Question: How can I detect and respond to insider threats and suspicious user behavior in my SaaS ecosystem?
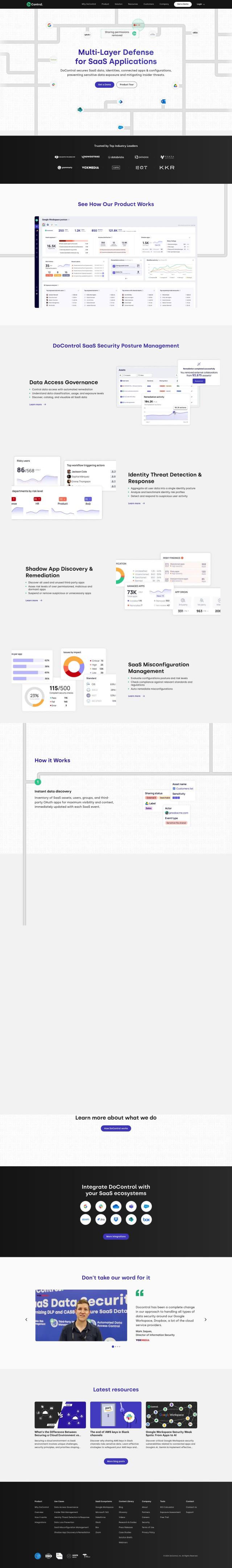
DoControl
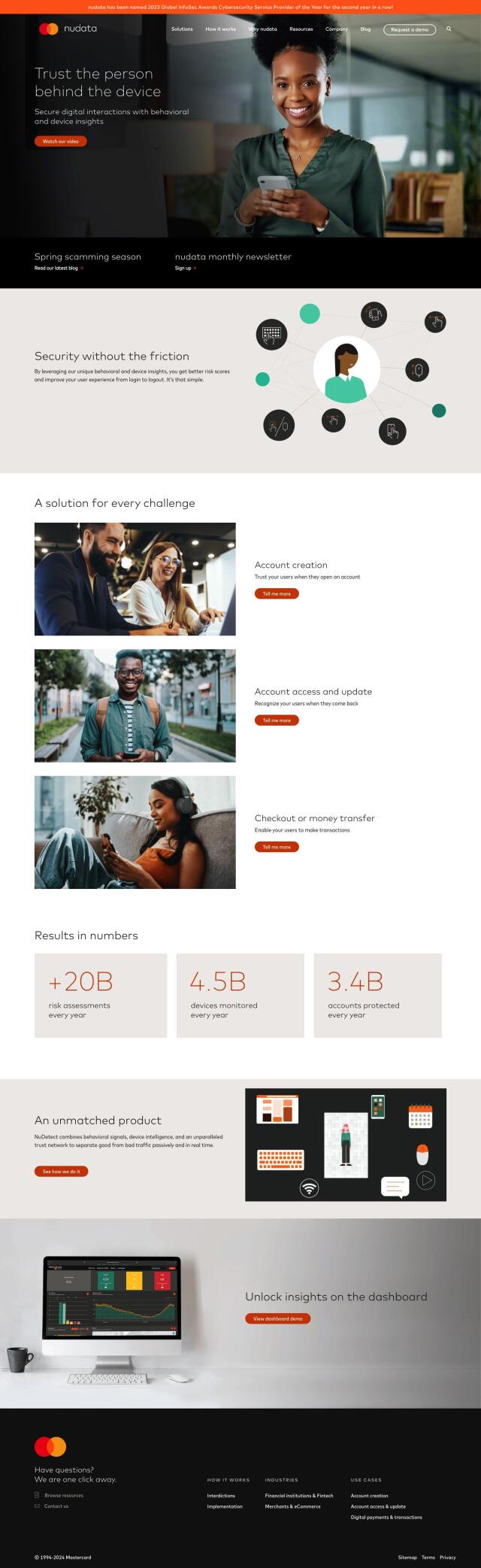
If you need to monitor and respond to insider threats and other suspicious user activity in your SaaS environment, DoControl is a good option to evaluate. It provides end-to-end visibility, threat detection and automated remediation for a range of SaaS apps like Google Workspace, Microsoft 365 and Salesforce. With features like data access governance, identity threat detection and shadow app discovery, DoControl can help protect sensitive data and prevent breaches. It also lets employees self-remediate risky behavior so security teams can focus on higher-level work and improve overall SaaS security posture.


