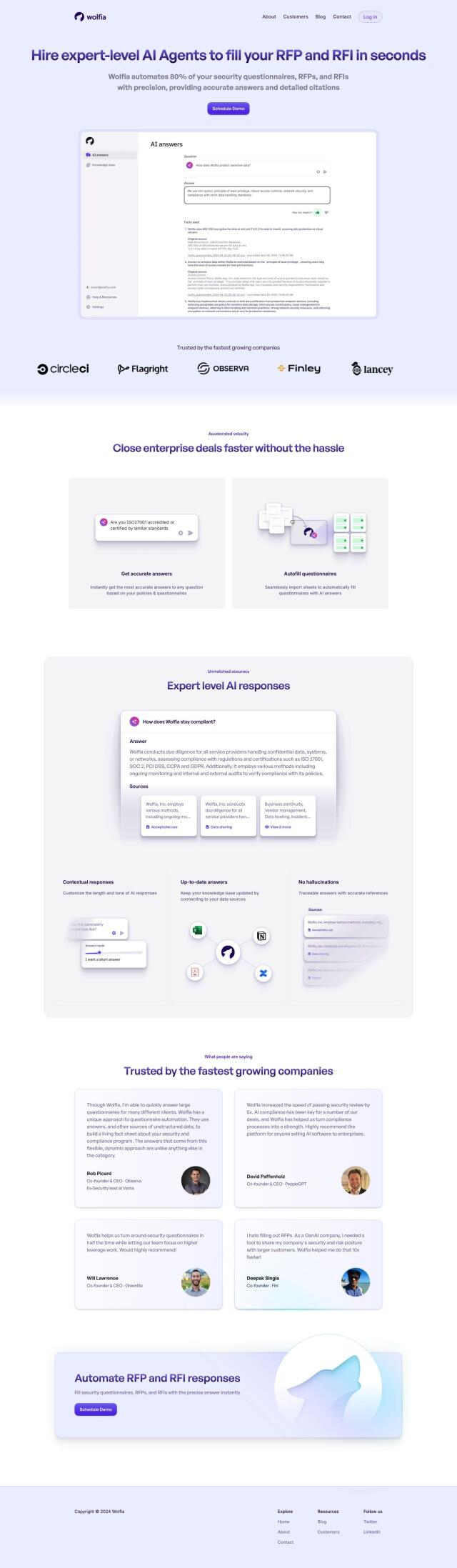
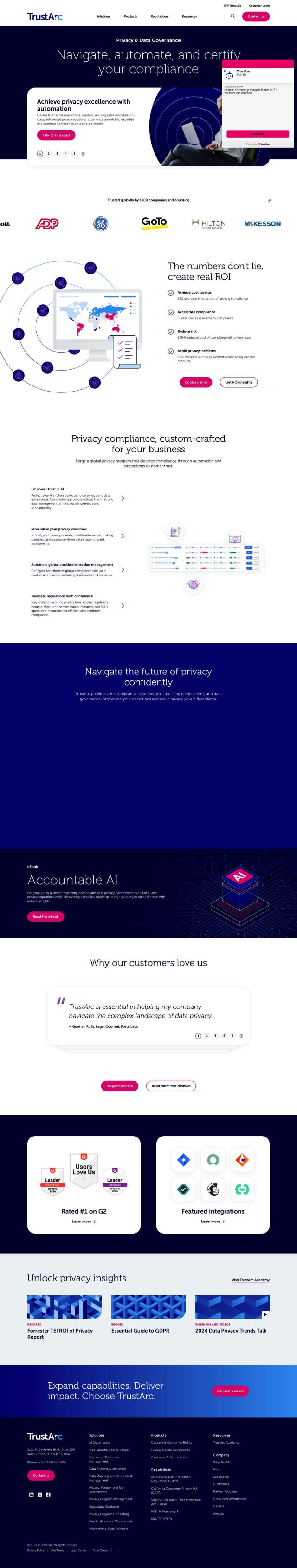
Question: Is there a platform that helps companies build trust with customers by making security reviews easy and frictionless, while also improving their overall security posture?
SafeBase
If you want a platform to help you establish trust with customers by making security assessments easy and painless, SafeBase is a good option. Its Trust Center Platform offers automated security assessments, CRM integration with Salesforce and HubSpot, and a custom rules engine. It also offers advanced analytics and visibility into your security program and customer access, and integrates with tools like Slack, Jira and StatusPage for workflow orchestration.


Whistic
Another good option is Whistic, which is geared specifically toward automating vendor assessments and making the process easier. It offers a centralized Trust Center, a Network Exchange for efficient information sharing, and AI integration to automate tasks. Whistic offers access to more than 40 questionnaires and frameworks, including rapid-response templates, and offers a single view of your supply chain to help you proactively mitigate risks.


Bitsight
For a more complete approach, Bitsight offers a more extensive cyber risk management platform. It includes tools for external attack surface management, cybersecurity analytics, security ratings, and compliance support. The platform helps organizations gain visibility, streamline risk management and ensure compliance, so they can better manage cyber risk and improve their overall security posture.
Secureframe
Finally, Secureframe automates and simplifies compliance work, covering a wide range of frameworks like SOC 2, ISO 27001 and GDPR. By automating evidence collection and offering continuous risk management, Secureframe speeds up sales by showing compliance, helping companies of all sizes improve their security posture and establish trust with customers.