Question: I'm looking for a platform that offers continuous authentication and risk assessment to reduce cybersecurity risks.
Arculix
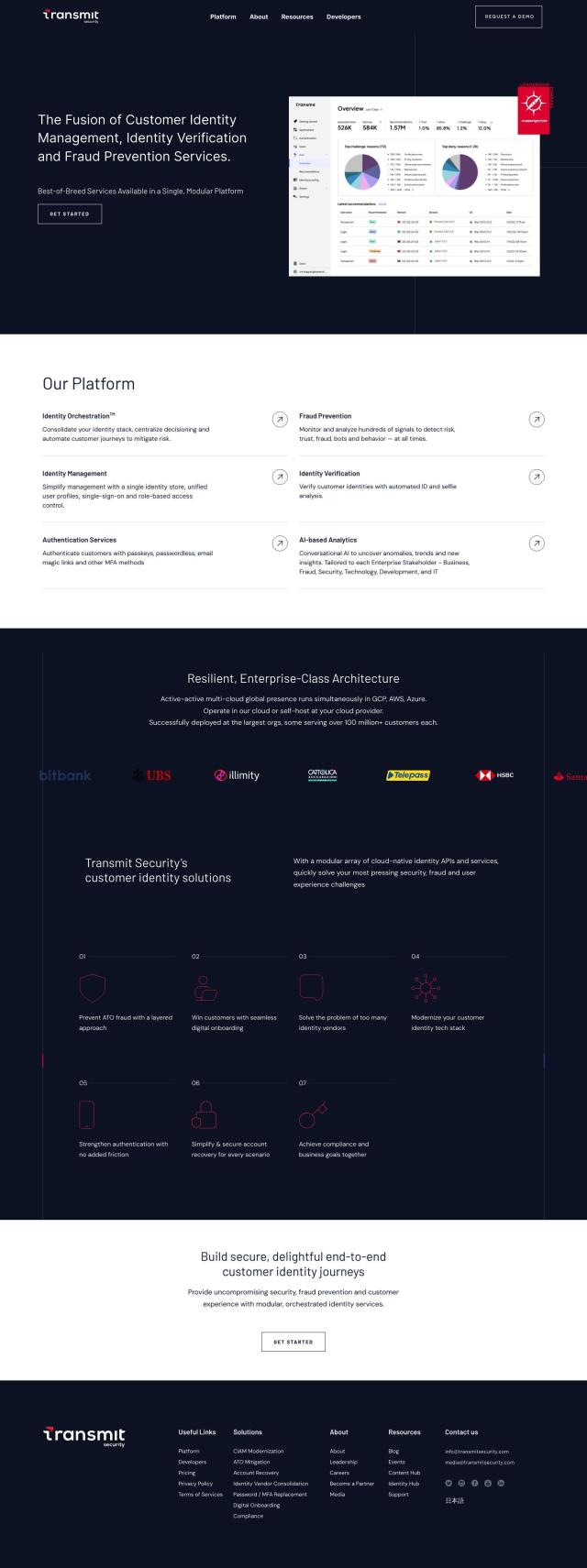
For continuous authentication and risk assessment to minimize cybersecurity risk, Arculix is a strong contender. It's a next-gen access management platform that uses machine learning for continuous authentication, invisible MFA, device trust and more than 30 phishing-resistant MFA options. The platform can be used for a variety of use cases, including cyber insurance compliance, SSO security, passwordless authentication and threat intel, all while maintaining a seamless user experience.
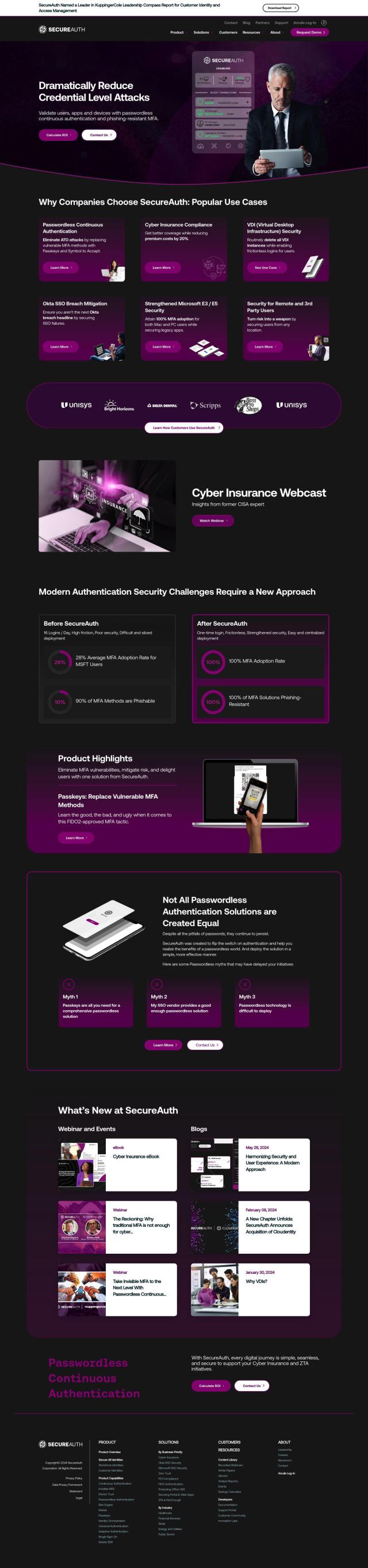
SecureAuth
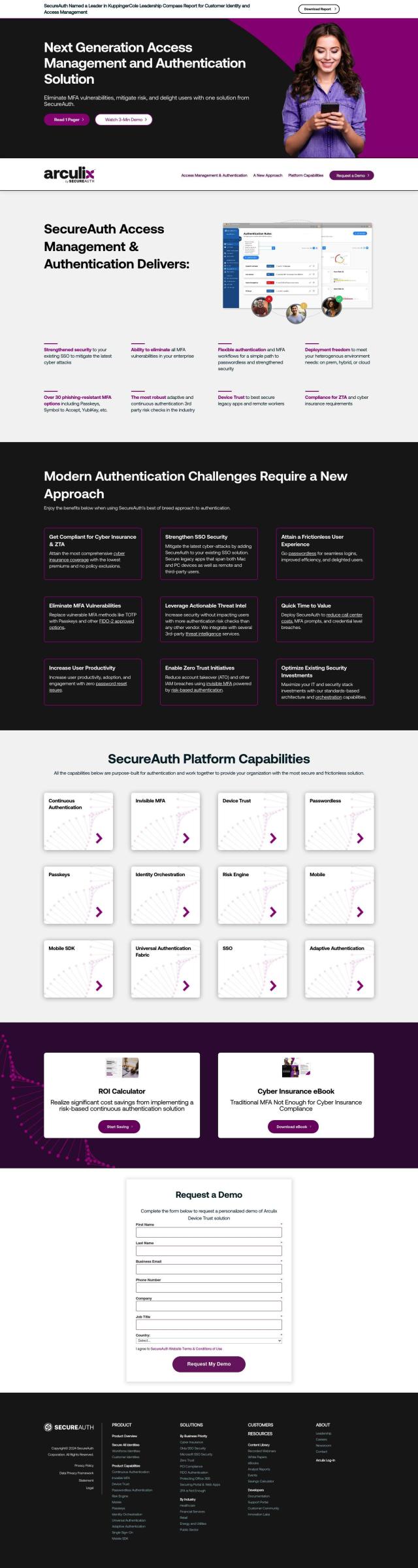
Another strong contender is SecureAuth, which offers passwordless continuous authentication. It includes features such as invisible MFA, device trust, passwordless authentication with Passkeys and FIDO2-approved options, and a risk engine. SecureAuth can be used for a variety of use cases including cyber insurance compliance, VDI security and remote user security to help organizations prevent credential-level attacks and improve their overall security posture.


