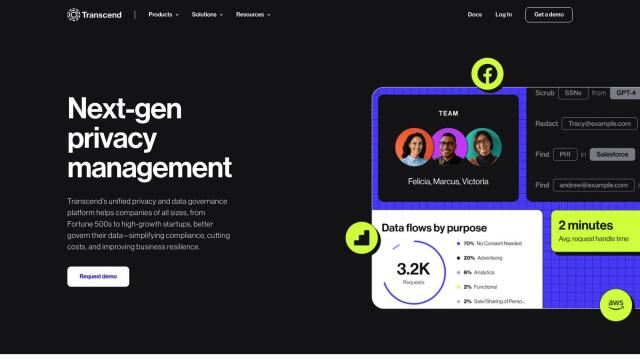
Question: Looking for a unified interface to manage user access and meet enterprise compliance requirements in a cloud-based environment.


BeyondTrust
BeyondTrust offers an intelligent identity and access security platform that offers a 360-degree view of all identities, privileges and access. It integrates with many tools and systems to help you take a zero-trust approach and offer dynamic access. The platform spans many use cases, including cloud access, cloud security, compliance and identity threat detection and response.


RSA
For a more security-focused identity solution, check out RSA. The RSA Unified Identity Platform includes automated identity intelligence, authentication, access, governance and lifecycle features. It supports multiple secure authentication methods and offers single sign-on, self-service and unified directory features. RSA can be used in cloud-only, hybrid and on-premises environments, so it's good for many industries.


CyberArk
Another strong contender is CyberArk, which offers secure access to any device, anywhere, with artificial intelligence technology. CyberArk protects every identity, human or machine, with secure Single Sign-On, Adaptive Multi-Factor Authentication and lifecycle management. It works with a broad range of industries and has flexible pricing, so it's a good choice for companies trying to move to a Zero Trust model.