Vectra AI
Another good option is Vectra AI, which uses AI-powered Attack Signal Intelligence to monitor for and respond to threats in real time. It monitors hybrid cloud environments, including public cloud, SaaS apps, identity, network and endpoint security. Vectra AI offers managed extended detection and response services that can help reduce alert noise and improve the efficiency of your security operations center. So it's a good option for companies that want to improve threat detection and response.
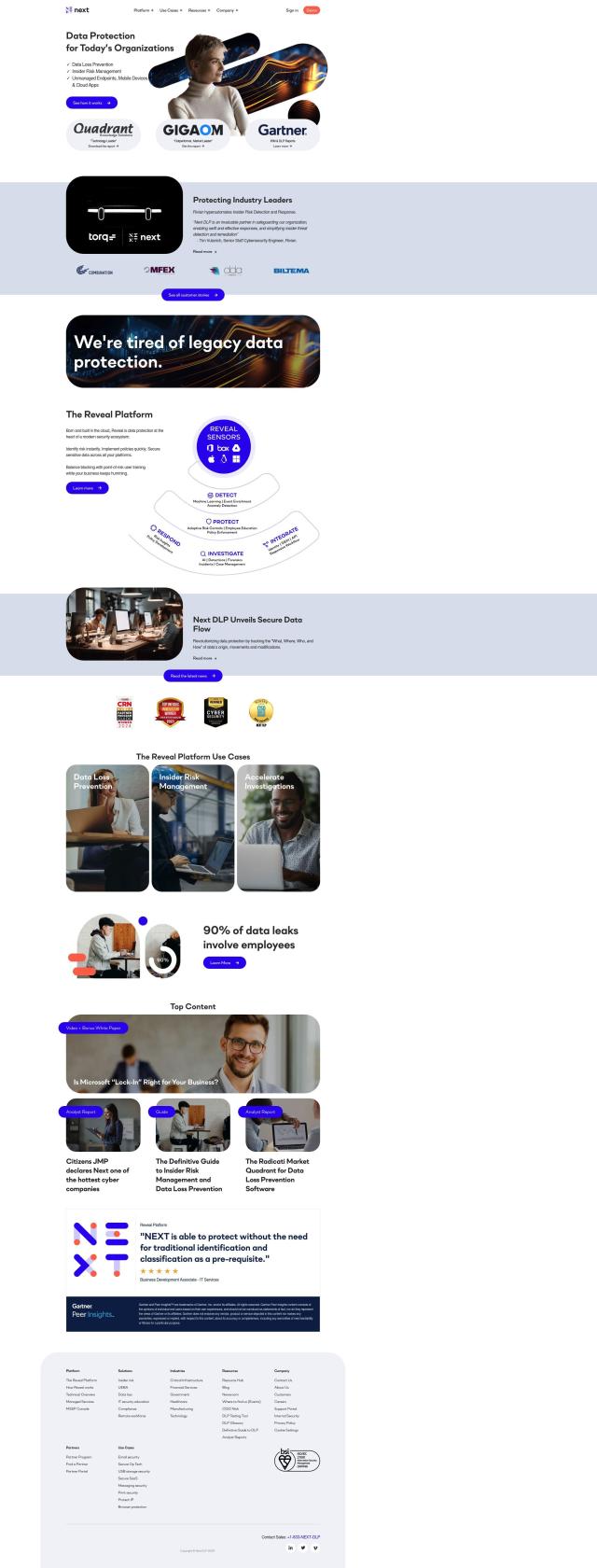

Next DLP
For a cloud-native option geared specifically to insider risk and data protection, Next DLP offers a mature platform for data loss prevention across endpoints, mobile devices and cloud applications. Its AI-powered features monitor for threats and score anomalous activity sequences, and it can coach employees in real time to stop data exfiltration. It's a good option for companies that have sensitive data, like finance and health care.


Varonis
Last, Varonis offers an all-in-one SaaS platform for automated data security, including data discovery and classification, threat detection and policy automation. It spans multiple cloud and on-premises environments and offers features like DSPM, AI security and UEBA to give you real-time visibility and proactive threat detection. Varonis is a good option for companies that need to get a better handle on their data and automate remediation.