IBM Security Trusteer
For a cloud-based option, IBM Security Trusteer offers real-time fraud detection, identity risk assessment and compromised device detection. It uses AI and machine learning to continuously assess user behavior for fraud risk, giving a seamless customer experience while minimizing the risk of unauthorized access. Trusteer solutions protect digital logins and transactions, and its cloud-based platform is designed to be scalable and agile.
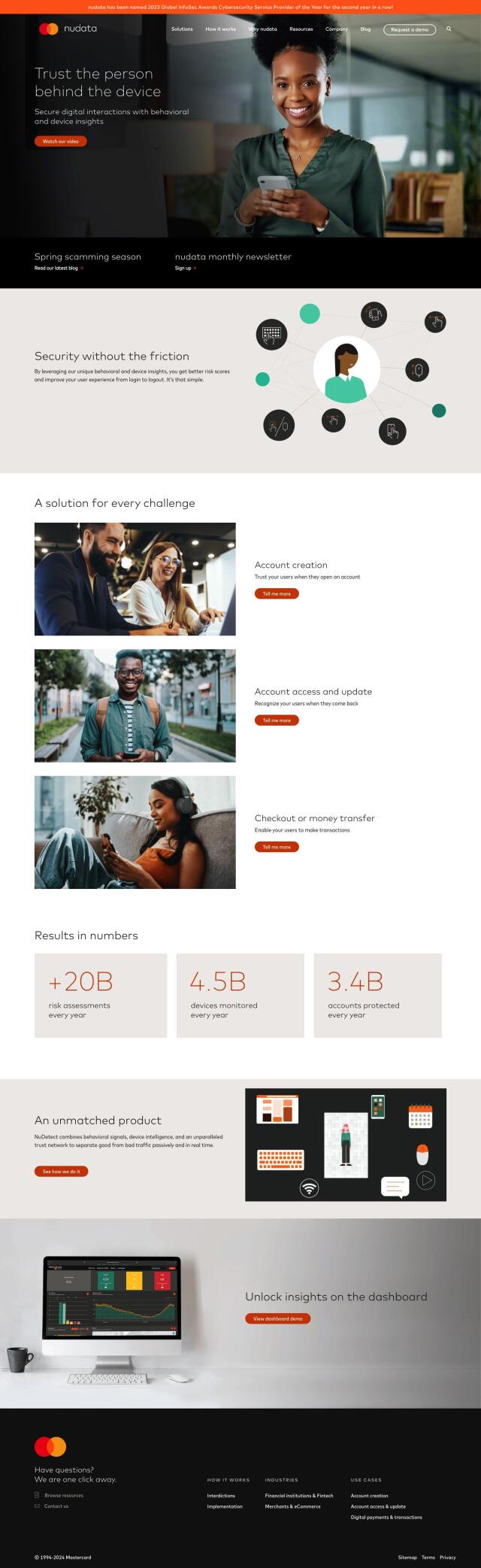
nudata Security
Last, nudata Security combines behavioral biometrics, device insights and a proprietary trust network to continuously assess user behavior. It offers accurate risk scores and a seamless user experience without compromising security. This platform is particularly useful for financial institutions, fintech companies and eCommerce businesses that need to balance security and user experience.