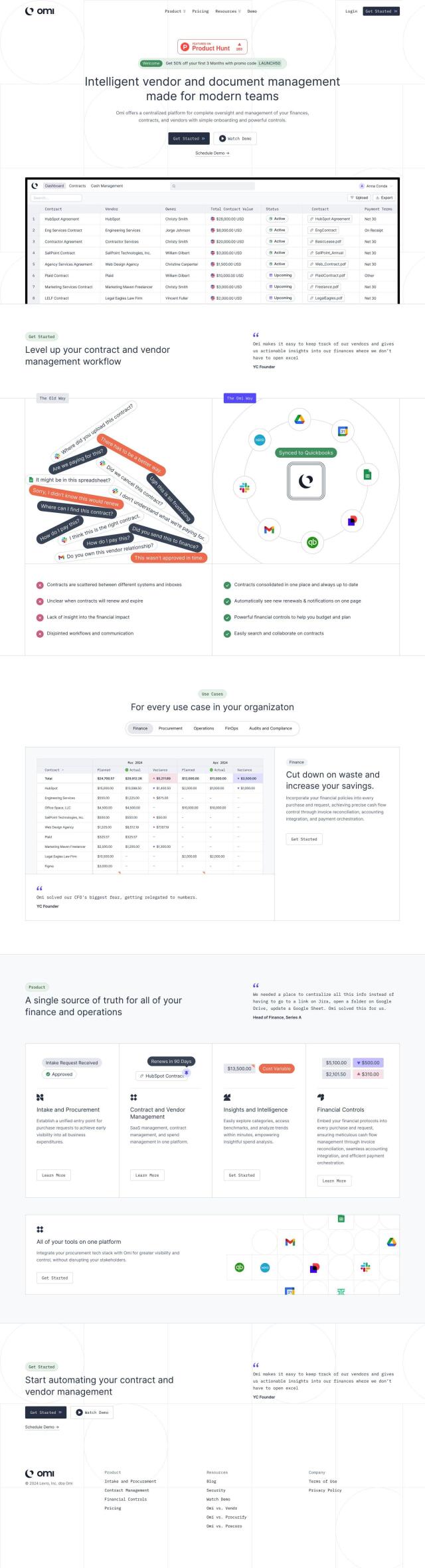
ProcessUnity
If you're looking for a Venminder alternative, ProcessUnity is another option. It's a broad third-party risk and cybersecurity risk management platform that automates the entire risk management lifecycle from onboarding to continuous monitoring. Its features include customizable workflows for TPRM automation, a Universal Data Core for risk data consolidation, and AI-powered tools for third-party risk. ProcessUnity is highly customizable and integrates with enterprise systems, making it a flexible option for managing third-party risk.


Prevalent
Another option is Prevalent, which uses AI and automation to assess and mitigate security risks from vendors and suppliers. It offers a single view of risk assessment and monitoring, covering a range of use cases including IT vendor risk management and supplier risk management. Prevalent offers due diligence collection and analysis, contextual risk reporting, and risk remediation, so it can be a good option for risk management teams in industries like finance and healthcare.


Panorays
Panorays is another option. The platform gives each third-party connection a real-time Risk DNA rating, which can trigger auto-adaptive security controls to steer each relationship toward the best possible security posture. It offers continuous supply chain detection and monitoring, actionable threat alerts, and AI-powered risk assessments. Panorays is designed to simplify third-party questionnaires and improve overall cybersecurity posture, so it's a good option for companies trying to optimize third-party risk management and cybersecurity.


Whistic
If you want to simplify the assessment process, Whistic offers an AI-powered platform to automate vendor assessments. It includes a centralized Trust Center for security and compliance documentation, a Network Exchange for efficient information sharing, and more than 40 questionnaires and frameworks. Whistic is designed to minimize the risk of breaches and free up InfoSec staff, so it's a good option for companies trying to modernize their third-party risk assessment process.