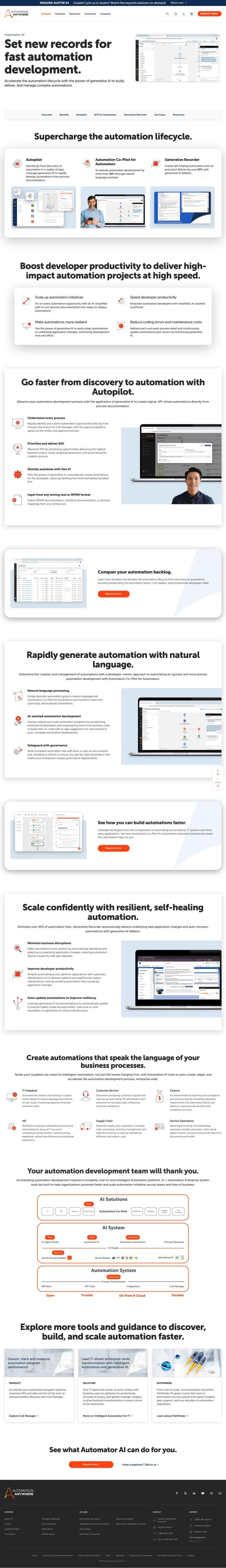
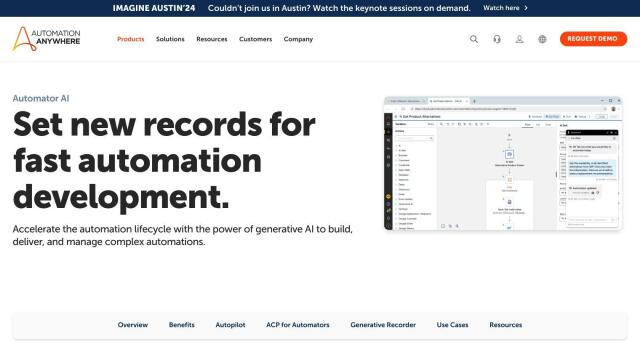
Question: Is there a way to automate compliance workloads and simplify IT operations for secure device access?
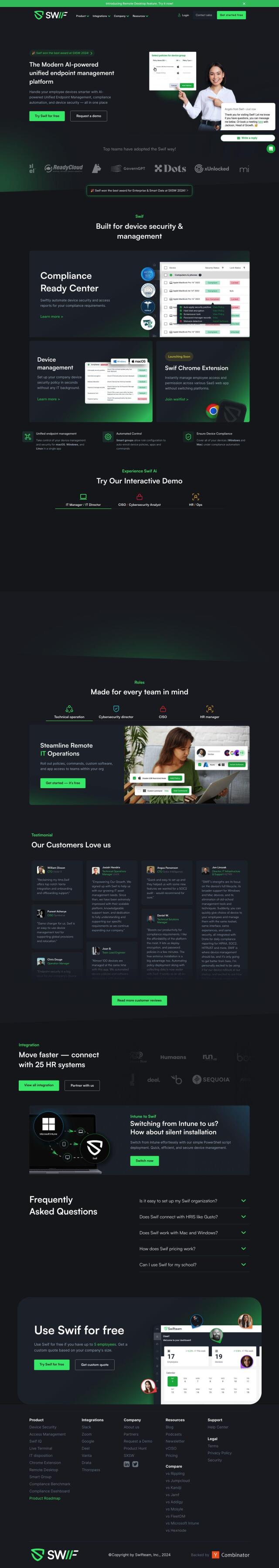
Swif
If you want to automate compliance tasks and make IT life easier for secure device access, Swif is a GenAI-powered platform that can help. It's a unified device management and compliance automation tool that includes tools to automate security and access reports, set up company security policies, and manage employee permissions to SaaS web apps through a Chrome extension. It also supports macOS, Windows and Linux devices with features like smart groups for automated control and compliance automation. And it integrates with tools like Slack, Zoom, Google and Vanta, so it's a good option for many teams.
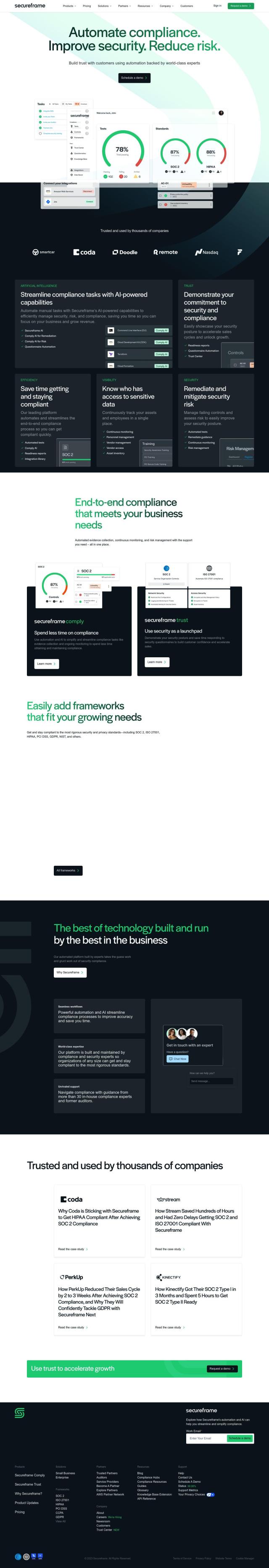
Secureframe
Another good option is Secureframe, which is geared specifically for automating compliance work and making the compliance process easier. It supports a variety of compliance frameworks including SOC 2, ISO 27001, HIPAA, PCI DSS, GDPR and NIST. The platform includes automated evidence collection, continuous risk management and workflow automation. Secureframe also includes expert guidance from a team of compliance experts, which can be helpful for companies trying to get their security house in order and prove compliance to customers.
Drata
If you're looking for a more comprehensive compliance automation platform, Drata offers a broad set of tools to manage Governance, Risk, and Compliance (GRC) programs. It supports multiple frameworks including SOC 2, HIPAA, GDPR, and has adaptive automation and continuous control monitoring. Among its features are automated evidence collection, 140+ native integrations, and process management with task creation and role-based access control. Drata is good for companies at any stage of their compliance journey, but particularly for those that need to maintain compliance across multiple frameworks at the same time.


CyberArk
Last, CyberArk is an identity security and access management solution. It offers secure access to any device anywhere, at any time, with AI-driven CyberArk CORA AI. The platform includes features like secure Single Sign-On, Adaptive Multi-Factor Authentication, and lifecycle management. CyberArk serves a broad range of industries and offers flexible pricing options, integrating with over 300 systems and services. It helps organizations protect their identity security posture and adopt a Zero Trust approach.