large website blocklist.
Lossless Aegis
If you're a business looking to step up your security, Lossless Aegis could be a good fit. This business-to-business tool monitors blockchain transactions in real time and uses predictive analytics to spot suspicious activity. It can help you spot potential problems before they become problems, which makes it a good choice for institutional security.