Question: I need a solution that automates access management for remote systems and databases to improve engineering velocity.


CyberArk
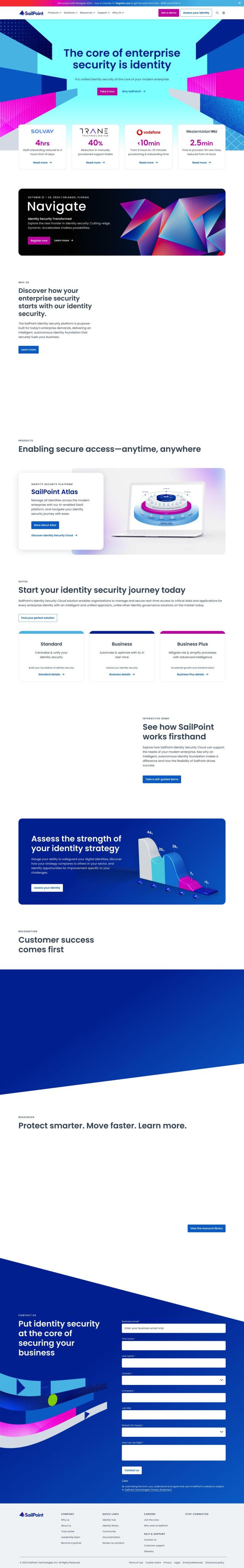
If you want to automate access management for remote systems and databases to accelerate engineering velocity, CyberArk is a good all-purpose solution. CyberArk offers secure access to any device with AI-powered identity security and adaptive multi-factor authentication. It also offers lifecycle management, directory services, and user behavior analytics to ensure strong access control and a strong identity security posture.


BeyondTrust
Another good option is BeyondTrust. The platform offers a 360-degree view of identities and privileges, including secure remote access, identity threat detection and dynamic access management. It can integrate with many tools and systems for a zero-trust approach and intelligent threat detection, a useful feature for organizations moving to a least privilege model.


Hoop
If you're looking for something more focused, check out Hoop. Hoop automates remote access and database connections with AI-powered data masking and just-in-time access. It integrates with Slack and offers features like session recording, webhooks for custom analytics and threat detection, making it a good option for accelerating security and engineering workflows.


Delinea
Last, Delinea offers intelligent authorization and identity security features like real-time centralized authorization and privileged access management. It also offers tools for securing secrets, governing service accounts and managing secure remote access, which can help reduce deployment and management time and resources for your identity security needs.