Question: Do you know of a platform that enables collective defense and anonymous collaboration among industrial organizations to share threat intelligence and combat cyber threats?
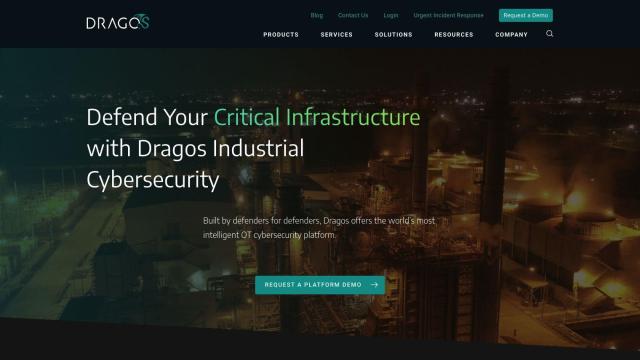
Dragos
If you're looking for a platform that enables collective defense and anonymous collaboration among industrial organizations to share threat intelligence and fight cyber attacks, Dragos is a good example of a full-featured solution. It offers a range of tools to monitor OT environments, assess vulnerabilities and respond to cybersecurity attacks. With OT cyber threat intelligence and collective defense, it's geared for industries like manufacturing, oil and gas and transportation, with features like detailed asset visibility, risk-based vulnerability management and threat hunting through proprietary threat intelligence.


Flashpoint
Another good option is Flashpoint, a powerful cyber threat intelligence platform that offers current and accurate threat intelligence. It's designed for use by a variety of teams including CTI/SOC, Fraud Teams and Corporate Security, so organizations can spot and respond to a broad range of threats. Flashpoint combines human sourced data collection and expert analysis with machine learning and proprietary collections engines, and offers customizable intelligence to support security teams.
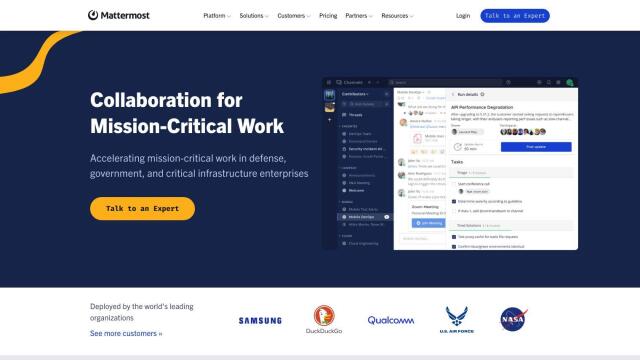
Mattermost
For collaborative defense, Mattermost is a secure collaboration platform geared for defense, government and critical infrastructure companies. It's got built-in security operations, incident response and real-time DevSecOps. Mattermost has robust security with deployment options in on-premises, air-gapped, private cloud and public cloud environments, so it can be customized and adapted to whatever environment is needed.


Recorded Future
Last, Recorded Future is a threat intelligence platform that helps customers assess and mitigate risk across multiple domains. It offers real-time intelligence through its Intelligence Graph, which ingests and processes data from a variety of sources. The platform offers ransomware mitigation, automated security workflows and supply chain risk mitigation, and is designed to help customers integrate intelligence into security operations.