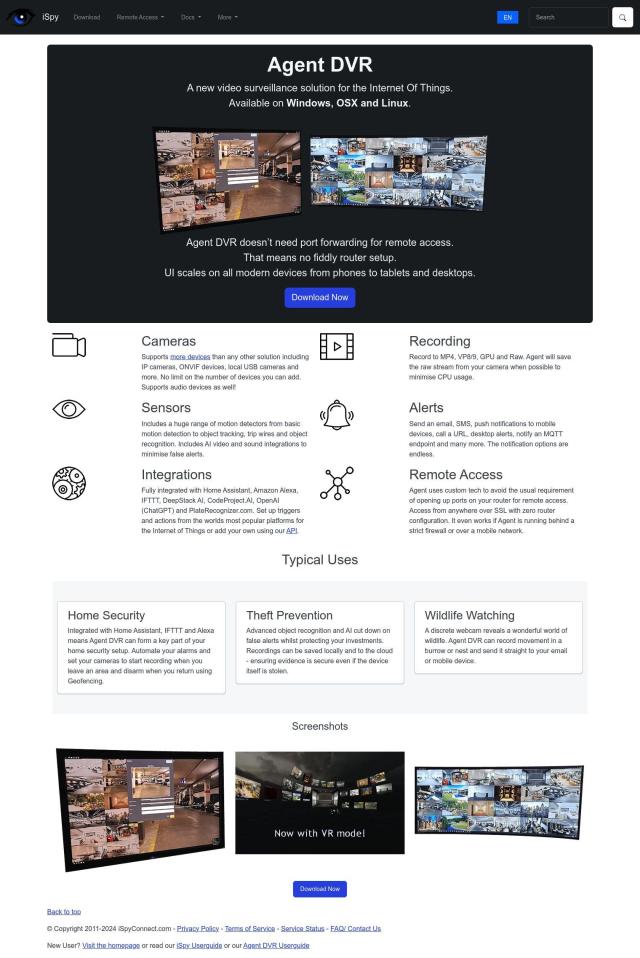
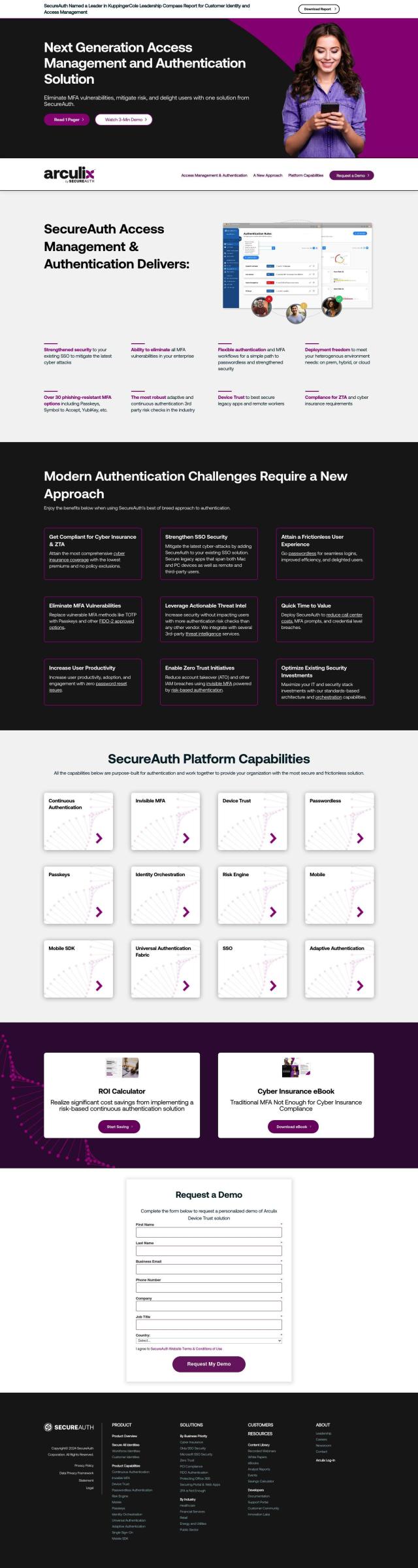
Question: I need a solution that allows me to access my Home Assistant from anywhere, using my phone or laptop, with end-to-end encryption.
Nabu Casa
If you want a service that lets you access Home Assistant from anywhere with your phone or laptop, using end-to-end encryption, Nabu Casa is another good option. Nabu Casa offers cloud-based remote access to Home Assistant for Android, iPhone, Apple Watch and Wear OS devices. It protects data with end-to-end encryption and can be integrated with popular voice assistants like Google Assistant and Amazon Alexa. The service offers a one-month free trial period, after which you'll pay a monthly subscription fee depending on your country.
Auth0
Another option is Auth0, an authentication and authorization service. It doesn't offer direct remote access to Home Assistant, but it has strong security features like Universal Login, Single Sign On, Multifactor Authentication and encrypted communication. It can be integrated with your application to handle access control, which could be useful if you're looking for a more complete security service.


Zero Networks
If you need more security and remote access, Zero Networks offers a fully automated service that's geared for microsegmentation and secure remote access for zero trust segmentation. It offers agentless and multifactor authentication, and secure remote access that combines the speed of VPNs with the security of Zero Trust Network Access. It's designed to stop ransomware attacks and block access to sensitive assets, too, so it's a good option if you want to lock down your network.
Infinipoint
Last, Infinipoint offers a Zero Trust Access Platform that continuously verifies user identity and device compliance for access. It offers phishing-resistant passwordless and multi-factor authentication and full device posture verification. The service can be used to control device access, enforce zero trust device posture and block account takeovers and weak device posture attacks, so it's a good option if you want to secure your remote access.